I Clicked On A Phishing Link, Now What?

Published:

If you think you’ve clicked on a phishing link, the first thing to do is take a deep breath. Your mind might be racing through worst-case scenarios, but this is a time to be systematic and calm, and regain control of the situation.
Phishing links mask themselves as urgent emails or enticing offers, which push users to make split-second decisions before rational thinking kicks in.
Remember, over 300,000 phishing attempts were reported to the FBI in 2022—so you’re far from alone.
Today, many attempts have become so sophisticated that even tech-savvy users are at risk.
If you’ve accidentally clicked on a phishing link or suspect malware was contained in an attachment, the potential consequences can feel overwhelming.
In this article, we’ll walk you through practical ways to regain control of your accounts and protect yourself from fraud.
Think your phone is hacked?
Phishing attacks don’t just try to steal your passwords, they could also install malware on your phone.
Check your device today with one of Certo’s award-winning apps.
What Is Phishing?
Phishing is a type of fraud where malicious actors attempt to deceive you into revealing confidential information. The information they’re after usually includes:
- Your passwords.
- Your login credentials.
- Your bank account numbers.
- Your Social Security numbers.
- Confidential business data.
The most common phishing attempts are social engineering attacks where cybercriminals send you a message impersonating your bank, a legitimate company, or even your place of work.
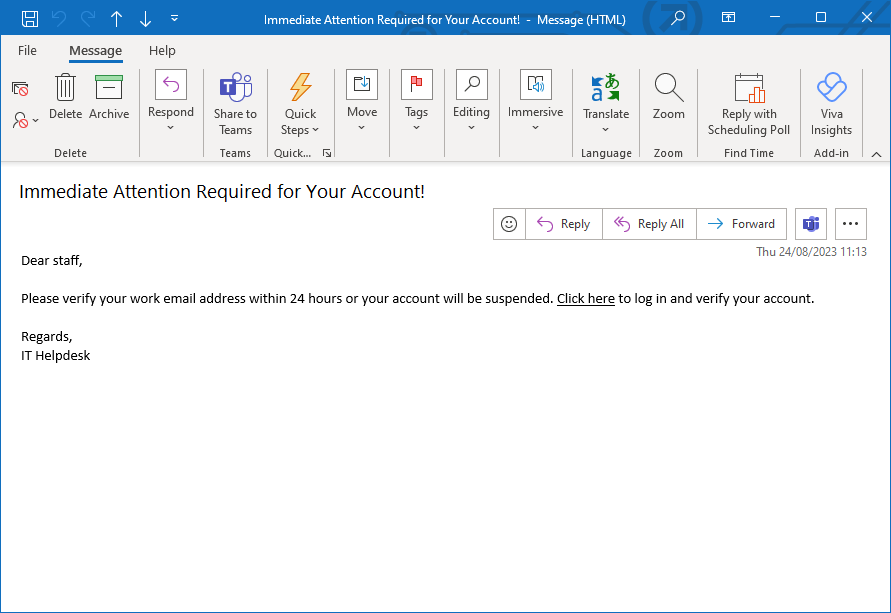
Fig 1. Example of a phishing email sent to a company employee.
How to Spot Phishing Attempts
Spotting phishing emails can be tricky because they employ clever tactics to look legitimate.
Most phishing attacks mirror the login pages of legitimate companies, have a similar email address with a subtle typo, and employ a sense of urgency. This urgency can come in many forms, including telling you that:
- Suspicious activity has been detected.
- Your account is about to be locked.
- You need to verify your account credentials.
- You need to pay an amount.
- You have received a delivery.
- You have won a prize.
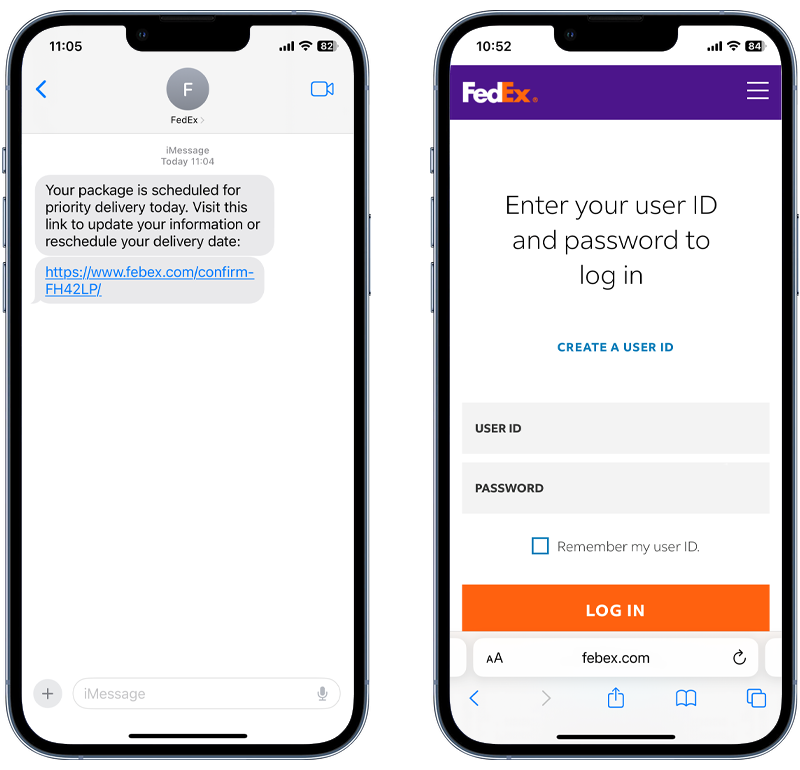
Fig 2. Example of a phishing SMS message and fake login page.
The goal of this is to entice you to act on impulse and do something before you have had a chance to think it through properly. But it’s not just phishing emails you need to be wary of. There are other types of sophisticated phishing scams, including:
- Smishing: SMS phishing, where malicious links are placed in SMS text messages.
- Fake invoices: Fraudsters send a fake invoice, along with instructions to call a phone number if the invoice is incorrect. When the victim calls, the fraudster attempts to solicit sensitive information.
- URL phishing: Cybercriminals create websites that masquerade as legitimate websites, which prompt users to input their data.
- Business email compromise: Hackers pose as executives to trick employees, partners, or customers into transferring funds or providing confidential information.
What Happens If You Click on a Phishing Link?

What happens after you’ve clicked on a phishing link depends on the type of scam you’re dealing with.
Depending on the sophistication and intent of the scam, different outcomes can emerge:
Malware
One of the most immediate dangers is the silent download of suspicious files onto your device. Most of these operations run stealthily in the background, so an average user wouldn’t even be aware of them.
Have you ever received an email from an unknown sender and seen a notification warning you not to open attachments from an untrusted source?
This is because malware can be damaging to businesses and individuals, and many email service providers and organizations proactively attempt to stop malware from spreading.
These malicious files can range from viruses that corrupt irreplaceable files and spyware that gains remote access to your device, to ransomware that locks your files and demands payment for their release.
Redirection to phishing websites
A malicious link embedded in a phishing email will typically lead you to a fraudulent website.
Often, these fake websites will look like trustworthy ones (for example, your online banking website) and ask you for your login credentials.
Once the criminals have gained this important data, they can use the same password and username you’ve given them to log into your real account and drain your funds.
Data harvesting
Some phishing emails or websites redirect you to forms that ask for a range of private information—from your birth date and address to your Social Security number.
This information can then be sold to unscrupulous buyers or published on the dark web, which makes you vulnerable to identity theft or financial fraud.
Access to your address book
If hackers gain access to your email address, they can send a phishing link to everyone in your address book.
Because the suspicious email seems to come from you, your contacts are more likely to think it’s legitimate and accidentally open the harmful link.
As the phishing link spreads through your contacts, it perpetuates the scam and could lead to embarrassment or damage to personal and professional relationships.
Control all your accounts
For most people, their primary email address is the recovery point for all their other accounts. If a cybercriminal breaches this email account via a successful phishing attack, they may be able to use it to gain access to your other accounts by intercepting password reset requests.
I Clicked on a Phishing Link but Didn’t Enter My Details
If you clicked on a phishing link but didn’t enter personal information, you’re in a much better position than if you had provided your details and should be safe from the most common types of phishing.
Remember however, some phishing links can install malware, so you should still take the following steps to protect yourself:
🔺 Immediately disconnect from the Internet
After you’ve clicked on a phishing link, immediately disconnect from the Internet. If you have a wired connection, unplug your ethernet cable.
Malware can spread to other devices connected to your network and cause further damage, so you’ll want to get offline as quickly as possible.
🔺 Run a malware scan
Rather than doing a quick scan, do a full system scan with your anti-malware software or antivirus program.
It takes longer but is more thorough, since it checks every file and application. After the scan, the software will list any suspicious files found.
Depending on the anti-virus program and the nature of the threat, either quarantine or delete the suspicious files to prevent installed malware from causing damage.
If you think your iPhone or Android phone has been hacked, Certo apps make it easy for you to scan, detect, and remove threats from your device.
Certo AntiSpy (iPhone) and Certo Mobile Security (Android) uncover malware—even if it’s designed to be undetectable—and safely remove cyber threats giving you peace of mind that your device is secure.
Think your phone is hacked?
Find malware installed via a phishing attack with Certo’s award-winning apps today.
🔺 Change weak passwords
Even if you didn’t enter any personal details, it’s still a good idea to change the passwords for your most important online accounts.
A good password manager is a great way to improve your password security by having strong and unique passwords for all of your online accounts. Some can even identify weak passwords or those that have been exposed on the dark web. We recommend NordPass.
I Clicked on a Phishing Link and Entered My Details

If you accidentally clicked on a phishing link and entered confidential data on a malicious website, it doesn’t mean all hope is lost.
Although it’s distressing, you can still protect yourself and your personal information by following each of the steps we’ve outlined above, along with the following:
🔺 Immediately contact your bank
If you shared any financial information with a phishing site, get in touch with your credit card company or bank immediately.
Inform them of the security breach and ask them to monitor transactions or freeze your account entirely.
You may also want to set up a fraud alert with your creditors. This alerts major credit bureaus that your account may be compromised, and they will take additional steps to authenticate your identity before extending additional credit.
🔺 Report the phishing attempt
If you received a phishing link to your business email address, notify your IT team or manager immediately.
Your company likely has protocols in place for handling phishing links and will secure other devices connected to the same network.
If you received a phishing link to your personal email address, you can report the message to your email provider so they can block any more attempts from the same sender.
If you received a phishing email from a cybercriminal who pretends to be another person or impersonates a legitimate business, notify them so they are informed and can secure their devices to stop the phishing link or malware attack from spreading among their contact list and causing more harm.
How to Protect Your Device from a Phishing Attack with Certo
Certo AntiSpy (iPhone)
From proactive system checks and vulnerability scans to threat removal, Certo AntiSpy offers a comprehensive solution for your cybersecurity.
Here are some of the key benefits of Certo AntiSpy for iPhone:
Vulnerability scanning – Instead of waiting for a malicious file to put your security at risk, it’s better to proactively search for potential vulnerabilities. Certo AntiSpy’s scanning function identifies areas where your data may be at risk, which enables you to take action before harm occurs.
Spyware detection – With Certo AntiSpy, you can detect apps that might be covertly snooping on your calls, texts, and other personal information, which provides peace of mind that your communications remain confidential.
Advanced threat detection – As technology evolves, online threats become more sophisticated. Certo AntiSpy’s advanced threat detection capabilities ensure that even the most modern hacking attempts are identified.
App permissions review – With so many apps available, it’s hard to keep track of which ones have access to what features. Certo AntiSpy allows you to review your app permissions by showing you which apps can access your microphone, camera, or location.
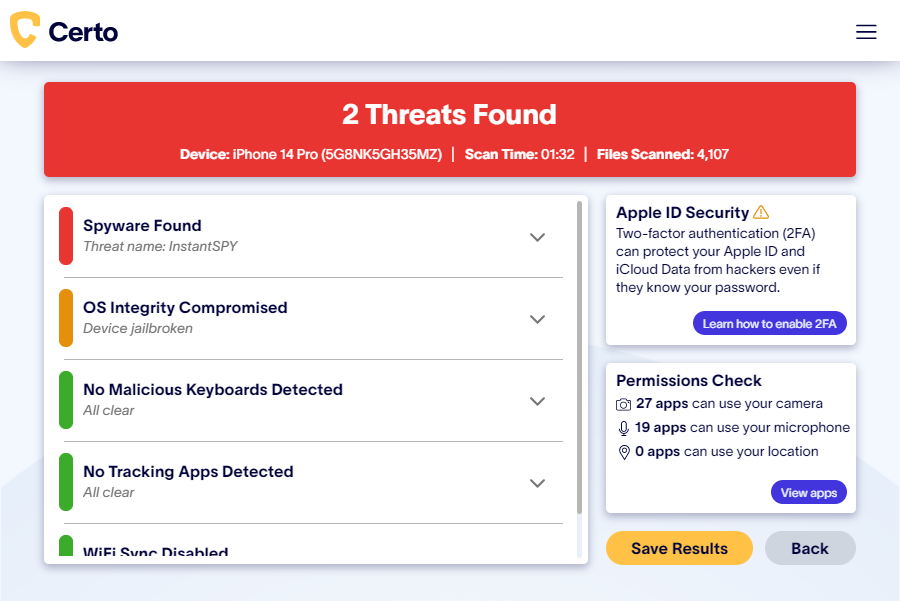
Fig 3. Certo AntiSpy for iPhone.
Certo Mobile Security (Android)
Protecting your Android device isn’t just about keeping it from falling into the wrong hands; it’s about safeguarding your personal data, communications, and digital life.
Here’s how Certo Mobile Security can safeguard your sensitive information:
Spyware detection – Malicious apps may secretly monitor your calls, messages, and private data—but you can guarantee the privacy of your communications with Certo Mobile Security for Android.
Threat removal – Identifying threats is only half the battle. Being able to quickly and efficiently remove them is equally important. Certo Mobile Security for Android not only detects threats but also assists in their removal, which ensures your device is protected against cyberthreats.
System adviser – One of the first lines of defense against malware is to understand the state of your phone’s operating system. Certo analyzes your OS for signs of tampering and provides guidance on how to maintain optimal device security.
Intruder detection – Check if your device is moved when you’re not around or catch someone trying to figure out your PIN. Your phone will also be able to take a secret picture of the person or stop them with an alarm.

Fig 4. Certo Mobile Security for Android.
The Final Word
Falling victim to a phishing scam can turn your sense of security and safety upside down in an instant—but that doesn’t mean you’re powerless.
There are numerous steps you can take to protect your private data, even if you’ve already clicked on a suspicious link.
But, when it comes to online security, proactive prevention is always best.
Download Certo AntiSpy for iPhone or Certo Mobile Security for Android to keep your devices protected and stay ahead of scammers—even before they attempt their strike.