New ‘MFA Bombing’ Apple ID Phishing Scam

Published:
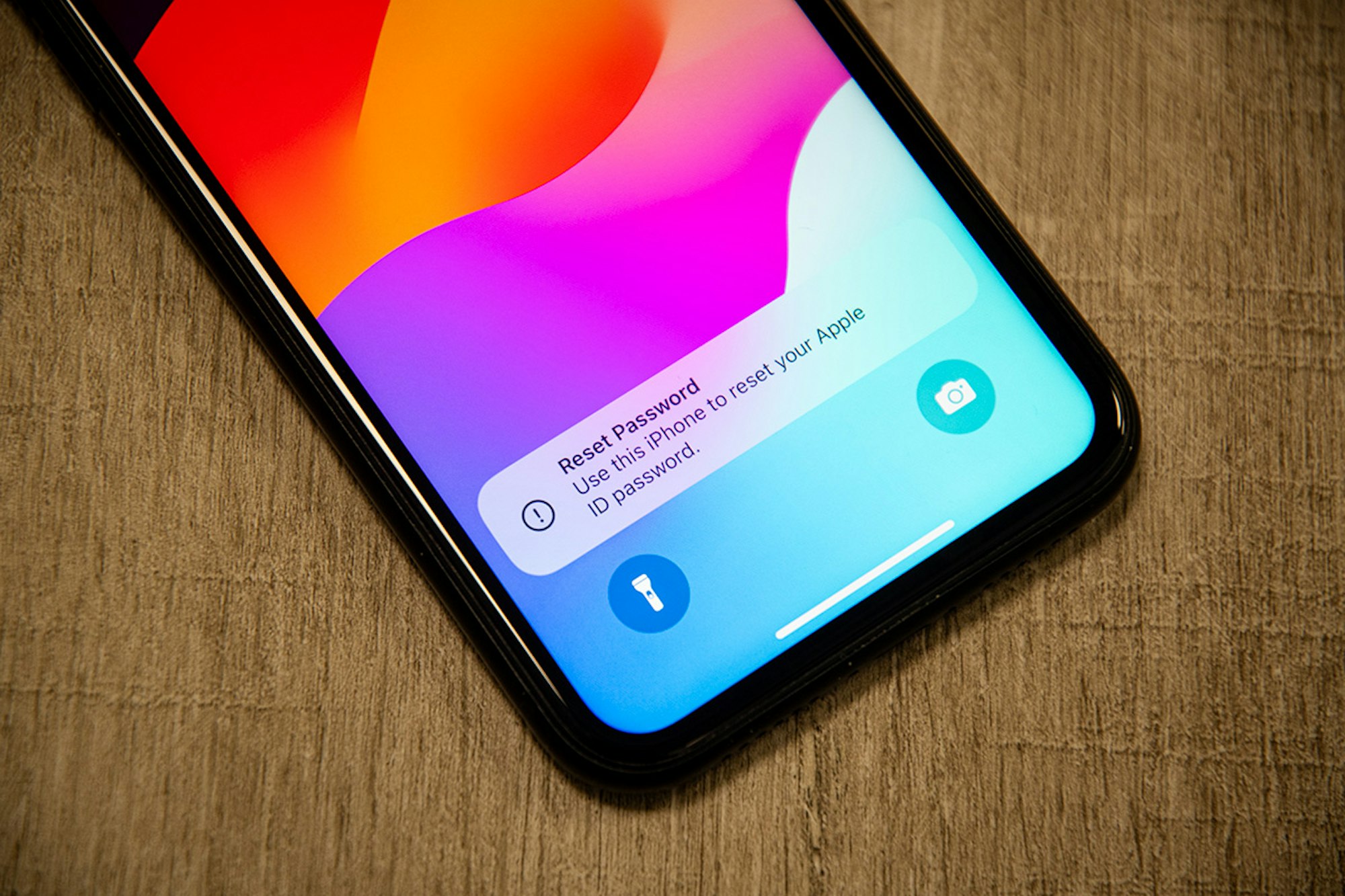
In the intricate world of cybersecurity, where vigilance is paramount, a new phishing campaign targeting Apple users has emerged, leveraging what seems to be an exploit in Apple’s password reset functionality.
This sophisticated attack not only inundates victims with relentless system-level prompts but also incorporates a deceptive phone call component, masquerading as Apple support to gain access to users’ devices and personal information.
Push Bombing
Parth Patel, an entrepreneur in the conversational AI domain, found himself at the epicenter of this phishing campaign on March 23. Documenting his ordeal on Twitter/X, Patel described the attack as a “push bombing” or “MFA fatigue” strategy. This tactic exploits multi-factor authentication (MFA) systems, barraging the user’s devices with alerts to authorize a password change or login attempt.
Patel’s experience was understandably disturbing, with all his Apple devices, including his watch, laptop, and phone, bombarded with system notifications to approve a password reset. The sheer volume of these prompts left his devices nearly unusable, forcing him to dismiss over a hundred notifications.
Spoofed Support Calls
The real twist in the tale came after Patel managed to deny all the password reset prompts. A call purportedly from Apple Support followed, with the caller ID spoofing Apple’s genuine customer support line.
The person on the line, feigning authenticity, recited Patel’s personal details accurately, all except for his real name, which they sourced from a dubious background report available online. This level of detail in the scammer’s knowledge underscored the elaborate preparation behind the attack.
The ultimate aim of the phishers was to persuade Patel to divulge a one-time code sent to his device, which would allow them to reset his Apple ID password, locking him out of his account and allowing the hackers to access his personal data.
Widespread Impact
Patel’s story is not an isolated incident. Others have shared remarkably similar experiences, indicating a broader pattern of attacks exploiting the same vulnerability. Victims have found themselves overwhelmed by password reset notifications, followed by calls from individuals posing as Apple support.
The common thread in these attacks is the manipulation of Apple’s system alerts and the sophisticated use of spoofed phone numbers and personal information to lend credibility to phishing attempts.
In response to these incidents, cybersecurity experts have been analyzing the attacks, seeking to understand the mechanisms at play and to devise countermeasures. Some suggest that changing the phone number associated with the Apple ID to a less accessible VOIP number could mitigate the risk, although this comes with its own set of trade-offs, such as the potential impact on iMessage and FaceTime functionality.
Security Measures and Apple’s Role
The incidents highlight a potential vulnerability in Apple’s rate-limiting mechanisms for password reset prompts, echoing past exploits where rate limits were bypassed to facilitate attacks. This similarity suggests that a concerted effort from Apple is required to address these vulnerabilities and protect users from such sophisticated phishing campaigns.
For users, the episode serves as a stark reminder of the ever-present threat of phishing attacks and the importance of maintaining vigilance. Adopting practices like using VOIP numbers for account security, employing email aliases to obscure real addresses, and being skeptical of unsolicited support calls can provide critical defenses against such scams.
In the end, the fight against phishing and cyber attacks is a continuous battle, requiring both users and corporations like Apple to remain ever vigilant and proactive in safeguarding personal and financial information in the digital age.