How to Detect Spyware on an iPhone

By Simon Lewis
Updated:

Last year, Apple published two security reports that detailed vulnerabilities that might let hackers seize control of iOS devices. While Apple promptly rolled out updates to address these issues, users are still concerned about their phone’s security and the protection of their personal data.
Unfortunately, it’s not just expert hackers who are able to develop iPhone viruses to exploit these vulnerabilities. Today’s digital era has given bad actors easy access to affordable software and how-to guides that can be used to install spyware on iPhones. This spyware could expose everything from your personal messages to your financial information.
If you think your iPhone may be compromised, you need to act—and fast. Here’s our guide to detect and remove spyware from your iPhone.
Table of Contents
- How to Detect Spyware on iPhone
- Detect and Remove Spyware with Certo AntiSpy
- How to Protect Your iPhone against Hackers
- Why Would Someone Hack Your iPhone?
- Who Can Put Spyware Software on Your iPhone?
- How Easy Is It for Hackers to Spy on Your iPhone?
- Types of iPhone Spyware
- Frequently Asked Questions (FAQs)
Award-winning spyware detection
Combat spyware and other cyber threats with Certo AntiSpy, the world's leading anti-spyware tool for iPhones.
How to Detect Spyware on iPhones
Despite their stellar reputation for having robust security features, iPhones aren’t exempt from spyware programs. Wondering whether you might have spyware on your iPhone? Here are some ways to tell:
🔺 Unknown or suspicious apps
We’ve all been there—sifting through our devices, stumbling across unknown apps and thinking, “When did I download these?” Most of the time, a forgotten app is just that. But sometimes, the reason you’re finding unknown apps can be more sinister.
When unknown apps surface on your iPhone, it’s not always a case of forgetfulness. Some spyware disguises itself as legitimate-looking apps that sneak past our defenses.
Here are some examples of suspicious apps to look out for:
- Jailbreak-related apps such as “Cydia”, “Sileo” and “Checkra1n”
- Known fake system apps like “SystemCore” and “SystemUpdate”
- Apps with names like “Phone Monitor”
If you encounter a suspicious app that you don’t recall downloading—especially if it isn’t one of Apple’s default apps or downloaded from the official App Store—it could very well point to spyware lurking beneath the surface.
🔺 Increased data usage
Data usage naturally ebbs and flows based on our online activities, but when you observe a sudden surge, there might be more at play than just excessive video streaming.
Spyware often works by collecting data from your device and secretly transmitting it to an external server. This under-the-radar operation can cause a suspicious spike in your data consumption.
Track your mobile data usage over a couple of days or weeks to get an idea of how much mobile data you typically use over a given period of time. If you notice a strange spike in usage, this may be a sign that your device has spyware installed.
🔺 Decreased battery life
While factors like age, battery health, and heavy app usage can contribute to battery depletion, an unexpected battery drain can point toward spyware programs working overtime in the background.
Because spyware is always running in the background to keep track of your activities, it can use up your battery life at an abnormal rate. If you’ve ruled out other factors that may be draining your battery, it’s time to investigate what might be going on behind the scenes.
🔺 Suspicious text messages
Everyone receives a weird text message now and then; if it only happens once in a while it’s usually not cause for concern. But if you regularly receive such texts, it may be a reason to dig a little deeper. Spyware and phishing messages often go hand-in-hand, and these text messages could be an indication that your phone has been targeted.

Detect and Remove Spyware with Certo AntiSpy
By now, you may be wondering whether you have iOS spying software on your device. Whether it was through a suspicious app, a malicious link, or a more targeted attack, there are countless ways iOS devices may become infected with spyware—and there’s one surefire way to find and remove it.
If you’re concerned about your iPhone’s security, the easiest way to detect and remove spyware is with Certo AntiSpy. This industry-leading software finds threats, then removes them in a few clicks. In addition, you can use it to run system checks, analyze your operating system, and review app permissions to identify vulnerabilities.
Certo AntiSpy takes a unique approach to threat detection on iPhones, meaning it can detect more threats than any other iPhone security solution.
Here’s why Certo AntiSpy is ideal for keeping your iPhone secure:
- Find and block spyware, suspicious apps, keyloggers, and more
- Remove suspicious apps and files
- Unique, deep scanning method finds threats that other apps cannot
- Award-winning and trusted by over 100,000 users
Watch the video below to see how Certo AntiSpy scans your iPhone and removes spyware in just a few minutes.
How to Protect Your iPhone against Hackers
While Certo AntiSpy is a fast and reliable way to remove spyware from your iPhone, this doesn’t mean your device will be safe from malicious software forever—unless you continuously take steps to protect it.
Fortunately, there are various ways you can boost your device’s defenses. Let’s dive into how to safeguard your iPhone effectively:
🟢 Detect and remove spyware
If your iPhone is infected with spyware then your messages, calls, photos and other private information could be exposed.
Regularly scan your device for iPhone spyware and malicious software. Not sure how to do this? Certo AntiSpy makes it easier than ever to detect and remove spyware, and keep your phone protected going forward.
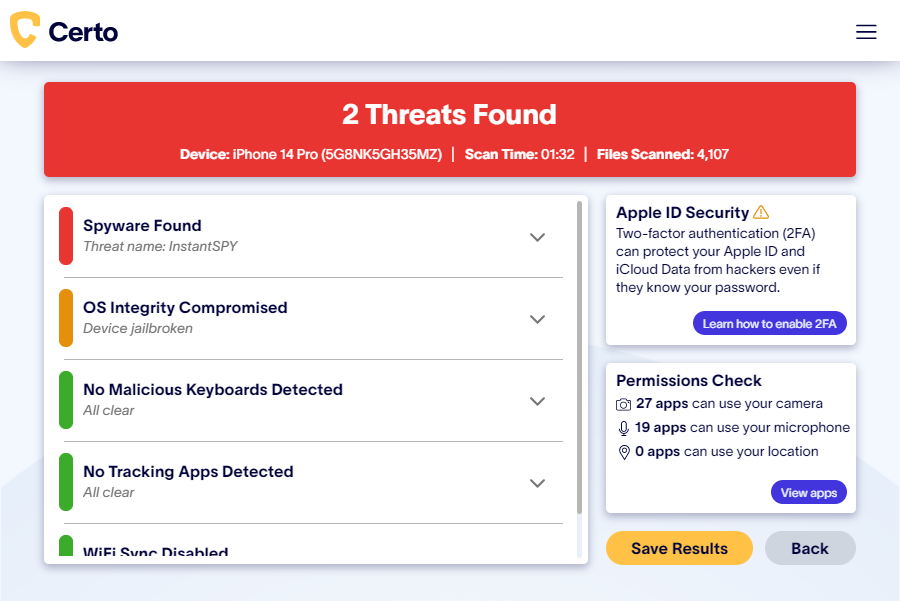
Fig 1. Results of a spyware scan with Certo AntiSpy.
🟢 Update your iOS to the latest version
As technology changes, so do our operating systems. If your device’s operating system is outdated, you could be vulnerable to spyware attacks. Here’s how to check whether a software update for iOS is available on your device:
- Tap on the Settings app from your home screen
- Scroll down and select the General option
- Tap on Software Update. Your device will check for updates
- If an update is available, you’ll see its version number and description
- If you wish to proceed with the update, tap Download and Install

Fig 2. Updating the iOS version on iPhone.
🟢 Update your apps
Just like you should ensure your iOS is up-to-date, it’s equally important to keep all your installed apps current. Developers regularly release security patches, so staying updated is one of your primary defenses against potential vulnerabilities.
Go through your app folders, and if you have any unknown or suspicious apps installed, delete them and run a spyware check.
🟢 Use a strong passcode
Most iPhone spyware requires the hacker to physically get hold of your device to install it. Therefore, a strong unlock passcode that’s difficult to guess can be one of the best ways to protect against a spyware attack.
Use a combination of uppercase and lowercase letters, numbers, and special symbols, and don’t base your passcode on publicly available information, like your birthday.
🟢 Use two-factor authentication
Some iPhone spyware works by accessing your iCloud account and stealing data that’s been synced from your phone, such as photos and messages. Therefore using two-factor authentication with your Apple ID is another important way to protect your iPhone from hackers.
Two-factor authentication (2FA) is a security feature that enhances the safety of your accounts beyond just a password. Even if cybercriminals decipher your password, 2FA prevents them from breaking into your account.
To access your account with 2FA, you’ll need to present two distinct forms of identification. This typically combines something you’re aware of (such as your password) with something you receive and input (for instance, a code produced by an application or a single-use password delivered through SMS or email).
🟢 Don’t open suspicious links
Clicking on suspicious links or attachments can give surveillance software, spyware, and malware direct access to your device.
Don’t click on links in emails or texts from contacts you don’t recognize and be careful about clicking on unknown links while browsing the internet.
🟢 Enable Lockdown mode
Lockdown mode is an optional, extreme protection measure that can be turned on to help combat some targeted and sophisticated cyberattacks, such as Pegasus.
When enabled, your device will function differently. Some apps, websites and features will be limited and some experiences will be completely unavailable.
While this isn’t going to protect against all methods of hacking, it can be a way to protect against certain types of advanced spyware.
Lockdown mode can be enabled as follows:
- Open the Settings app.
- Tap Privacy & Security.
- Under Security, tap Lockdown Mode and tap Turn On Lockdown Mode.
- Tap Turn On Lockdown Mode.
- Tap Turn On & Restart, then enter your device passcode.
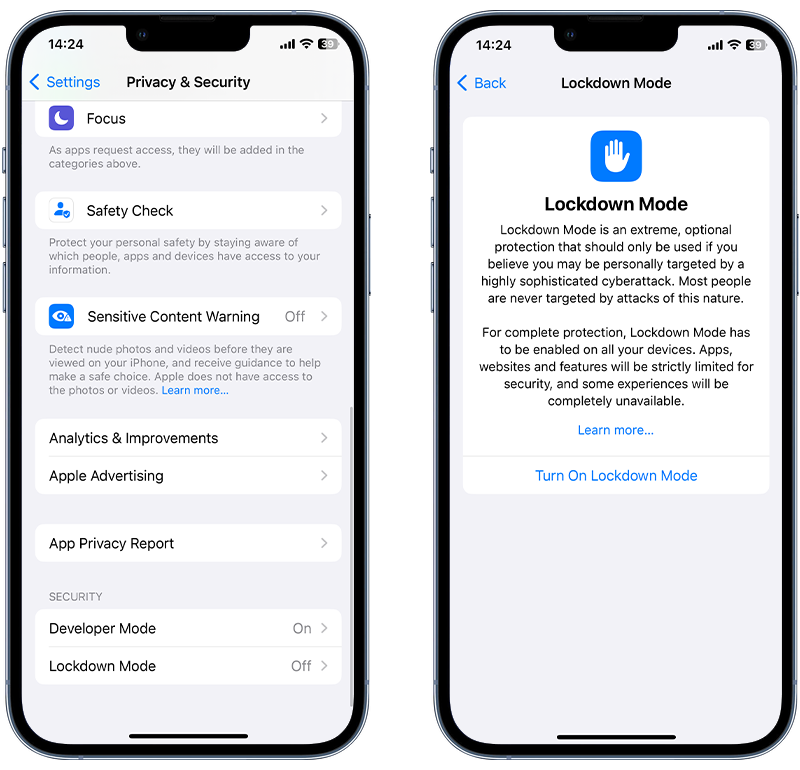
Fig 3. Enabling Lockdown Mode on iPhone.
Why Would Someone Hack Your iPhone?
There are many reasons someone might want to hack your phone. However, the most common reasons are to collect information about an aspect of your personal life or for monetary gain.
Here are a few examples that detail why someone would install malicious programs on your iPhone and how they could abuse your private data:
Cyberstalking
Cyberstalking is one of the most common uses of spyware apps and it is often carried out by someone close to you. Some examples of cyberstalking are:
- Accessing private text messages for use in divorce proceedings
- Monitoring of GPS locations by a jealous spouse or partner
- Accessing your iPhone remotely
- Installing surveillance software on your iPhone
Identity theft
Once they have access to your personal information, a hacker could steal your identity. They might use your details to open new bank accounts, take out loans, or worse.
This has the potential to completely ruin your life and leave you with a mountain of debt that you weren’t responsible for—or at the very least, cause a huge amount of stress and waste a lot of your time.
Financial fraud
If a hacker manages to steal information related to your finances, it’s common for them to purchase items online by using your information. They could also request money from your contacts or withdraw funds from your bank accounts.
Data theft
Hackers can make fast money by collecting data from multiple victims and then selling the information to others. Full ID packages can sell for amounts of up to $100 each on the dark web, and hackers will usually sell this data in large batches.
Blackmail
Hackers could use the data they’ve stolen to blackmail you. This tactic usually involves them threatening to share your personal photos, videos, or text messages with your contacts, unless you send them money.
Uncover spyware with Certo AntiSpy
If you're concerned that someone may have installed spyware on your iPhone then run a quick scan with the award-winning Certo AntiSpy.
Our industry-leading spyware detection tool finds threats that are undetectable by more traditional security apps.
Who Can Put Spyware Software on Your iPhone?
A hacker could be anyone. They might be a jealous spouse or a nosy employer, or even a complete stranger such as a professional hacker, stalker, or fraudster. It’s impossible to tell—especially since spyware is readily available and easy to use.
Most people, however, are far more likely to be hacked by someone they know, with one survey suggesting that 50% of Americans had accessed their partner’s phone without their knowledge.
It’s also worth noting that if you have access to valuable data or are a high-profile individual, then you may be more at risk of being hacked by a professional.
How Easy Is It for Hackers to Spy on Your iPhone?
Contrary to what many people think, anyone can become a hacker with the right tools. Unfortunately, the spyware needed to hack an iPhone is cheap to purchase; hackers can get access to them from as little as $30 per month.
Hacking is no longer reserved for experts. These days, anyone who can use an iPhone is capable of installing data-stealing spyware. All they need is access to your phone for a few minutes to download spying software onto your device.
Types of iPhone Spyware
Hidden spy apps
Hidden spy apps are the most commonly used type of iPhone spyware.
They are designed to remain hidden on your iPhone and give hackers access to huge chunks of personal data, including instant messages, emails, real-time location, photos, and more.
This type of spyware program requires the hacker to have physical access to the victim’s device for a few minutes to install it. Once installed, the hacker can then remotely monitor all activity on the infected device. In some cases, they may even be able to turn on the microphone and camera to listen and watch remotely.
iCloud attack
An alternative method available to hackers who want to steal data from iPhones are iCloud spyware attacks. This is when a hacker targets the data synced from your phone and held in your iCloud account, as opposed to targeting your physical device.
This type of attack doesn’t require access to the device, but does require the hacker to have the victim’s Apple ID login details. And because it is carried out via the internet, it is almost impossible to detect.
Fortunately, it’s quite easy to protect yourself against such an attack by enabling two-factor authentication with your Apple ID. This type of authentication requires two pieces of information to access your account, for example, your Apple passcode and a six-digit code sent to one of your trusted devices, which make it much more difficult for hackers to gain access.
Rogue enterprise apps
This type of hack relies on bypassing the App Store’s strict security measures by installing suspicious apps in a different way. It uses a method usually reserved for app developers and for larger corporations that need their own custom apps.
This method allows hackers to install malicious apps onto your phone that have not been approved by Apple. Rogue enterprise apps are not completely invisible, but hackers often give these apps innocent-sounding names or hide them in a utilities folder so they go unnoticed.
These apps are not as powerful or intrusive as a hidden spy app, but they are compatible with a wider range of devices and are often a preferred attack method due to how easily they can be installed.
Misusing legitimate apps
Pre-installed apps such as ‘Find my iPhone’ and ‘Google Maps’ can be misused by a hacker to track the victim’s location. This requires the hacker to gain access to the victim’s device for a short time.
A hacker can also change the logged-in account on the device’s web browser in order to collect browsing data history and account login details.
As no malicious apps or code are installed, it’s easy for this type of attack to go unnoticed for months or even years, during which time the hacker has gained a wealth of information.
Zero-day exploits
Zero-day exploits are somewhat rare, but they can be devastating to those affected. These attacks are usually carried out by hackers when they happen to discover a previously unknown weakness in operating systems or third-party apps.
Once a weakness has been exposed, it’s immediately exploited. If a zero-day attack is carried out on a popular app or device, it can affect millions of users. In some cases, more advanced exploits can even infect a device with malicious software completely remotely, without the hacker needing to touch the victim’s device.

Frequently Asked Questions (FAQs)
How does spyware get installed onto my iPhone?
Even though the iOS ecosystem is renowned for its security measures, spyware installation on an iPhone can occur through various means. Here are some common ways spyware can find its way onto your device:
- Jailbroken devices that have an outdated or compromised operating system
- Phishing attacks via malicious email, text messages, or social media
- Insecure public Wi-Fi networks
- Malicious apps that install spyware on an iPhone
- Physical access if someone knows your passcode
What are the risks of having spyware installed on my iPhone?
Given the amount of sensitive personal information stored on your iPhone, spyware can be a significant threat. Here are the primary risks associated with spyware on your iPhone:
- Personal data theft
- Financial loss
- Compromised privacy
- Location tracking
How do I remove spyware from an iPhone?
Removing spyware from your iPhone is easy with Certo AntiSpy. Here are five easy steps to protect your phone:
- Install Certo AntiSpy on your computer
- Use a USB cable to connect your phone to your computer
- Run the scan
- Certo AntiSpy will detect iPhone spyware
- Click Remove to erase any spyware from your iPhone
You can also perform a factory reset to wipe your device completely, along with the malicious app or folder. Remember, a factory reset means you will lose all your data, so this step should only be taken as a last resort.
How do I protect myself from spyware?
Protecting yourself from spyware requires a combination of best practices, software solutions, and vigilance. Here’s how to shield yourself from cyberthreats:
- Run regular system scans with Certo AntiSpy
- Ensure your iOS runs on the latest version
- Don’t install apps from third-party app stores
- Take extra care if you have a jailbroken iPhone
- Use a strong unlock passcode that only you know