The Banking Trojan Evading Detection on Android Devices

Published:

In an era where digital banking is intertwined with daily life, the emergence of sophisticated malware targeting financial transactions is a growing concern. A recent discovery by cybersecurity experts reveals a new threat to Android users, particularly those engaging with Latin American banks. Dubbed PixPirate, this banking trojan has been ingeniously designed to operate undetected, exploiting the Android platform in ways previously unseen.
PixPirate Overview
First brought to light by the Cleafy Threat Intelligence and Response team, PixPirate has caught the cybersecurity community’s attention due to its innovative evasion techniques. Further research by IBM reveals that unlike typical malware that seeks to hide its presence by masking its icon— a method effective only up to Android version 9—PixPirate adopts a more sophisticated approach to remain invisible across all versions up to Android 14.
PixPirate cleverly avoids using a launcher icon, circumventing the traditional method of detection and removal. This absence of an icon means that users have no direct way to initiate or even spot the malicious app, allowing it to lurk on the device unseen.
How It Works
The operation of PixPirate involves a two-app system designed to steal information from unsuspecting victims. The initial phase of the attack employs a ‘downloader’ app, disseminated via phishing tactics through platforms like WhatsApp and SMS. Upon installation, this app seeks permission for various invasive actions, including access to Android’s Accessibility Services, setting the stage for the deployment of the core malware.
The subsequent stage introduces the ‘droppee’ app, which houses the encrypted PixPirate trojan. This app is designed without declaring a main activity, thus evading appearance on the home screen or app drawer. Instead, it operates as a service that other applications can interact with, specifically the downloader app, which activates the PixPirate malware under certain conditions like device boot or connectivity changes.
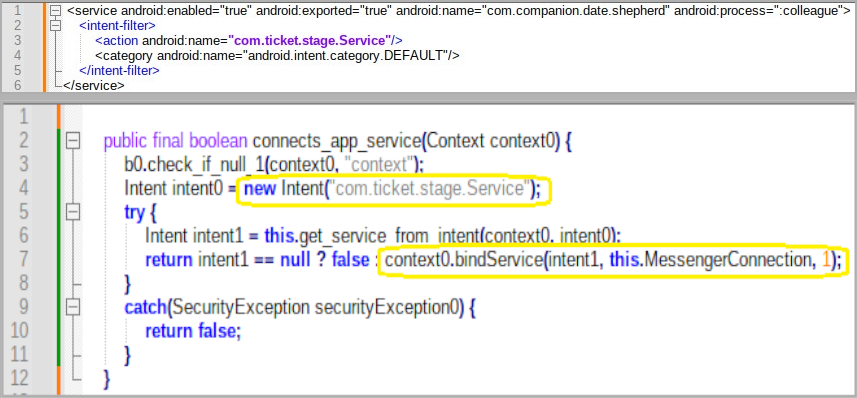
Fig 1. Service declaration (top) and event binding (bottom) (IBM)
Persistent and Hidden Threats
Even if users identify and remove the downloader app, PixPirate remains operational, triggered by various system events and continuing its surreptitious activities. Its primary target is the Brazilian instant payment system, Pix, attempting unauthorized transactions by capturing user credentials and bypassing two-factor authentication.
IBM’s research highlights the malware’s ability to conduct these fraudulent activities seamlessly, with a fallback to manual control should automated efforts falter. Alarmingly, PixPirate also demonstrates the capacity to disable key Android security mechanisms, including Google Play Protect.
Staying Ahead of PixPirate
Google gave a statement in response to this: “Based on our current detections, no apps containing this malware are found on Google Play.
Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services.”
For device security, we recommend that you always keep Google Play Protect on. Here’s how to check it’s enabled:
- Open the Google Play Store app.
- Tap the profile icon at the top right of your screen.
- Tap Play Protect.
- If Play Protect is turned off, this could be a sign that someone has disabled it in order to install a malicious app.

Fig 2. Enabling Play Protect on Android.