The Hidden Agenda of Third-Party App Stores

By Simon Lewis
Updated:

Many cell phone users are unaware that there are other app stores outside of the official Apple App Store or Google Play Store. However, in reality there are more than 300 operational stores worldwide, with that number continuing to grow. For example, one third party store, Aptoide, has reportedly had over 7bn downloads from its platform.
While you may feel that the number of apps on the official stores are more than sufficient – Apple for example offers in excess of 2 million apps on their App Store – there are a huge array of extra games and services available on unofficial third-party stores, as well as different versions of the apps you know and love. In this article, we ask should we be using these alternative app stores? And are they safe?
Why would someone want to visit a third-party app store?
There are a number of reasons why someone might want to visit a third-party app store.
As mentioned above, these stores can offer different services that are not available through official channels. They could be tweaked versions of popular apps that boast extended functionality and customization options, as well as free versions of apps you would generally have to pay for. They can also offer apps outside the regions they are normally available, and older versions of certain apps that users may want if they are running older devices or software.
So, what’s not to love? All that sounds great right? The only snag is that these app stores aren’t subject to the rigorous approval process of the official services. This means that they can serve as a route for developers to publish apps that have been removed from, or are not allowed on, the official stores.
There are plenty of concerns that have been raised over the security of these third-party stores, with many people seeing them as hotbeds of criminality. Whether these are a security risk depends on which store you look at. There are some that host apps containing malware and spyware while others are genuine and simply trying to widen the market and offer a legitimate alternative to the big tech giants.
Why would a developer host their app on a third-party site?
Developing apps costs money and time for those doing the work. So why would someone take their product to an unregulated third-party store and give it away for free? The answer to this is most likely not pure altruism.
Here are some reasons why they may go to the darker side of app stores:
- Higher ad volume and so higher ad revenue. There is a limit on the number of ads allowed on apps provided through the Apple and Google official app stores. Third party outlets typically allow a higher volume of ads and are less concerned about the general look and feel of their platform. This means app developers can earn more per user for their apps. These ads can be more intrusive and persistent than is allowed on official app stores. See examples further down.
- Sell your data – apps are able to mine a lot of data from your device including location data, device details (model, software versions etc.) and anything else you give permission for. Often, we don’t realise just how much we’re giving away when downloading an app.
- The worst-case scenario is that these apps include malware that will steal your personal information for criminal purposes.
However, there can be legitimate reasons for hosting apps on non-official app stores, such as:
- Hosting apps for free: Apple and Google charge a yearly subscription fee to host an app on their official stores. Many third-party alternatives do not do this, and so developers can test the popularity of apps without spending the money.
- Overcrowding: The Apple App Store is home to over 2 million apps, so anything new can easily just get lost. Developers have more chances to rank their apps higher on alternative stores.
- Third-party app stores often charge lower commission rates for in-app purchases when compared to Google and Apple.
Third party App stores do have their place. Unfortunately, while you may be able to fake your follower count or avoid paying a few dollars for an app, it all comes at a much higher cost to users’ security. We decided to delve into over 100 apps available on third party app stores and analyze their behaviour. We assessed how they interacted with the user’s device and tracked where they were sending data in order to find out if they were safe, or if they could be compromising user privacy in any way.
Here is what we did
- We installed the app on a number of test devices across iOS and Android.
- We visually observed app behaviour and compared to the genuine version if relevant.
- We monitored changes made to the device and what data the app could access.
- We recorded and analyzed the data sent to and from the app over the Internet. We did this to determine if any data that wasn’t relevant to the app use was being leaked out of the device and whether any malicious code was being downloaded.
After analyzing the apps, we recorded notable findings from some of the most popular, which are detailed below:
TikTok ++ (iOS)
What is it? A tweaked iOS version of the TikTok app.
The pros:
This version offers additional features not available in the official version, including:
- Downloading all videos
- Spoof or fake Following, Fan and Hearts stats
- Remove TikTok ads
The cons:
Ads: Whilst TikTok ads are removed by some versions of the tweaked TikTok ++ app, these are replaced by intrusive full screen ads that have been added by either the developers or the third-party app store. We found that these ads often contained false or misleading information. One example stated “50 viruses detected on your iPhone” which we know was untrue. This is a common tactic used by less genuine advertisers and developers to scare users and increase the number of clicks on an ad.
Malware: During analysis of the internet traffic capture we identified several encrypted calls to https://tharbadir.com/9 and https://tharbadir.com/11, which are behind the IP address 139.45.195.38. Further analysis revealed that these URLs and IP addresses had been flagged by several virus detection engines as being associated with malware. We also uncovered a prior WhatsApp phishing scam associated with these URLs.
While we were unable to determine the exact nature of TikTok++’s relationship and interactions with this malicious domain, the fact the link exists at all is cause for concern.
We also observed that the TikTok++ app sends certain device information to ‘data.flurry.com’. This data includes device model, time zone, disk/memory usage, language, screen width/height and advertising identifier. The official TikTok app that we analyzed has no link with this domain at all. Unfortunately, it was impossible to determine how this data is being used by Flurry.com or how they might be sharing it.
Zestia Step app store (iOS)
What is it? Zestia is a third-party app store in its own right, but in order to use it you must first download their app Zestia Step. This is quite a common practice and most of the third-party app stores require you to download their app first in order to browse the store. We decided to analyze this app to see if there was any risk associated with apps provided by third party app stores themselves and not just the apps that are made available on these stores.
The pros:
Zestia is well known as the place to go if you are looking for cracked apps and tweaked versions of well-known apps like Instagram and Kik.
The cons:
Ads: The Zestia Step app has very aggressive ads and popups. As soon as you open the app you are presented with a full screen popup, which is very difficult to close or move on from. Although these are technically adverts, they are designed to look like iOS warnings or genuine features, in order to trick the user into taking some sort of action, such as downloading or paying for another app/service.
One of the worst examples of this is a persistent popup that opens the door for software that can take over the user’s calendar and bombard them with spam and fake warnings every hour. The popup presents itself as a video player, which brings up an iOS notification that asks the user to subscribe in order to watch the video. If the user taps cancel the notification disappears but tapping anywhere on the screen repeatedly triggers the popup to reappear. This makes it impossible to move on without subscribing. If the user does subscribe, their calendar is filled with fake events that are disguised to look like iOS warnings, claiming that the device is infected with a virus or malware and that the user will need to pay to fix it.

Another example that we saw is a full-page ad designed to look like a legitimate iOS security warning. The ad states that the user’s device has been infected with viruses and that they must install another app to fix it. These adverts are incredibly misleading as it is impossible for an advert, or indeed any iOS app, to tell if your iPhone has a virus. As with the above example, the ad makes it impossible to move on without the user tapping the OK to be taken to the download page for another app.
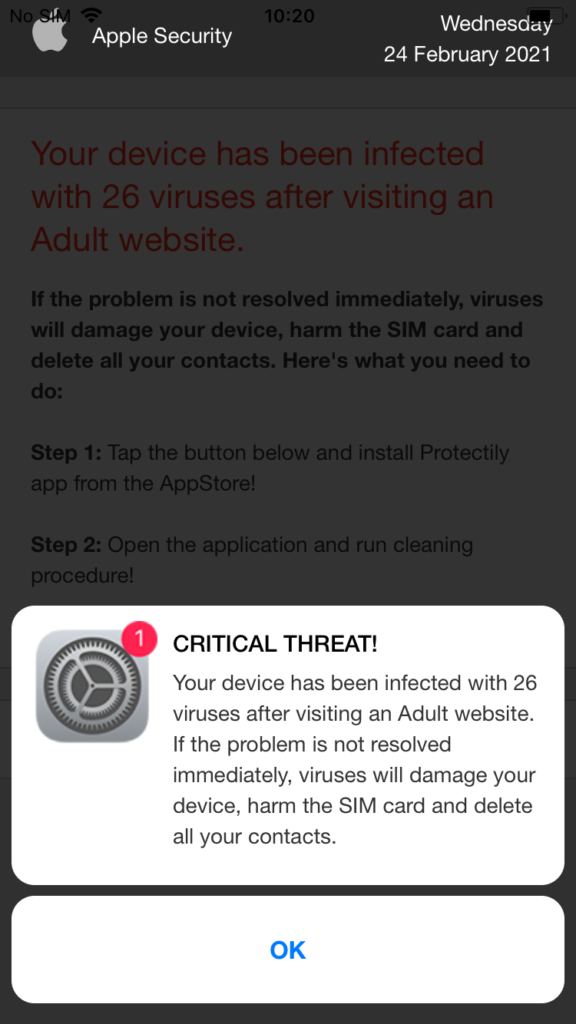
Malware: While the Zestia Step app was running on our test device it tried to contact a number of domains that are known to be associated with fraud, phishing, malvertising and riskware. These included:
- www.hicpm10.com
- Tours-78-94.wellhello.com
- Load09.biz
- ridedical-riseats.com
Instagram Plus (Android)
What is it? The tweaked version of the Instagram app.
The pros:
This version offers various additional features that are not available in the official app. Including:
- The option to download photos and videos
- The option to download Stories and Live Streams
- You can hide your name when you view someone else’s story
The cons:
Accessing your personal information: As a security feature of the Android System, apps have to define the device features they need to access in order to function. For example, a voice recording app would need to access your microphone to work, or a mapping app would need to access your location data.
We analyzed the real Instagram app and compared its device features to a version of Instagram Plus from an alternative third-party app store. We found some notable differences, including Instagram Plus specifying the permission ‘RECEIVE_SMS’, whereas the real Instagram app did not. If this permission is granted by the user then the app would have the ability to read all incoming SMS messages on the device. We were unable to determine how this permission was being used on the device, but someone with malicious intent could use this permission to spy on a device to intercept things like two factor authentication codes and password reset links.
Malware: While installed on our test devices Instagram Plus communicated with a number of blacklisted IP addresses. Specifically, the IP addresses 157.240.20.35 & 179.60.195.36, which are known to be associated with malware.
Clash of Clans (Android)
What is it? This is a popular game app, which, when downloaded from a third-party store, ostensibly looks exactly the same as the official version obtained through the Google Play Store. However, when we compared the two apps, we found that there was a difference.
The pros:
It’s a fun game that does exactly what it says on the tin.
The cons:
Accessing your personal information: The third-party app store version of the app states that it requires access to the permission ‘READ_PHONE_STATE’. This is not required by the official version.
Applications that have been given access to this device feature have “read only” access to phone state. This includes the current cellular network information, the status of any ongoing calls, and a list of any Phone Accounts registered on the device.
While we were unable to determine if or how this permission is being exploited, it is obviously not something that is central to the running of the app itself. Which begs the question of why the app may require access to this device feature?
Final thoughts…
While apps from third-party stores add a degree of customization and flexibility, our findings suggest that they should be used with caution. Without careful research, you could be compromising your online security and giving away more than you would think.