How to Tell If Your Bluetooth Is Hacked and Protect Your Device

Published:

Earlier this year, footage emerged of a new commercially-available device that allows criminals to start cars without a key using a Bluetooth connection.
This followed news that devices using low-energy Bluetooth connections were at risk of being hacked. This included laptops, phones, and millions of Tesla electric vehicles.
These high-profile security loopholes show just how vulnerable Bluetooth connections are to hackers. It has led many people to question the security of their Bluetooth devices.
If you are worried about the security of your Bluetooth devices, you are in the right place.
Think your phone is hacked?
If you're concerned someone may have installed malware on your device via Bluetooth then run a quick scan today.
How Does Bluetooth Hacking Work?
Bluetooth uses short-range radio frequencies to share data between two devices. To connect two devices using Bluetooth, you first need to pair them. This involves registering the information each device needs to connect to the other.
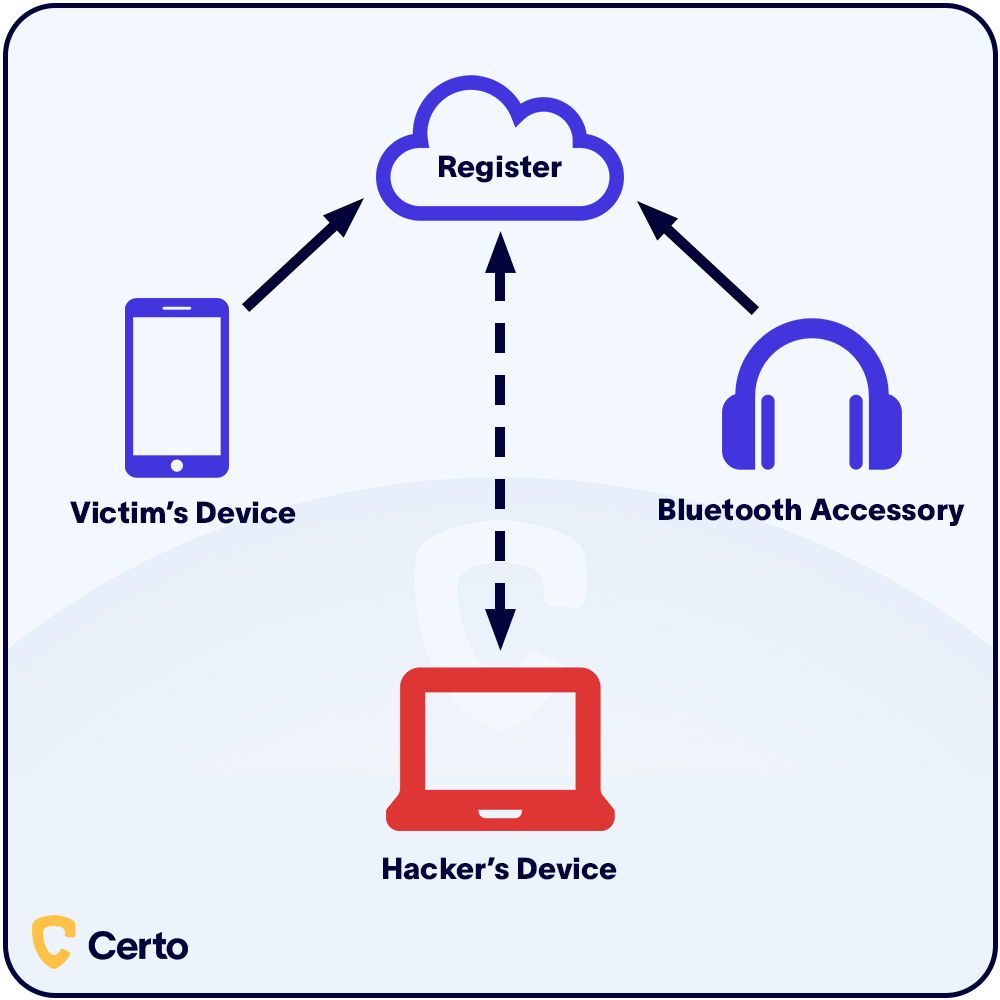
Fig 1. How Bluetooth hacking works
Theoretically, this should stop cybercriminals from using Bluetooth to access your phone. If an unknown device attempts to pair with your phone via Bluetooth, you can simply ignore or block it.
And because Bluetooth signals are short-range and are weakened by obstructions like walls, the chances are you’ll see who is trying to pair their Bluetooth device with yours.
The problem is that cybercriminals can use hacking tools to search for and identify vulnerable Bluetooth-enabled devices. They then intercept the Bluetooth handshake—that’s when the two devices connect—and use brute force attacks to break the handshake encryption and force a connection with their own device.
Bluetooth attacks usually occur in crowded environments like shopping centers or public transport hubs. That’s because many people will be trying to connect to Bluetooth devices and it will be hard for victims to spot the hacker.

Once the hacker connects to your device, depending on the method they’ve used they could:
- Attempt to crack your passwords and access things like bank accounts
- Steal personal data from your phone
- Listen to your calls and read your messages
- Send unsolicited messages and phishing attacks
- Install malware on your device
- Remotely unlock your car
- Unlock digital locks in your home or office
If a hacker connects to your device via Bluetooth in this way, you probably won’t know about it until it is too late.
Types of Bluetooth Hacks
There are several types of Bluetooth hacks. Some are more dangerous than others but they all connect to the victim’s device similarly.
Bluejacking
This is when a hacker sends you unsolicited messages and images over Bluetooth. Sometimes these messages are just annoying spam. But they could be phishing messages that attempt to get you to download malware. If this happens, they can track your phone and steal your data.
Bluesnarfing
When a Bluetooth device is in discoverable mode, it’s visible to other Bluetooth devices. If your device has vulnerabilities, an attacker can exploit these to connect to the device without your knowledge or consent. This type of attack is called Bluesnarfing.
Once connected, the attacker can gain access to data stored on the device, such as contacts, messages and photos.
Bluebugging
Bluebugging goes even further and exploits Bluetooth vulnerabilities on the device to actually install malware. The attack is usually initiated via a malicious link sent to the victim’s phone via SMS.
Once the hacker is connected, they have the ability to take over the device entirely. This means they can read and send messages, access the phonebook, initiate or intercept phone calls, and even leverage the victim’s identity on various apps including those for online banking. This intrusive access resembles the technique used in phone bugging, hence the name ‘Bluebugging’.
Bluesmacking
This is a denial-of-service (DoS) attack where the hacker overwhelms your device by sending huge packets of data to it over Bluetooth. This can cause your device to stop working or malfunction in other ways.
Car whispering
Car whispering is a technique that exploits vulnerabilities in a vehicle’s Bluetooth system to send and receive audio signals without your knowledge or consent. This type of attack is made possible when the vehicle’s Bluetooth system is left in “discoverable” mode, which allows other Bluetooth-enabled devices to identify and potentially connect to it.
The term “whispering” implies that the attacker is capable of “speaking” to the car (or its occupants) and/or “listening” to conversations within the vehicle. While it’s not as invasive or far-reaching as other forms of Bluetooth hacking, such as Bluebugging or Bluesnarfing which can access and manipulate personal data, car whispering nonetheless poses significant privacy concerns.
Blueborne hacks
This is a type of computer virus that automatically installs malware on any Bluetooth-enabled device that it comes within range of. You do not have to accept the connection, so it usually happens without your knowledge. This type of attack can spread and infect new devices quickly. Bluetooth hackers can control your device or access and steal data.
Stop hackers for good
Quickly and easily run a spyware check on your cell phone today with one of our award-winning apps.
How to Tell If Your Device’s Bluetooth Has Been Hacked
If you’re using a mobile device in a crowded public place, be vigilant of Bluetooth hacking.
Here are 9 signs that your Bluetooth may have been hacked. Please note these signs can also be caused by other factors, and their presence does not necessarily confirm a Bluetooth hack.
- Unexpected battery drain: Connecting to Bluetooth takes extra battery power. If you notice your battery drains faster than normal, it may be because hackers are accessing your Bluetooth.
- Unfamiliar devices in connection list: Check the list of devices paired with your Bluetooth. If you notice unknown or unrecognized devices, it could indicate that someone has gained access without your permission.
- Slow performance: If your device starts experiencing sluggishness or delays, it may be due to a compromised Bluetooth connection.
- Unrecognized apps: If you spot apps on your device that you didn’t download or don’t recognize, it may be a sign of a Bluetooth attack. Hackers can use Bluetooth to install malicious apps that steal data or take control of your device’s functions.
- Unexpected or strange notifications: Be vigilant about any unusual notifications or error messages related to Bluetooth connectivity.
- High battery temperature: Using Bluetooth puts an extra load on your device’s battery, which may cause it to warm up. If your device feels excessively warm, even when not in use, it might signal Bluetooth misuse by an unauthorized party.
- Bluetooth settings changes: If you notice changes to your Bluetooth settings that you didn’t make, it could indicate you have been hacked.
- Strange interference during calls: Odd disruptions or interference during phone calls or voice notes may be a sign that someone is listening in. Hacking Bluetooth is one of the ways hackers can do this.
- Increased mobile data use: Malware uses your device’s data connection to send information from your phone to the hacker. Higher-than-expected data use on your device is one sign that you have malware and that hackers may have used Bluetooth to install it.
7 Ways to Protect Yourself from Bluetooth Hacking
There are several things you can do to protect yourself from Bluetooth hacking. Some of these techniques are useful to prevent hackers from connecting to your device, while others are effective once they are connected.
1. Disable Bluetooth
It might sound obvious, but disabling Bluetooth when you’re not actively using it is the best way to minimize the risk of unauthorized access.
2. Disable discoverable mode
Configure your Bluetooth settings to make your device discoverable only when necessary, rather than leaving it visible to all nearby devices all the time.
How to do this on Android:
- Swipe down and tap the setting icon
- Tap connections
- Toggle phone visibility on or off
How to do this on iPhone:
- Swipe down from the top-right of your screen
- Tap the Bluetooth icon
- You can still connect to registered Bluetooth devices, but your phone is undiscoverable
- Note that your Bluetooth may automatically turn back on again after a certain period
3. Avoid pairing in public
Be cautious when pairing your devices in public spaces, as hackers may attempt to intercept the pairing process. Pair devices in secure and private environments whenever possible.
4. Be wary of unknown Bluetooth devices
Only pair your devices with trusted and recognized devices. Avoid connecting to unknown or suspicious devices. Periodically review the list of devices connected to your Bluetooth and remove any unrecognized or unused connections.
5. Keep your devices updated
Regularly update the firmware and software on your devices, as updates often include security patches that can protect against known vulnerabilities.
6. Be cautious with Bluetooth accessories
Be mindful of the Bluetooth accessories you use, such as keyboards, headphones, or speakers. Ensure that they come from reputable manufacturers and have proper security measures in place.
7. Use Anti-Spyware Software
Bluetooth is often used as a way to gain access to your device. More often than not hackers will use this vulnerability to install spyware on your phone.
This kind of malicious software is the real threat. It allows hackers to track your phone, steal your data, and monitor your calls and messages.
The best way to check if this kind of malware is installed on your phone is to run a spyware scan. Check out Certo AntiSpy for iPhone or Certo Mobile Security for Android.

Fig 2. Certo Mobile Security for Android
Certo protects your device by:
- Detecting spyware or bugging software on your device
- Analyzing your operating system for signs that it has been compromised
- Removing threats or providing easy instructions on how to do so
- Listing which apps have access to your location, camera, etc.
Protect Your Bluetooth Device
Bluetooth technology is everywhere—we often don’t even realize we’re using it. But Bluetooth is prone to hacking in certain situations. It’s therefore crucial to be able to recognize the signs of a hacked Bluetooth connection.
By following the measures recommended in this guide, you can significantly reduce the chances of being hacked via Bluetooth.
Cover Image by Freepik