What To Do If Your iPhone Has Been Hacked

Published:

In today’s hyper-connected world, iPhones aren’t just an accessory. They’re a vital lifeline that connects us to our families, jobs, and instant information. But what happens when they fall into the wrong hands?
Regardless of your phone’s operating system, anyone can be the target of online threats or have their phone compromised on an insecure network. If you believe your phone has been hacked, it’s important not to panic. Instead, it’s time to take swift and strategic action.
In this article, we’ll share a step-by-step guide that shows you what to do if you believe your iPhone has been hacked.
If you have an Android device you believe has been hacked, please read our blog on how to fix a hacked Android phone.
Fix a hacked iPhone
Get your privacy back. Detect and remove spyware and other cyber threats with the award-winning Certo AntiSpy.
Can an iPhone Be Hacked?
Apple has a reputation for its secure iOS, so you may think, “Isn’t my iPhone secure already?”
Unfortunately, no smartphone—be it an iPhone or Android device—is immune to hacking threats. While Apple designed its iPhones with multiple layers of security, they’re not invulnerable to malicious software and hacking attempts.
Both iPhones and Android devices can fall prey to breaches. Any device connected to the Internet can, in theory, be hacked. Some of the most common ways in which phones are hacked, include:
- Suspicious apps.
- Insecure public Wi-Fi networks.
- Phishing.
It’s important that you don’t rely solely on Apple for your data’s safety. Having strong mobile security habits can be instrumental in safeguarding your personal information and digital identity, no matter your phone type.
Why Would Cybercriminals Want to Hack My iPhone?

The digital age has brought us convenience, but it also comes with its own unique set of risks. If you’re a regular person with a typical job, you may think that hackers won’t be interested in your data—after all, you aren’t a celebrity or politician.
Unfortunately, this couldn’t be further from the truth. Regular people have their phones hacked daily, and statistics show that there is a hacker attack every 39 seconds. Whether they’re Android users or iPhone users doesn’t make any difference.
So, why might someone want to hack ordinary people’s iPhones or Android devices? There are countless motives, including:
🛑 Identity theft
Identity theft is one of the most common crimes in the digital realm. Cybercriminals want to gain your personal details to impersonate you and commit various forms of fraud.
After stealing an identity, a hacker can open credit lines, secure loans, or even orchestrate larger-scale frauds, all while impersonating the victim. Beyond serious financial ramifications, this can lead to social and professional consequences for the target.
🛑 Gain remote access
Spyware (malicious software designed to infiltrate devices) operates covertly. When hackers install spyware on smartphones or computers, their primary goal is continuous monitoring.
They can track users’ every move, listen to private conversations, and even gain insight into their personal habits and routines. Over time, this information can provide a comprehensive profile of the user and make them vulnerable to cyberthreats or manipulative schemes.
🛑 Financial data
Most people store a wealth of financial information on their devices—from bank account details to credit card information. For hackers, this data represents direct financial opportunities.
A hacked phone allows criminals to execute unauthorized transactions, siphon funds, or even commit large-scale financial fraud. In addition, once hackers have accessed this information, it can be sold on the dark web, and this makes the victim susceptible to continued financial breaches.
🛑 Your login credentials
Usernames and passwords are the keys to our digital lives. These credentials grant access to a range of online accounts, from personal emails to online banking and more.
Cybercriminals know that many people reuse passwords across platforms. So, if they can gain the login credentials for one service, they often gain access to others.
Stolen credentials can also be traded or sold on the dark web, where they can be used in coordinated attacks or identity theft.
10 Things to Do to Protect Your Hacked iPhone Immediately

Hacking can lead to unauthorized access to your personal information and compromise your privacy, so you must act quickly to stay safe. Here’s what you should do:
🟢 Disconnect from Wi-Fi & mobile data
The moment you suspect your iPhone has been hacked, disconnect from the internet. This step is essential because—in a hacking scenario—the attacker usually establishes and maintains access to your device through an active internet connection.
Of course, this step is not a permanent solution, but it will buy you some time to calm down and figure out your next move.
🟢 Change your iPhone lock screen passcode
Many hacks happen when someone has physical access to your device, so if you suspect your iPhone has been hacked in this way, it’s essential to prevent further unauthorized access.
Changing your iPhone unlock passcode to one that’s hard to guess and known only by you is the best way to do this. Here’s how:
- Open Settings.
- Tap Face ID & Passcode.
- Enter your current passcode.
- Scroll down and tap Change Passcode.
🟢 Change your Apple ID password
Many iPhone hacks work by gaining access to your Apple ID, so changing your Apple ID password is one of the first things you should do if you think your iPhone might have been hacked. This is a critical step to regain control over your account and minimize potential damage. Here’s how to change your password:
- Open Settings.
- Tap on your name at the top to access your Apple ID settings.
- Tap Password & Security.
- Tap Change Password to begin the password change process.
Enter a strong password for your Apple ID. A strong password should include a combination of upper and lower-case letters, numbers, and special characters. Don’t use easily guessable information or a slight tweak to your existing password.
🟢 Change your passwords for online accounts
If hackers have gained access to your iPhone, it’s vital that you take action—fast. While changing your Apple password is an excellent first step, you’ll also want to change the passwords across your online accounts.
Hackers know that many people use the same or similar password on various accounts, so if they know one password, it could lead to a domino effect with them taking control of all your accounts.
Make sure to use strong, unique passwords on each account, and consider using a password manager like NordPass to store your passwords securely.
🟢 Run your antivirus software
Despite their robust security features, iPhones are not completely invulnerable to being hacked.
Certo AntiSpy is a powerful antivirus tool custom-designed to help iPhone users find and remove these threats in a few easy steps.
Here’s how to use Certo AntiSpy to keep your iPhone safe and secure:
1. Download Certo AntiSpy. Download and install Certo AntiSpy antivirus software on your computer.
2. Plug your iPhone into your computer. Connect your iPhone to the computer where Certo AntiSpy is installed with a USB cable.
3. Run a scan. Once your iPhone is connected, open Certo AntiSpy and start the scan. The software will then analyze your iPhone and check for signs of malware, spy apps, and system vulnerabilities.
4. Remove any threats. Once you’ve run the scan, Certo AntiSpy will show you the results. Here, you can remove any suspicious files with the mere click of a button.
Stop hackers for good
Combat spyware and other cyber threats with Certo AntiSpy, the world's leading anti-spyware tool for iPhones.
🟢 Uninstall suspicious apps
Apps on your iPhone often request permission to access various features and data, such as your camera, microphone, location, contacts, and more.
These app permissions are granted when you first install the app or when the app requests access. Most people grant app permissions to their devices without thinking twice, but a malicious app can wreak havoc on your security and steal sensitive data.
Delete any apps you don’t remember downloading or apps you’ve downloaded from potentially malicious websites.
🟢 Update your iOS version
Having an up-to-date operating system becomes critical if you suspect that advanced spyware has been used to compromise your iPhone.
Jailbroken iPhones are particularly vulnerable, because the manufacturer’s software restrictions and latest security patches may be compromised.
In a world where technology moves so fast, keeping your iPhone updated is one of the easiest and most effective ways to protect yourself. Here’s how to check whether updates are available:
- Open Settings.
- Scroll down and tap on General.
- Tap on Software Update.
- If an update is available, you’ll see an option to Download and Install.
🟢 Enable two-factor authentication
Two-factor authentication (2FA) is a security mechanism that adds an extra layer of protection to your accounts—it goes beyond your password. If hackers have managed to figure out your password, 2FA will stop them from getting into your account.
2FA requires you to provide two different types of identification before you can access your account. This usually involves something you know (your password) and something you obtain and enter (like a verification code generated by an app or a one-time password sent to you via SMS or email).
🟢 Activate lockdown mode
Lockdown mode is a security feature that enhances your iPhone’s protection when privacy is crucial. When activated, it can block some advanced hacks by limiting certain features.
Like turning off your Wi-Fi, enabling lockdown mode isn’t a permanent solution, but it can buy you some time. Here’s how to activate lockdown mode:
- Open Settings.
- Tap Privacy & Security.
- Tap Lockdown Mode, then Turn On Lockdown Mode.
- Restart your iPhone and enter your passcode.
🟢 Factory reset your device
Doing a factory reset might feel drastic, but it’s an effective last resort that will completely wipe your device along with any malicious apps on it. If you want to factory reset your iPhone, approach the process methodically to ensure you don’t lose any irreplaceable data. Here’s how:
1. Backup your data. Once you’ve performed a factory reset, your iPhone data will be lost forever. Back up everything you want to keep, including photos, videos, contacts, messages, and passwords.
2. Perform a factory reset. Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings. This will reset your iPhone and return it to its factory state.
3. Set up your iPhone as a new device. After the factory reset, set up your iPhone as a new device. This means you won’t restore your phone from a backup; setting your phone up from scratch will prevent any remaining malicious software from being restored along with your backed-up contents.
Final Thoughts
If you think your phone has been hacked, you need game-changing antivirus software to protect your private data. Certo AntiSpy is a powerful and reliable option designed to find and remove spyware with a few simple clicks.
With Certo AntiSpy, you can quickly scan your phone for malicious apps and files, then remove any threats that might be lurking. Once you’ve restored your iPhone’s security, you can protect your phone from hackers time and again by continuing to run regular scans.
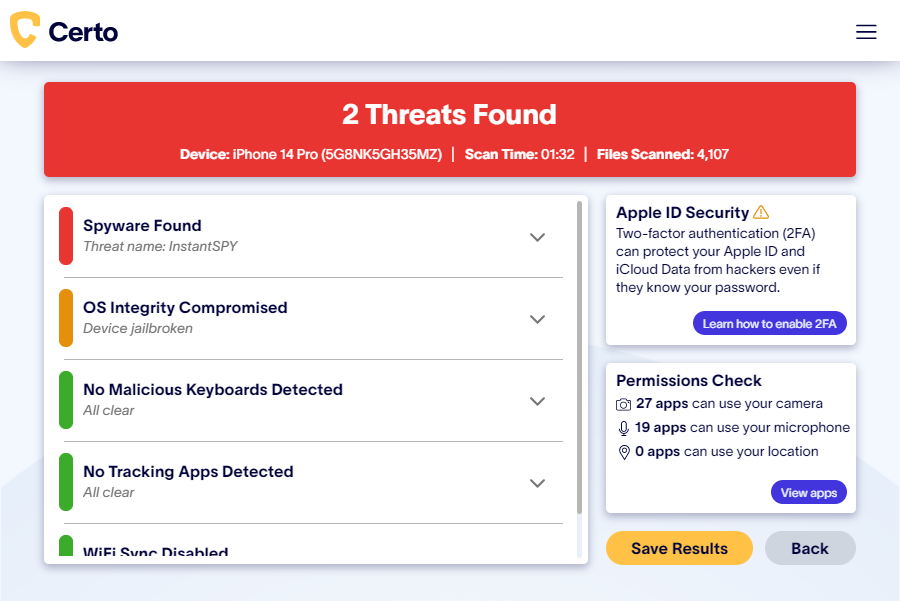
Fig 1: Certo AntiSpy scanning a hacked iPhone