How to Secure Your iPhone from Hackers

Updated:

In today’s interconnected world, our reliance on devices like iPhones has never been more pronounced. These sleek pieces of technology aren’t just for calls and texts anymore; they’re our all-in-one portal for communication, entertainment, and managing personal affairs.
From checking emails to banking and engaging on social platforms, iPhones have made life significantly more streamlined.
Yet, this convenience doesn’t come without risks. Cybercriminals often see iPhones as prized targets given the wealth of information they hold. Wondering how to bolster your iPhone’s defenses against such threats?
If you suspect your iPhone has been hacked, consider using specialized tools like Certo AntiSpy to find and remove threats from your device.
For proactive measures, delve into this comprehensive guide that outlines precautions and best practices to fortify your iPhone against hackers
Stop hackers for good
Combat spyware and other cyber threats with Certo AntiSpy, the world's leading anti-spyware tool for iPhones.
How to Protect Your iPhone From Hackers
Use a strong passcode and change it often
This may seem obvious, but your passcode is the first line of defense to stop someone from getting into your iPhone. You should also change your passcode regularly, especially if you are often observed when typing it in.
Very often, a hacker will need physical access to your phone to install and set up spyware or malware, so a strong passcode can make this more difficult.
Here’s a guide on how to create a strong passcode and set it up:
✅ Length matters: The longer your passcode, the harder it is to crack. By default, an iPhone uses a six-digit numeric passcode. However, we recommend an even longer alphanumeric code for added security.
✅ Avoid common patterns: Avoid sequences like “123456” or repeated numbers like “111111.” Similarly, don’t use easily guessable information, such as your birth year or address.
✅ Mix it up: If using an alphanumeric code, combine uppercase and lowercase letters with numbers. Consider adding special characters like &,%, and $ for added complexity.
✅ Randomness is key: The best passcodes are random. Instead of creating a passcode off the top of your head, consider using a password manager or another tool to generate a random sequence.
💡 If available, you should also use biometric features to unlock your phone, like Face ID or fingerprint access.
Setting your strong passcode on your iPhone
- Open the Settings app on your iPhone.
- Scroll down and tap on Face ID & Passcode or Touch ID & Passcode (depending on your iPhone model).
- Enter your current passcode if prompted.
- Tap on Change Passcode.
- Enter your old passcode once more.
- When prompted to enter a new passcode, tap on Passcode Options right above the numeric keypad.
- You can choose from the options: Custom Alphanumeric Code, Custom Numeric Code, 6-Digit Numeric Code, or 4-Digit Numeric Code. For maximum security, opt for the Custom Alphanumeric Code.
- Enter your new, strong passcode.
- You’ll be asked to verify by entering it again.
- Once confirmed, your iPhone will now be secured with your new passcode.
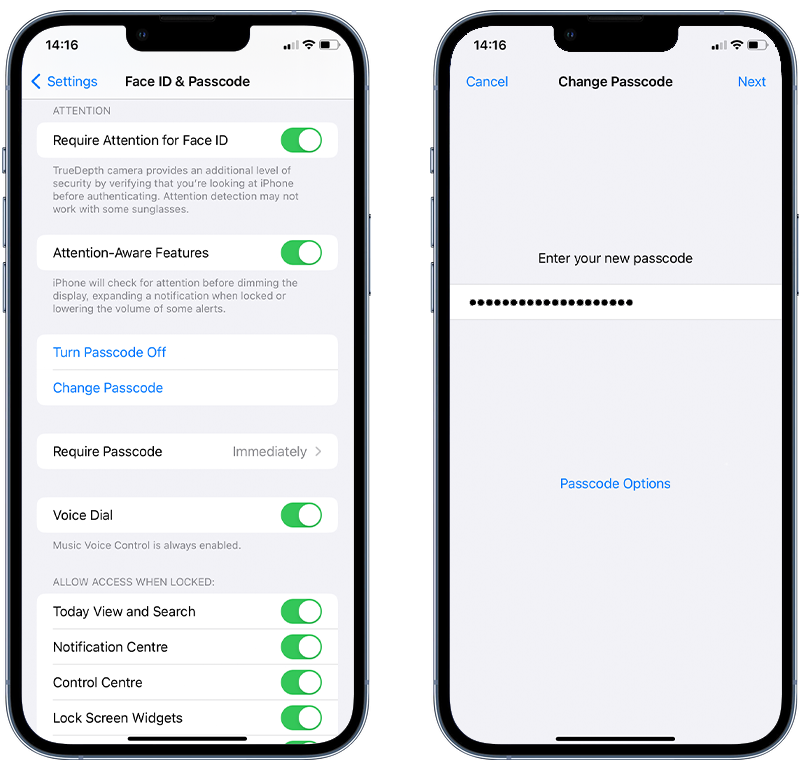
Fig 1. Setting an alphanumeric passcode on iPhone.
⚠️ Remember, while having a robust passcode is essential, it’s equally vital to remember it. If you’re using an exceptionally complex alphanumeric code, store it securely, perhaps in a trusted password manager or a secure offline location.
Keep your iPhone updated
We like to think that iPhones are intrinsically protected from hackers, and while Apple does what it can, your device can quickly become insecure if you do not install software updates as soon as they are available.
Security vulnerabilities that hackers can exploit are regularly fixed in updates to iOS, so don’t put it off, even if it’s not convenient. If available, you should turn on automatic updates to make this process even easier and have the latest security patches installed.
Keeping your phone updated also applies to your app library. Recently, some hackers have been able to target vulnerabilities in specific apps, such as WhatsApp. So, ensure you keep everything updated to stop hackers from getting into your iPhone.
By running the latest version of iOS, you ensure that it operates with the latest security features and boosts device performance.
How to check for iOS updates
- Connect to Wi-Fi.
- Open the Settings app.
- Tap on General.
- Tap on Software Update.
- Your iPhone will check for available updates.

Fig 2. Performing a software update on iPhone.
Use two-factor authentication (2FA)
Many people choose to back up their iPhone data to iCloud automatically. This is convenient and a great feature if your phone is broken or lost. However, it also means there’s a second full copy of your data out there that could potentially be accessed by hackers.
To protect your iCloud account, you should always use two-factor authentication (2FA) to access it. This means that even if a hacker manages to crack your password, your account will still be safe, and your backed-up data will be secure.
How to set up 2FA on an iPhone
- Go to Settings and select your name.
- Select Sign-In & Security.
- Tap to turn on two-factor authentication.

Fig 3. Enabling two-factor authentication for an Apple ID.
Download a good security app
There are various iPhone security apps available to download from the App Store. However, for the best protection we recommend using an app that can run a deep scan of your iPhone, such as Certo AntiSpy. Due to the unique way Certo AntiSpy analyzes your device, it can perform the most thorough security scan and find threats that other apps can’t.
How Certo AntiSpy works for iPhones:
✅ Download: Firstly, download Certo AntiSpy to your Windows or Mac computer.
✅ Scan: Connect your iPhone using the USB cable and click Scan Now to begin. Certo will run a deep scan of your iPhone for spyware and other cyberthreats.
✅ Detect: If Certo identifies any threats, it provides detailed information about the detection. This includes the name of the threat, its capabilities, and possible implications.
✅ Remove: Certo will either remove the threat for you or provide step-by-step instructions to remove it from your device yourself.
Use a VPN
Another great way to protect your iPhone from hackers is to use a VPN (Virtual Private Network). A VPN will encrypt all traffic and data between your phone and any online resource you access, including:
- Your email account.
- Social media.
- Any website you visit.
We highly recommend NordVPN. This will ensure no one can eavesdrop on your online activity.
Enable Lockdown Mode
Lockdown Mode is an extreme security feature that offers additional protection by limiting certain device features. It’s available on iPhones and iPads running iOS 16 or later.
This feature is designed to provide optional protection against sophisticated cyberattacks, particularly from state-sponsored iOS spying software developers like Pegasus and Predator.
This mode is designed for people who might be personally targeted by surveillance software via state-sponsored cyber attacks due to their professions or identities.
To enable Lockdown Mode on an iPhone, follow these steps:
- Open the Settings app.
- Tap Privacy & Security.
- Scroll down and tap Lockdown Mode, then tap Turn On Lockdown Mode.
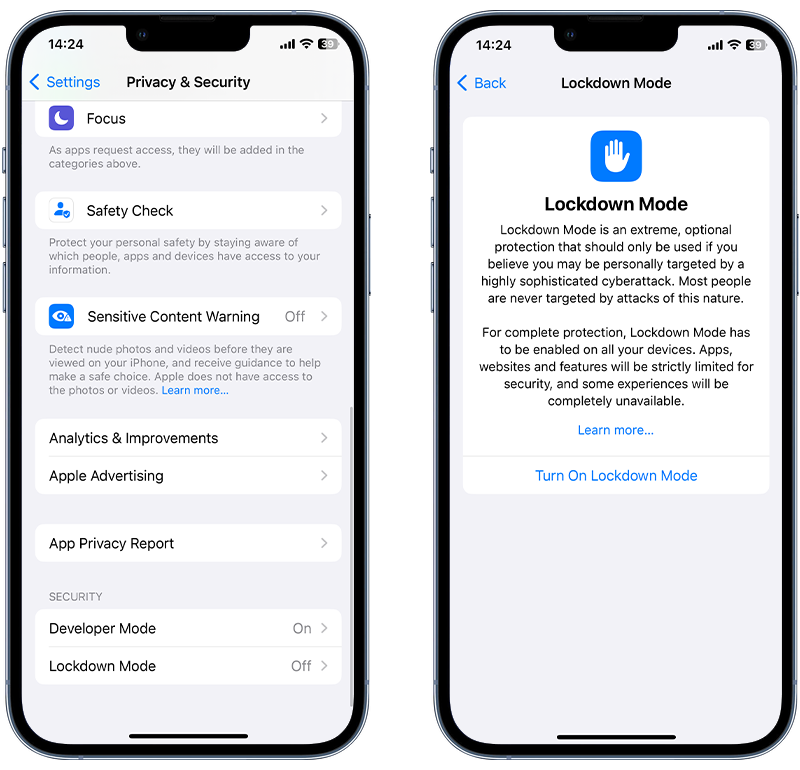
Fig 4. Enabling Lockdown Mode on iPhone.
Turn on Advanced Data Protection
In iOS 16, Apple added the option to enable Advanced Data Protection for your data stored in iCloud. This feature encrypts your data, meaning it can only ever be accessed by one of your trusted devices.
Here is how to set up Advanced Data Protection on Apple devices:
- Open the Settings app.
- Tap your name, then tap iCloud.
- Scroll down, tap Advanced Data Protection, then tap Turn on Advanced Data Protection.
- Follow the on-screen instructions to review your recovery methods and enable advanced data protection.
You can learn more about this feature here.
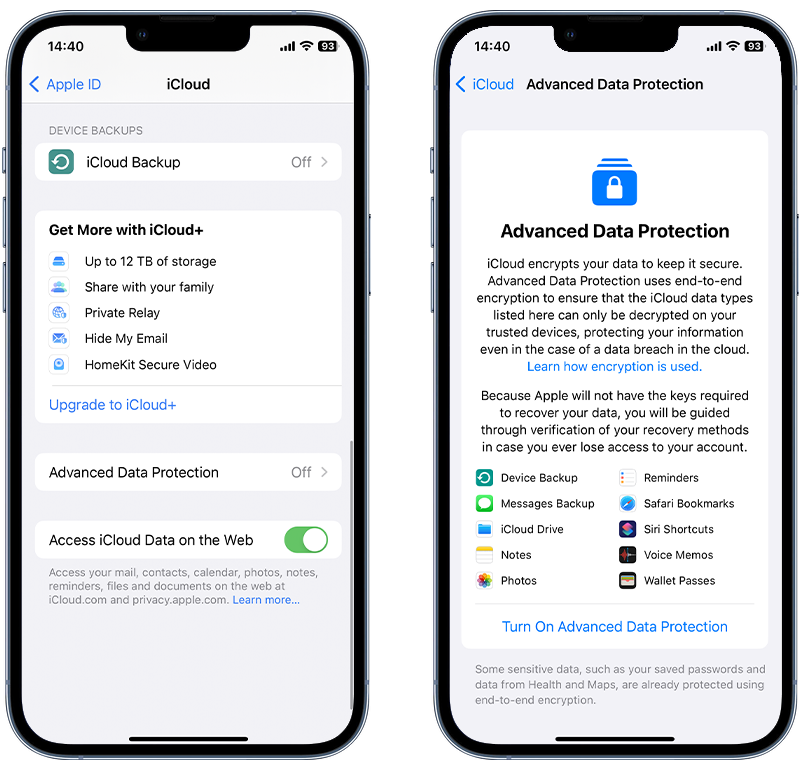
Fig 5. Enabling Advanced Data Protection for your iCloud account.
iPhone Security: Common Oversights and Risks
Avoid jailbreaking
Jailbreaking is the process of removing Apple’s manufacturer restrictions from the device. This allows you, or anyone else, to customize the device and opens up new options outside Apple’s restrictions.
While this might sound like a good idea, Apple’s restrictions are in place to keep security tight. By removing them, you essentially leave your front door open to hackers. While a jailbroken iPhone offers more user flexibility, it’s much more vulnerable to spyware and malware.
Don’t tell anyone your passcode
Once you have a strong passcode, keep it to yourself. It can be upsetting to think about, but you are much more likely to be hacked by someone you know than some anonymous hacking organization.
Keeping your passcode private, even from people you feel you can trust, is crucial to device security.
Only download apps from trusted sources
Third-party apps and app stores often lure users with the promise of free versions of otherwise paid apps. This might make it tempting to install apps from these sources. However, you should always exercise caution, as many third-party offerings can contain malware.
Ask yourself what possible benefit there could be for them to offer you something for free. Often, the answer is that you will pay in another way.
For optimal security and peace of mind, installing iPhone apps exclusively from Apple’s App Store is recommended. Apple meticulously reviews and vets all apps before they become available on their platform.
Be careful on public Wi-Fi
We can easily be tricked into thinking an unsecured Wi-Fi network is safe if it uses a familiar, official, or otherwise trustworthy-sounding name.
While many of these networks could be safe, you often have no way of knowing who controls the network or who else is connected to it.
If you have to join an unsecured Wi-Fi hotspot, then make sure you use a reputable VPN to protect your iPhone from hackers.
Be cautious with custom keyboards
While custom keyboards can offer an enhanced typing experience by adding new emojis or improving your writing, they come with potential security risks.
Every key you press, from regular messages to sensitive login credentials, passes through the keyboard.
If a keyboard app is malicious, it could log and transmit this data to unauthorized third parties.
Custom keyboards are becoming an increasingly popular way for hackers to steal data from iPhones. It’s therefore essential to only install them from a recognized and trustworthy source, like the official App Store. Even then, checking reviews, developer credentials, and any mentioned app permissions is wise.
💡 Run a quick scan with Certo AntiSpy to see if any malicious keyboards are installed on your iPhone.
Don’t use Developer Mode if you don’t have to
Developer Mode, while useful for software developers and tech enthusiasts, also opens up potential vulnerabilities. When activated, it can grant access to deeper system functionalities.
This expanded access can, in turn, be exploited by hackers. For instance, someone with ill intentions could connect your device to their computer and sideload a harmful application, bypassing standard security measures.
For the average user, the benefits of Developer Mode might not outweigh the risks. If you’re not using your device for development tasks or other specialized functions, it’s recommended to keep this mode disabled.
By doing so, you reduce potential entry points for threats and further safeguard the integrity of your device’s security.
Don’t click on links in unsolicited emails or text messages
iPhone hacks are becoming increasingly sophisticated. Hackers are constantly looking for new ways to infiltrate devices. One prevalent method they employ is sending malicious phishing emails or texts directly to potential victims.
While device security continues to evolve and improve, these tactics are designed to exploit human error. These links are specifically crafted to either deploy malware or deceive the user into divulging personal information.
Be careful if you get a link in an email or text that you weren’t expecting, especially if it says you’ve won something or threatens to lock you out of an account.
⚠️ Are you concerned your iPhone has been hacked? See our guide on what steps to take if you’ve been hacked.
While these guidelines will bolster your defense against those trying to hack your iPhone, it’s crucial to remain vigilant.
If you ever have doubts regarding the security of your device, the best course of action is to scan for potential threats like viruses or malware promptly.
Secure your iPhone from hackers
Millions trust Certo to protect their mobile devices from hackers. Find out how Certo AntiSpy could help secure your iPhone.
Frequently Asked Questions (FAQs)
How can I check if my iPhone has been compromised?
Regularly scanning your device with trusted security tools like Certo AntiSpy, checking for unexplained battery drain, and being alert to unfamiliar app installations can help you detect suspicious activities.
How do I make sure my iPhone is safe?
To keep your iPhone secure, consistently update to the latest iOS versions which come equipped with important security patches. Employ a robust passcode and take advantage of Face ID or Touch ID features. It’s essential to download apps solely from the official App Store and to be wary of any suspicious links or emails. Lastly, use Advanced Data Protection for iCloud for an added layer of security.
How can I protect my iPhone from phishing attacks?
Avoid clicking on unfamiliar links sent to you via email or text, especially if they prompt you for personal information or credentials.
Always double-check the sender’s details and be wary of any unsolicited communication. If you have accidentally clicked on a phishing link, read our guide on what to do.
Cover Image by vecstock on Freepik