How to Remove Spyware from an iPhone or iPad

Updated:

In today’s tech-savvy world, keeping devices like iPhones and iPads safe from spyware is crucial. Spyware is sneaky software that can get into your device and steal your info.
Unfortunately, removing spyware from an iPhone or iPad is often more challenging than simply deleting a malicious app. This is because spyware hides deep in the device’s file system to try and avoid detection.
Despite the robust safety features of Apple devices, they can still fall prey to these harmful spyware programs. The good news? You can spot and eliminate spyware on your iPhone or iPad with relative ease. This guide will walk you through:
➡️ Removing spyware: Follow step-by-step instructions to purge any spyware from your device.
➡️ Spotting the signs: Learn to tell whether your device has fallen victim to spyware.
➡️ Understanding spyware: Know what it is and how it can infiltrate your iPhone or iPad.
➡️ Proactive protection: Discover proactive steps you can take to prevent future spyware attacks, which will ensure your devices remain safe and your personal information stays private.
Ready to secure your iPhone? Let’s get started!
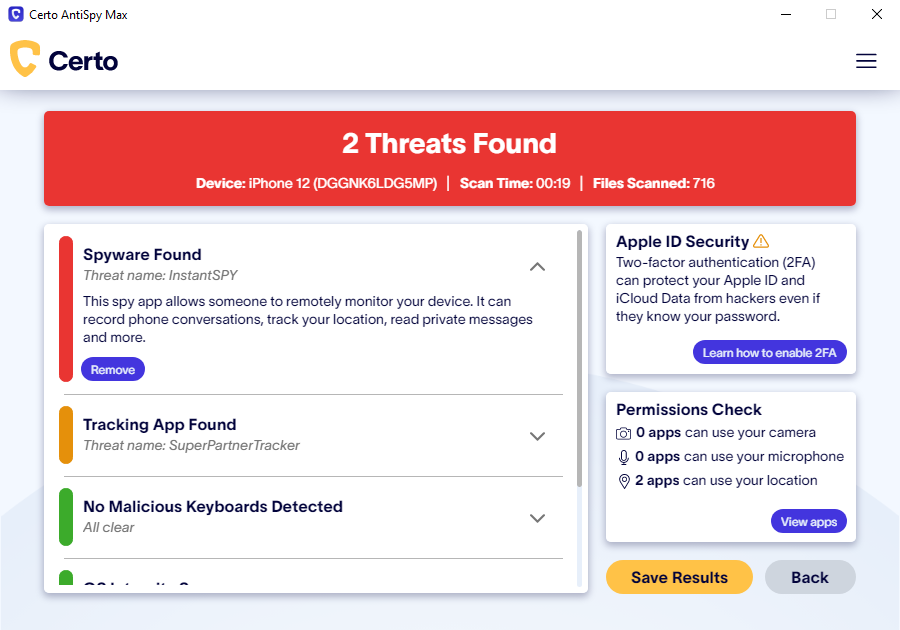
Remove spyware the easy way
Uncover and remove spyware with Certo AntiSpy, the award winning anti-spyware tool for iPhone.
How to Remove Spyware from Your iPhone or iPad
1. Restart your device
It may sound simple, but restarting your device is an excellent first step when looking to remove spyware on your devices.
One of the most intrusive types of spyware relies on jailbreaking your iPhone or iPad to give a hacker remote access.
However, when you restart your phone, most jailbreaks will be removed, rendering any installed spyware useless. The hacker would then need to find a way to regain physical access to your device to re-run the jailbreak.
Restarting an iPhone is a straightforward process. Here’s how to do it:
- Press and hold the side button and the volume up or down button until two sliding buttons appear.
- Release the buttons.
- Slide to power off.
- Once powered off, hold the side button until you see the Apple logo appear.
2. Update your device’s operating system
Most spyware relies on out-of-date software, which often contains security vulnerabilities. Therefore, ensuring you are running the latest version of iOS is vital for your device’s security.
Keeping updated can protect your iPhone in two ways:
1️⃣ Firstly, if you already have spyware that’s exploiting a known security vulnerability, the threat will be removed as soon as you update to a new iOS version.
2️⃣ Secondly, running the latest version of iOS restricts the options available to a potential hacker, which makes it much harder to compromise your device in the first place.
Updating your iPhone to the latest version of iOS is a simple process. Here’s how to do it:
- Go to Settings.
- Scroll down and tap General.
- Tap Software Update.
- If a software update is available, tap Download and Install.
- If prompted, enter your passcode.
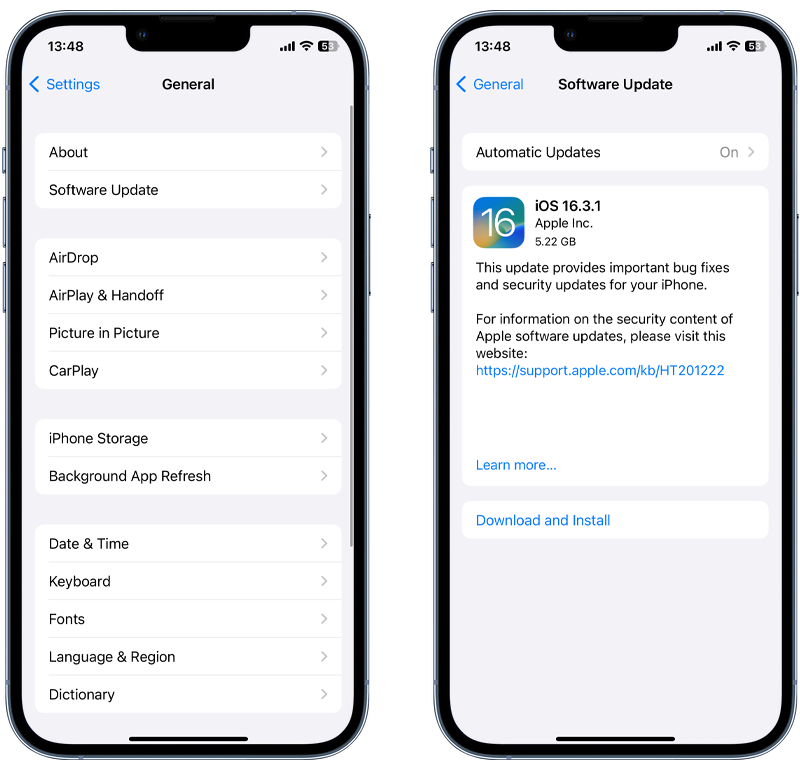
Fig 1. Performing an iOS update.
💡 Pro Tip: Turn on Automatic Updates under Settings > Software Update to ensure you are always running the latest version of iOS.
3. Remove suspicious apps
If you prefer taking a more granular approach to threat removal, manually review all the apps installed on your device and delete any that look suspicious.
Also, remember to check app folders, as hackers often use these to keep their spy apps out of sight.
It’s worth noting that some malicious apps can be hidden from the device’s home screen altogether, which means they could go unnoticed when performing a visual review of installed apps.
💡 Pro-tip: Run a scan with antivirus software like Certo AntiSpy to find malicious apps designed to be completely invisible.
4. Remove unknown custom keyboards
Malicious custom keyboards installed on your iPhone can act as keyloggers that record every keystroke you make, including passwords and personal information. This data can then be transmitted to hackers because they monitor everything you type. Such keyboards should be removed immediately.
To delete unrecognized custom keyboards on your iPhone, follow these steps:
- Go to Settings > General > Keyboard.
- Tap Keyboards.
- Tap Edit.
- Tap the red minus button next to any keyboard you don’t recognize.
- Tap Delete.
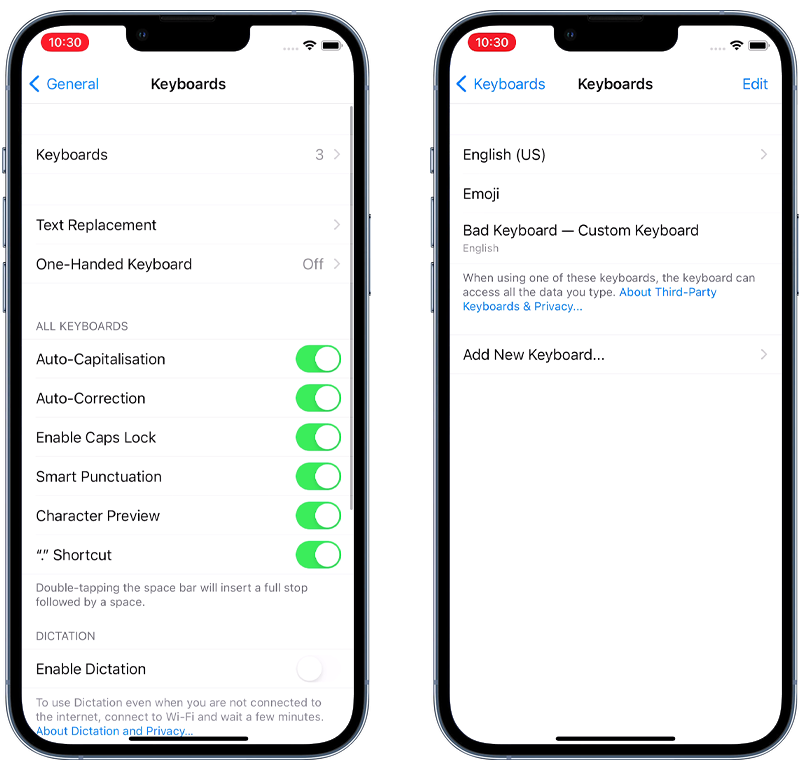
Fig 2. Removing a custom keyboard on iPhone.
Note: By default, most devices have two keyboards: Your chosen language (e.g. English (US)) and Emoji.
5. Change your Apple ID password
Some hackers will go after your iCloud account instead of targeting your device with spyware. It can be tricky to detect when someone has accessed your iCloud data. Fortunately, it’s straightforward to protect your account from this attack.
Firstly, you’ll want to change the password for your Apple ID as soon as possible. Doing so will lock any hackers out of your account, which means they must work out your new password to regain access.
It’s important to have access to the email account associated with your Apple ID and first check your trusted phone number before you proceed, as these will be used to verify your identity during the password reset process.
Here’s how to change your password on an iPhone and iPad:
- Go to Settings.
- Tap your name at the top.
- Tap Sign-In & Security.
- Tap Change Password.
- Enter your current passcode when prompted.
- Follow the on-screen instructions to update your password.
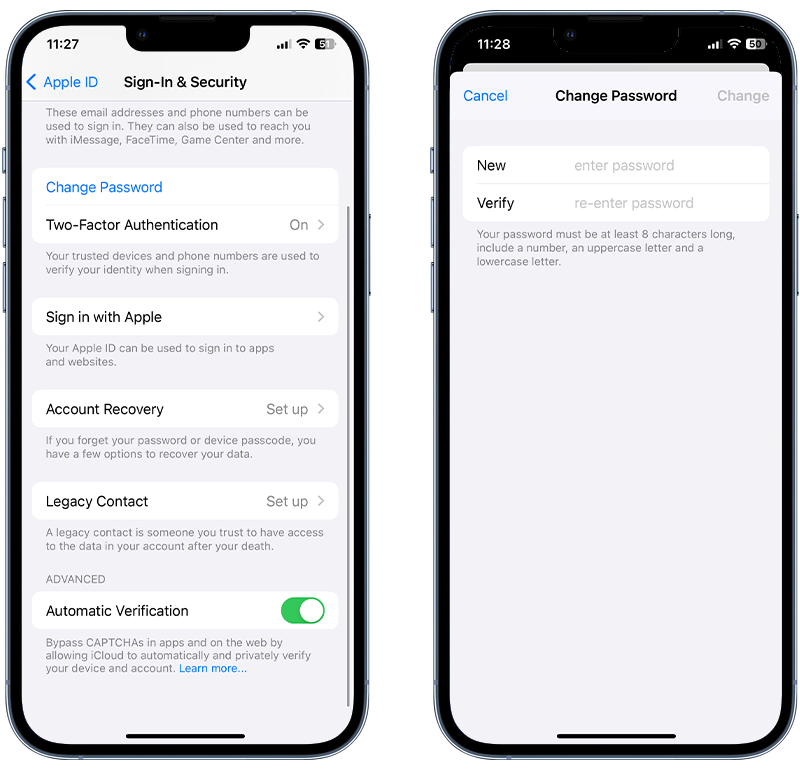
Fig 3. Changing your Apple ID password on iPhone.
Alternate method (for both iPad and iPhone)
If you can’t access your device, you can reset it using the Apple ID account page:
- Go to the Apple ID account page (appleid.apple.com) on a browser.
- Sign into your Apple account.
- Click Sign-In and Security.
- Click Password.
- Enter your current password and set a new password.
- Check the box labeled Sign out of Apple devices and websites associated with your Apple ID.
- Click Change Password.
💡 Pro Tip: Ensure two-factor authentication is enabled for your Apple ID. If it’s turned on, your account and data are better protected from unauthorized remote access, even if someone works out your Apple ID password. More on this below!
6. Enable Lockdown Mode
Lockdown Mode is an optional, extreme security feature available on iPhones and iPads running iOS 16 or later.
This feature is designed to provide additional protection against sophisticated cyberattacks, particularly from state-sponsored iOS spying software like Pegasus and Predator.
Lockdown mode is designed for people who might be personally targeted by surveillance software via state-sponsored cyberattacks due to their professions or identities.
To enable Lockdown Mode on an iPhone or iPad, follow these steps:
- Open the Settings app.
- Tap Privacy & Security.
- Scroll down and tap Lockdown Mode, then tap Turn On Lockdown Mode.
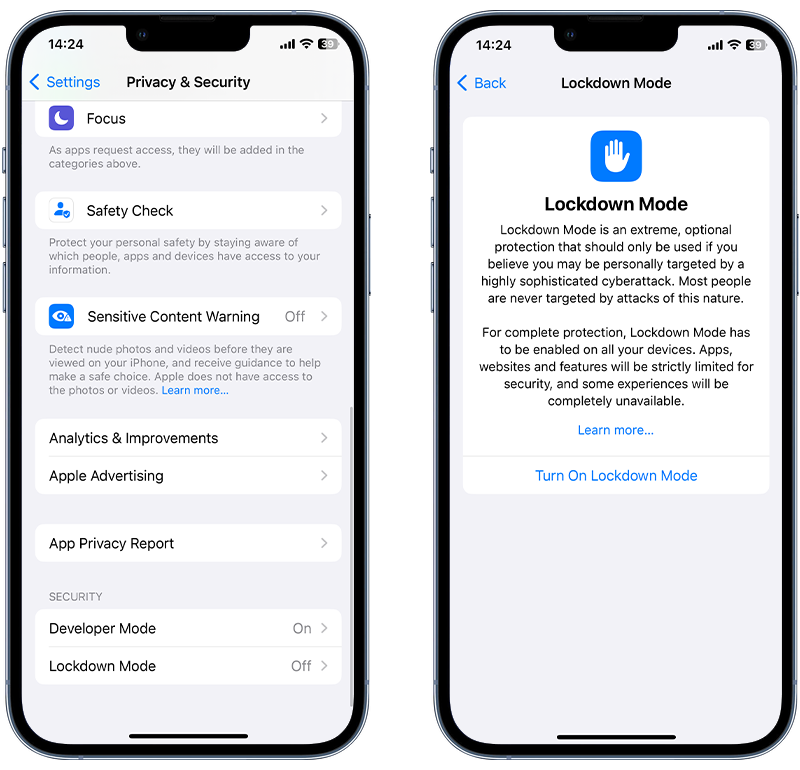
Fig 4. Enabling Lockdown Mode on iPhone.
⚠️ Important: When Lockdown mode is enabled, some aspects of your device will function differently. Certain apps, websites and features will be strictly limited and some experiences will be completely unavailable.
7. Remove unknown Bluetooth devices
Bluetooth technology is everywhere—we often don’t even realize we’re using it. But Bluetooth is prone to hacking in certain situations and can give hackers access to your phone.
It’s crucial to unpair any unrecognized Bluetooth devices if you suspect your iPhone has been compromised. Here’s why:
⛔ Data access and transfer: Once paired, some Bluetooth devices can access sensitive data on your iPhone or even send data to your device.
⛔ Eavesdropping: Certain Bluetooth-enabled devices, especially headsets or car systems, can be used to listen to your calls and read your text messages.
⛔ Remote control: Some Bluetooth devices can exert control over certain iPhone functions, like taking over your keyboard, calls and audio functions.
To unpair unrecognized Bluetooth devices on your iPhone, go to Settings > Bluetooth and check for unfamiliar devices. If any are found, click on the (i) icon next to the device and select Forget This Device.
Hackers may attempt to access your iOS devices via Bluetooth, either by exploiting vulnerabilities in the communication protocol or by using a paired device to eavesdrop on your communications.
To remove unknown or unwanted Bluetooth devices from your iPhone or iPad, follow these steps:
- Open the Settings app on your device.
- Navigate to Bluetooth.
- Here, you will see a list of paired devices. Locate the Bluetooth device you want to remove.
- Tap the information (i) icon next to the device name you wish to remove.
- A new screen will open, then tap Forget This Device.
- A confirmation pop-up will appear; tap Forget Device or Confirm to remove the device from your list of paired Bluetooth devices.
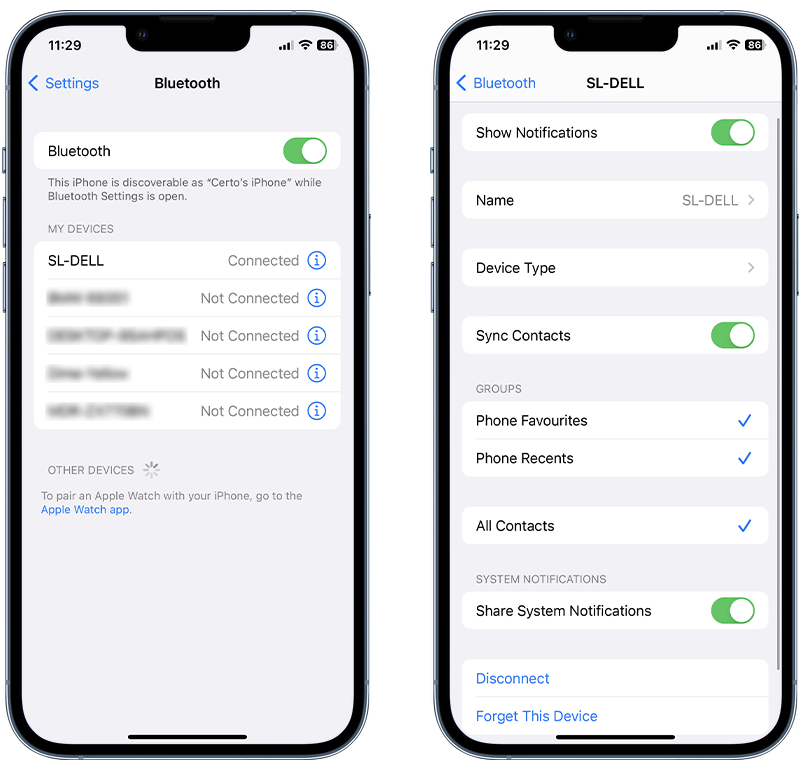
Fig 5. Removing an unknown Bluetooth device on iPhone.
💡 Expert Insight: How do hackers use Bluetooth to hack your Apple devices?
🔵 Paired Device Snooping: When paired with your iPhone or iPad, some Bluetooth devices have the ability to access sensitive data. Hackers can use this functionality as a way to snoop on their victim’s messages, notifications or even to remotely control certain functions of the device.
Check for and remove any paired Bluetooth devices that may have been added without your consent.
🔵 Bluesnarfing: When a Bluetooth device is set to 'discoverable' mode, it broadcasts its presence to nearby devices. However, if your device hasn’t been updated in a while and contains security vulnerabilities, it could become a target for Bluesnarfing, an attack that allows a hacker to covertly pair with your device without your permission.
Upon establishing a connection the hacker may access and extract private information stored on your device.
8. Delete unrecognized profiles
Some organizations use configuration profiles to set up devices with specific settings or install bespoke apps.
Hackers, however, can misuse this feature to install malicious apps on your iPhone outside of the official App Store. It’s good to check for any profiles you don’t recognize and delete them immediately.
To uninstall a configuration profile on an iOS device, follow these steps:
- Open the Settings app on your iOS device’s home screen.
- Go to General > VPN & Device Management.
- Under the Profiles section, you’ll see a list of all the configuration profiles installed on your device. Tap on the profile you wish to remove. Please note that profiles won’t be visible until at least one profile is installed.
- Tap on the Remove Profile button. If your device has a passcode, you’ll be prompted to enter it.
- A confirmation prompt will appear that asks whether you want to remove the profile. Confirm the removal. Restart your device to apply the changes.
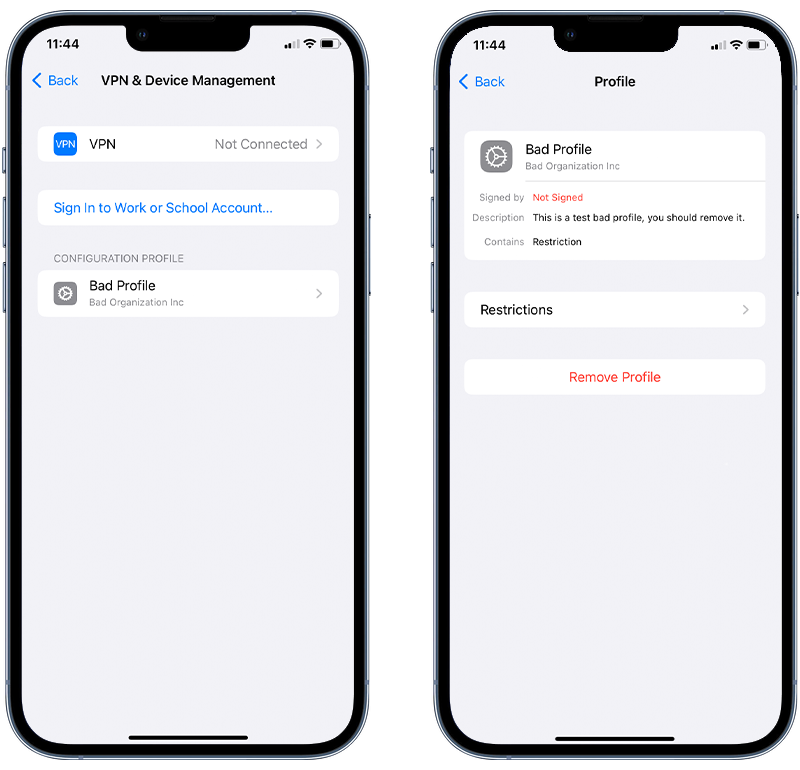
Fig 6. Deleting an unrecognized configuration profile.
9. Perform a factory reset
Even though it’s regarded as an extreme measure, wiping all data from your device with a factory reset is a surefire way to clean your iPhone of any spyware. This method erases all data from the device and reinstalls the latest iOS software, returning it to its original factory settings.
This is a last resort since it will remove all your photos, messages, and data as part of the process. You should therefore perform a backup of your device using iTunes, Finder, or iCloud before doing a factory reset to allow all your data to be restored later.
We recommend restoring your device from a computer. Using the “Erase All Contents and Settings” option in the Settings app may cause software issues if you have a specific type of spyware. Restoring via a computer is the best way to ensure your device remains operational.
Follow these steps to backup your device and then perform a factory reset:
- Open iTunes on your PC or Finder on your Mac.
- Connect your iOS device.
- Select your device when it appears.
- In the Summary pane, click Back up now and wait for the backup to complete.
- Once backed up, click Restore iPhone (or Restore iPad).
- Click Restore again to confirm.
- The device will then restore to factory settings and restart. This process can take several minutes to complete.
- When completed, you can restore all of your data from your previously created backup.
💡 Pro Tip: Make sure your computer is running the latest version of its operating system, and ensure your iPhone or iPad has the latest version of iOS or iPadOS. Also, ensure that your device is fully charged or keep it connected to a power source during the reset process.
How Does Spyware Get on an iPhone?

Now that you know how to remove spyware from an iPhone or iPad, we thought it would be a good idea to discuss the ways spyware or malware could find its way onto your device.
Generally, it’s not something that happens by accident, and it almost always means someone has physically tampered with your device.
This section will break down the five main tactics hackers use to install malware and spyware on iPhone and iPad devices.
1. Hidden spy apps
This type of spyware has been around the longest and gives hackers unrestricted access to the victim’s device. It can silently forward text messages, scoop up all of your photos, track your location, and even turn on your microphone remotely.
Fortunately, it is one of the more difficult spyware types for hackers to use since they would first need to jailbreak your device. Usually, this is not possible if you have an up-to-date iOS version.
If they did manage to jailbreak the device, then all they would have to do is download a spy app and hide it from view.
2. Keyloggers
We briefly discussed keyloggers above, but this relatively new spyware is becoming increasingly popular with hackers. This is mainly due to how easy it is to install compared to other spying tools.
Keyloggers typically take the form of a custom keyboard. For a hacker to install one of these, they would have to get hold of your device for a few minutes to install the malicious keyboard and set it to default.
3. Tracking apps
The App Store contains many legitimate family tracking apps, which can be used to share your GPS location.
Unfortunately, while most of these apps are well-intentioned, hackers often misuse them to track their victim’s location.
For your device to be affected by a tracking app, the person responsible would need physical access to it to download it from the App Store.
💡 Pro Tip: Review the apps with
4. Pegasus
The use of Pegasus was first discovered in 2016 and it is certainly on the more advanced end of the spyware spectrum. Developed by the Israeli cyber-arms company NSO Group, previous versions of Pegasus could infect an iPhone remotely by sending a malicious link via SMS.
Pegasus has a hefty price tag (allegedly millions of dollars), and it’s claimed that the spyware is only available to governments. As such, it’s doubtful that most iOS users will ever encounter a targeted attack through Pegasus.
5. iCloud spyware attacks
This type of hacking is not strictly spyware since no malware is installed on the device during the attack. However, it’s important to cover here, as iCloud hacking could be a way for a hacker to access information from your device when you sync data with iCloud.
In this attack, the hacker would log in to your iCloud account and view or download any data you have synced from your device. However, this attack is becoming less and less common, mainly due to security improvements made by Apple and two-factor authentication that is now mandatory for Apple IDs.
Now, hackers will need to know your Apple ID password and another piece of information (for example, a verification code sent to you via text message), which makes it a much more complex attack to pull off.
Stop hackers for good
Combat spyware and other cyber threats with Certo AntiSpy, the world's leading anti-spyware tool for iPhones and iPads.
How to Tell Whether Your iPhone Has Spyware
Concerned about iPhone spyware and want to find out whether you’re affected? Now that you know the removal steps, here are the top five things to look out for that may indicate someone is spying on your iOS device:
⚠️ Battery drain
Spyware or stalkerware works by recording specific activity on your iPhone, such as calls, texts, or photos you capture. In order to do this, the spy app will be constantly active in the background, which can eat through your battery fairly quickly and cause your phone to perform slowly.
It’s worth noting that iPhone or iPad batteries will typically degrade over time. However, suppose you see a sudden drop in battery life—this could indicate that something is running in the background and it’s certainly worth further investigation.
⚠️ Overheating
Spy apps consume a lot of resources while active on your mobile device. As such, they will typically make your device run a little hotter than normal and cause strange behavior in your device’s operating system.
Of course, there are many other reasons a device may heat up, but it’s a meaningful sign to look out for.
⚠️ High data usage
Have you noticed higher-than-expected data usage on your device? Most spyware will send recorded data to the hacker using your Wi-Fi or 4G/5G connection. So if your device is infected with spyware, your data usage could increase significantly.
Fortunately, on the iPhone, it’s easy to see which apps use your data. You can view the stats under Settings > Mobile Data.
If you find a suspicious app that uses lots of data, you should delete it immediately.
⚠️ Suspicious apps
Most spyware takes the form of a monitoring app. The advanced ones can be made entirely invisible, so you’ll need to run a spyware scan to uncover them. However, others work just like regular apps and can be identified by performing a quick visual check of installed apps.
Watch out for unknown or suspicious apps hidden in folders. A common tactic hackers use is to hide spy apps in a ‘Utilities’ folder or other places where their victims may not think to look.
Three Ways to Increase the Security of Your iPhone and iPad

Cover Image by rawpixel.com on Freepik
Nowadays, our phones and tablets hold a wealth of personal and work-related information. Keeping these devices safe is very important.
Here are three easy steps to improve the security of your iPhone or iPad, which make it harder for cybercriminals to gain unauthorized access.
✔️ Physically secure your iPhone and iPad
Restricting physical access is the first line of defense. Never leave your devices unattended in public places.
Also, use a strong passcode to lock your devices. A complex passcode contains digits, letters, and symbols, which make it difficult for prying eyes to guess.
Another way to protect your iPhone is to enable biometric identification like Face ID or Touch ID for an added layer of security.
✔️ Enable automatic updates
Enabling automatic updates on your iPhone or iPad is crucial for security because updates frequently contain patches for vulnerabilities that have been discovered since the last version was released.
Cybercriminals exploit these vulnerabilities to gain unauthorized access to devices and personal information
Automatic updates ensure that your device receives these critical fixes as soon as they are available, thereby minimizing the window of opportunity for attackers to compromise your phone’s security.
To enable auto-updates, go to Settings > General > Software Update and make sure Automatic Updates is set to On.
✔️ Regularly scan for spyware with Certo AntiSpy
Regularly scanning your phone for spyware is vital for maintaining security because it helps in the early detection and removal of malicious software that could be hiding in your device.
Spyware can compromise personal data, track your activities, or even take control of your phone for nefarious purposes. By conducting regular scans, you ensure that any potential threats are identified and eradicated promptly, keeping your sensitive information and the integrity of your device safeguarded.
Here’s how:
- Download Certo AntiSpy.
- Connect your iPhone to your computer.
- Click Scan.
- Click Remove next to any threats to restore your privacy.
Fig 7. Removing spyware from an iPhone using Certo AntiSpy.
Key Takeaways
As phone hacking becomes more and more widespread, it’s essential to take steps to protect your devices from potential security breaches. Luckily, there are a few simple ways to detect and remove spyware from your device—or even better, to prevent attacks before they occur.
Download Certo AntiSpy for iPhone to protect your phone against viruses and spyware. Use secure passwords and VPNs like NordVPN to make it harder for hackers to gain access. Update your phone regularly and be vigilant for suspicious apps on your device.