iMessage Exploited by New Darcula Phishing Campaign Against iPhone Users

Published:

In the ever-evolving landscape of cyber threats, a new menace has emerged in the form of a sophisticated phishing-as-a-service (PhaaS) named ‘Darcula.’
This insidious platform, equipped with over 20,000 domains, has been identified as a potent tool for cybercriminals seeking to impersonate brands and steal credentials from Android and iPhone users across more than 100 countries.
Exploring the Tactics of Darcula
Unlike conventional phishing methods, Darcula leverages modern technologies such as JavaScript, React, Docker, and Harbor to offer a dynamic and continuously evolving arsenal of over 200 templates, tailored to mimic various services and organizations.
What sets Darcula apart is its ingenious utilization of the Rich Communication Services (RCS) protocol for Google Messages and iMessage, forgoing traditional SMS channels for delivering phishing messages.
Targeting Mobile Users Across the Globe
Initially documented by security researcher Oshri Kalfon, Darcula has since gained traction within the cybercrime community, manifesting in numerous high-profile attacks worldwide.
Notably, research by Netcraft shows the platform has been implicated in scams targeting postal services, financial institutions, governmental agencies, telecommunications companies, airlines, and utility providers.
Credit Netcraft
Technologies and Tactics Unveiled
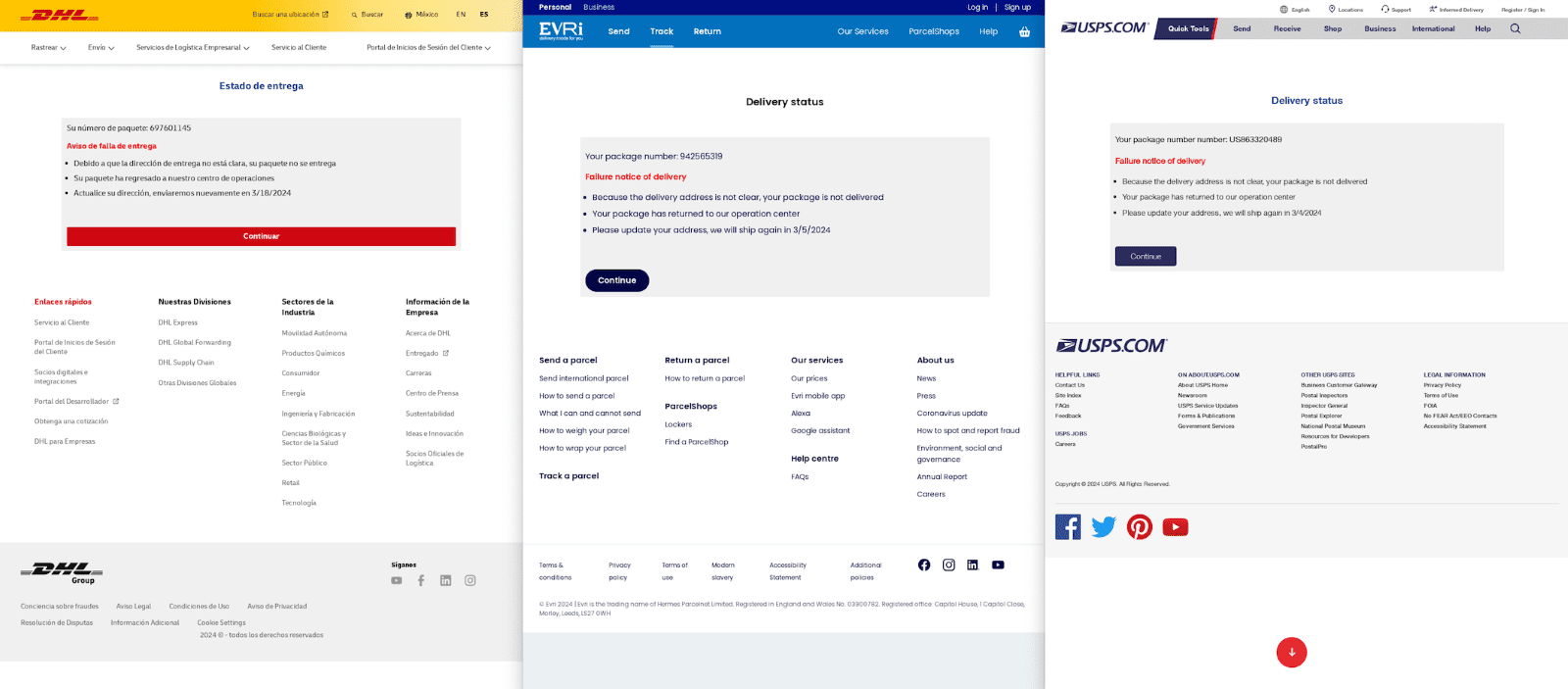
The phishing kit provided by Darcula offers meticulously crafted landing pages, adorned with local language, logos, and content, thereby enhancing its deceptive appearance.
Upon selection of a target brand, cybercriminals can swiftly deploy the corresponding phishing site and its management dashboard within a Docker environment, facilitated by the open-source container registry Harbor.
Darcula predominantly employs “.top” and “.com” top-level domains for hosting purpose-registered domains. To date, Netcraft has identified 20,000 Darcula domains across 11,000 IP addresses, with an alarming rate of 120 new domains added daily.
Credit Netcraft
How Cybercriminals Navigate RCS and iMessage Restrictions
In a departure from conventional SMS-based tactics, Darcula leverages RCS and iMessage to disseminate phishing messages, capitalizing on the perceived legitimacy conferred by these platforms.
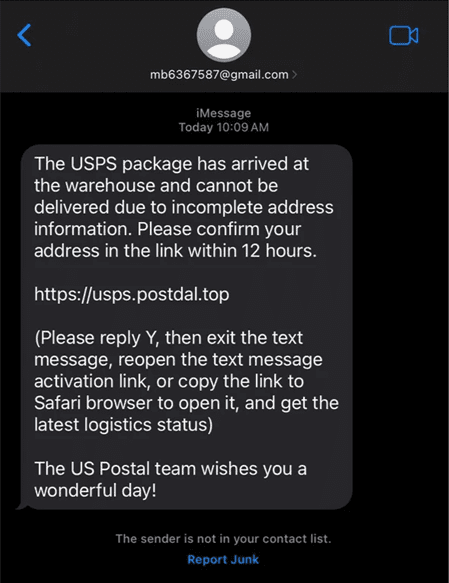
Furthermore, with the end-to-end encryption provided by RCS and iMessage, intercepting and blocking phishing messages based on their content becomes virtually impossible. However, these platforms also bring their own set of challenges, including restrictions imposed by Apple and Google, which demand innovative tactics for circumvention.
For instance, Apple’s stringent policies limit the volume of messages that can be sent from individual accounts, prompting cybercriminals to resort to multiple Apple IDs and device farms.
Moreover, iMessage’s safeguard requiring recipients to reply before accessing embedded URLs poses an additional hurdle, necessitating the inclusion of instructions in phishing messages to circumvent this measure.
Tips for Recognizing and Avoiding Darcula Phishing Attempts
In light of these developments, users are advised to exercise caution when encountering unsolicited messages urging them to click on URLs, particularly if the sender is unfamiliar.
Vigilance against grammatical errors, spelling mistakes, overly enticing offers, or demands for urgent action can serve as crucial safeguards against falling victim to phishing attacks perpetrated through evolving delivery methods.
As threat actors continue to innovate and adapt, staying informed and exercising skepticism remain paramount in safeguarding against the pervasive threat of phishing attacks like Darcula.