How To Remove A Hacker From My iPhone?

Published:

There are two common myths about iPhone security. The first is that iPhones don’t get viruses and the second is that these devices can’t be hacked.
While compared to other mobile devices, iPhones have a reputation for being very secure. Unfortunately, though, the truth is that phone hacking incidents are on the rise, and no smartphone is truly safe.
In today’s digital world, it’s more important than ever to protect your personal data. If you think your iPhone has been hacked, it’s important to act quickly to remove the hacker and secure your device.
In this article, we’ll walk you through the steps you can take to remove a hacker from your iPhone and keep your data safe.
Quick Links
- 1. Restart the iPhone
- 2. Update iOS
- 3. Use an Anti-Spyware App
- 4. Reset your Apple ID Password
- 5. Delete Unrecognized Profiles
- 6. Delete Unrecognized Custom Keyboards
- 7. Unpair Unrecognized Bluetooth Devices
- 8. Remove Additional Saved Face IDs
- 9. Disable Message Forwarding
- 10. Disable Calls on Other Devices
- 11. Factory Reset
Signs Your iPhone Might Be Hacked
Think your iPhone might be hacked? Here are some clear signs to watch out for:
⚠️ Unexpected battery drain: Malicious software can run in the background, consuming more battery than usual. Another sign is if your phone runs abnormally slow without any other known cause.
⚠️ High data usage: Spyware or malware can send data from your phone to a hacker’s external server. If you notice a sudden spike in data usage without a corresponding increase in your known activities, it might be a cause for concern.
⚠️ Unfamiliar apps on your phone: If you see apps on your phone that you don't remember installing, they might have been installed maliciously.
⚠️ Unusual account activity: Receiving unexpected two-factor authentication codes, password reset emails, or being locked out of your Apple ID account could indicate someone has access to your data.
Want to dive deeper? Click here to access our comprehensive guide, which offers all the insights you need to determine if you’ve been a victim of iPhone hacking.
How to Get Rid of Hackers on Your iPhone
If you’re concerned that your iPhone might be compromised, stay calm. Follow these essential steps to protect your device and personal information.
1. Restart the iPhone
The first step in removing a hacker from your iPhone is to shut it down and restart it. Restarting a hacked phone is a good idea for a few reasons:
➡️ End malicious processes: Malicious software might be running active processes on your phone, performing unwanted actions. Restarting the phone can disrupt these processes and deny hacker access to your device..
➡️ Clear out system cache: Over time, and especially if exposed to malicious websites or apps, your device might store harmful data in its cache. A restart can help clear out this cached data.
➡️ Remove a jailbreak: Certain types of iPhone spyware require your device to be jailbroken, a process that removes security restrictions on the device. A jailbreak will be reversed when you restart your device, in turn disabling any active spyware.
How to restart your iPhone:
- Press and hold the volume up or down button and the side button until the power-off slider appears.
- Drag the slider to switch off your iPhone.
- After switching off your iPhone, press and hold the side button again until the Apple logo appears.
2. Update iOS
Always keeping your phone updated with the latest iOS version is essential.
Updates often contain security patches for known vulnerabilities that hackers might exploit. Installing the latest version closes these gaps and strengthens your iPhone’s defenses.
Cyber attackers frequently target outdated software because they’re familiar with its weaknesses. Therefore, keeping your iOS up-to-date not only removes active threats, but also ensures that the latest security enhancements protect you and reduce the chances of future breaches.
Here’s how to check for iOS updates:
- Open your iPhone’s Settings app.
- Tap on General.
- Tap on Software Update.
- Your iPhone will check for available updates.
💡 Pro Tip: Always use a secure Wi-Fi network or mobile data when updating your device. We recommend avoiding public Wi-Fi networks when updating your iOS to keep your phone safe.
Also, if you're using your phone when you're out and about, use a virtual private network (VPN) when connected to public Wi-Fi. This will help to keep your personal information confidential.
3. Use an anti-spyware app
The best way to remove a hacker is by downloading an anti-spyware app and using that to scan for and remove hackers, viruses, and spyware.
Unfortunately, for Apple users, most anti-spyware apps that can be installed directly on iPhones or iPads are unable to properly scan the device for spyware or viruses.
The reason is that Apple’s operating system does not allow apps to access other apps or files on the device. For example, Instagram can’t access information stored in your banking app or any other app on your iPhone.
While this is great for general security and privacy, it’s not ideal for preventing phone hacking because the installed anti-spyware app can’t fully scan your phone for suspicious activity.
Don’t worry, though. Certo AntiSpy is an award-winning solution that is able to completely scan your iPhone to detect and remove spyware.
Certo Antispy does this by connecting to your iPhone or iPad via a computer, which enables it to perform a full and complete scan of the entire device.

💡 Pro Tip: Do you have a hacked Android phone?
Try Certo for Android. Our all-in-one app crushes spyware, stops intruders, and keeps you safe online. Download the free version from the Google Play Store today.
How to remove a hacker with Certo AntiSpy:
- Download Certo AntiSpy to your computer.
- Connect your iPhone via USB.
- Click Scan.
- Once complete, click Remove next to any threats detected.
4. Reset your Apple ID password
Your Apple ID is the gateway to your personal data and services associated with your device. If hackers gain access to it, they can retrieve backups, access your iCloud account data, make unauthorized purchases, and even lock you out of your device.
Changing the password immediately stops unauthorized access, ensuring the intruder can’t continue exploiting the account or make further changes using your credentials. It’s a crucial step in re-securing your digital identity and assets.
If you need to reset your Apple ID password, follow these steps:
- Go to Settings.
- Tap on your name (Apple ID, iCloud, iTunes, and App Store).
- Tap Sign-In & Security > Change Password.
- If you’re logged into iCloud and have a passcode enabled, you’ll be prompted to enter the passcode for your device.
If you can’t access your device, use a web browser:
- Go to iForgot.apple.com.
- Enter your Apple ID and click Continue.
- You must enter a code from your trusted device if you have set up two-factor authentication. You must enter your recovery key if you haven’t set up two-factor authentication.
- Enter a new password and confirm it.
- Click Change Password.
💡 Pro Tip: Keep the following in mind when resetting your Apple ID password
➡️ Your new password must be at least 8 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
➡️ Don’t use the same password for your Apple ID as you use for other accounts.
➡️ Change your Apple ID password regularly, especially if you think it may have been compromised.
5. Delete unrecognized profiles
Configuration profiles can be used by businesses and schools to set up specific settings and restrictions on devices.
However, hackers can exploit this feature and also install malicious code and profiles on your iPhone. Check to see if you have any unrecognized profiles and delete them immediately.
To uninstall a configuration profile on an iOS device, follow these steps:
- Open the Settings app on your iOS device’s home screen.
- Go to General > VPN & Device Management.
- Under the Profiles section, you’ll see a list of all the configuration profiles installed on your device. Tap on the profile you wish to remove. Please note that profiles won’t be visible until at least one profile is installed.
- Tap on the Remove Profile button. If your device has a passcode, you’ll be prompted to enter it.
- A confirmation prompt will appear, asking if you want to remove the profile. Confirm the removal. Restart your device to apply the changes.
6. Delete unrecognized custom keyboards
If you suspect that your iPhone has been hacked, you should check for and delete any unrecognized custom keyboards.
This is because a hacker could have installed a malicious keyboard on your device that can be used to track your keystrokes and steal sensitive information like passwords or credit card numbers.
To delete unrecognized custom keyboards on your iPhone, follow these steps:
- Go to Settings > General > Keyboard.
- Tap Keyboards.
- Tap Edit.
- Tap the red minus button next to any keyboard that you don’t recognize.
- Tap Delete.
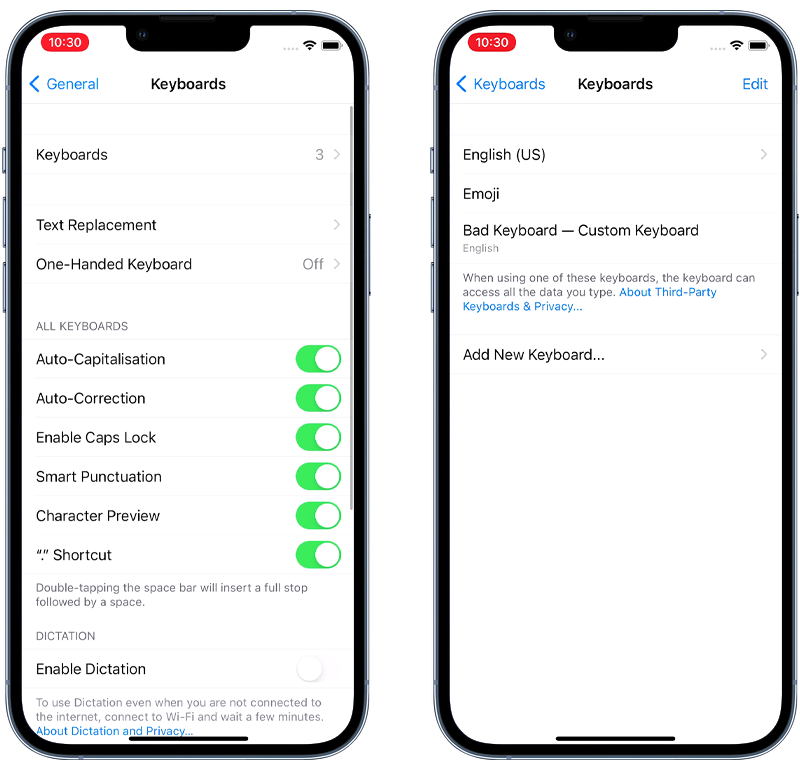
Fig 1. Locating a custom keyboard on iOS.
7. Unpair unrecognized Bluetooth devices
Bluetooth technology is everywhere—we often don’t even realize we’re using it. But Bluetooth is prone to hacking in certain situations and can give hackers access to your phone.
It’s crucial to unpair any unrecognized Bluetooth devices if you suspect your iPhone has been compromised. Here’s why:
⛔ Data access and transfer: Once paired, some Bluetooth devices can access sensitive data on your iPhone or even send data to your device.
⛔ Eavesdropping: Certain Bluetooth-enabled devices, especially headsets or car systems, can be used to listen to your calls and read your text messages.
⛔ Remote control: Some Bluetooth devices can exert control over certain iPhone functions, like taking over your keyboard, calls and audio functions.
To unpair unrecognized Bluetooth devices on your iPhone, go to Settings > Bluetooth and check for unfamiliar devices. If any are found, click on the (i) icon next to the device and select Forget This Device.

Fig 2. Checking for unrecognized Bluetooth devices on iOS.
8. Remove additional saved Face IDs
Stored Face IDs should be limited to your face only.
If you suspect your iPhone has been hacked, remove any additional saved Face IDs. This is because a hacker could have saved their face to your iPhone and could be using it to unlock your phone without your knowledge.
Here are some of the things that a hacker could do with an additional saved Face ID:
- Unlock your phone and access your personal information, such as contacts, photos, and messages.
- Make purchases with your Apple Pay account.
- Install device monitoring spyware so they can keep tabs on your activity remotely.
To check for and remove additional saved Face IDs on your iPhone, follow these steps:
- Go to Settings > Face ID & Passcode.
- If you see the option to Set Up an Alternative Appearance then only one Face ID is setup and no further action is required.
- If you don’t see Set Up an Alternative Appearance then a second Face ID is setup.
- To remove a second Face ID, tap Reset Face ID to remove all stored faces, then setup Face ID again.
9. Disable message forwarding
Message forwarding on iOS devices is a feature that allows texts and iMessages sent to one device to be automatically forwarded to another.
This is especially useful for people who own multiple Apple devices. With message forwarding enabled, you can receive and reply to messages from any device, even if they were initially sent to just one specific device.
This feature can be exploited to forward your messages to another device discreetly. A hacker can exploit this feature in many ways, including:
⚠️ A privacy breach: Hackers can read personal and private conversations.
⚠️ Obtaining 2FA codes: They can gain unauthorized access to accounts using intercepted two-factor authentication codes.
⚠️ Financial gain: A hacker could intercept bank alerts, one-time PINs (OTPs), and transaction details.
⚠️ Blackmail: With access to personal or sensitive messages and media, a hacker could potentially blackmail you.
⚠️ Impersonation: With access to your messages, a hacker could impersonate you and send spam or phishing messages to your contacts.
⚠️ Resetting your passwords: A hacker could request a password reset for one of your accounts, receive the reset link or code via message forwarding, and subsequently take over that account.
To disable message forwarding on your iPhone, go to Settings > Messages > Text Message Forwarding, and ensure it’s disabled or only enabled for devices you trust.
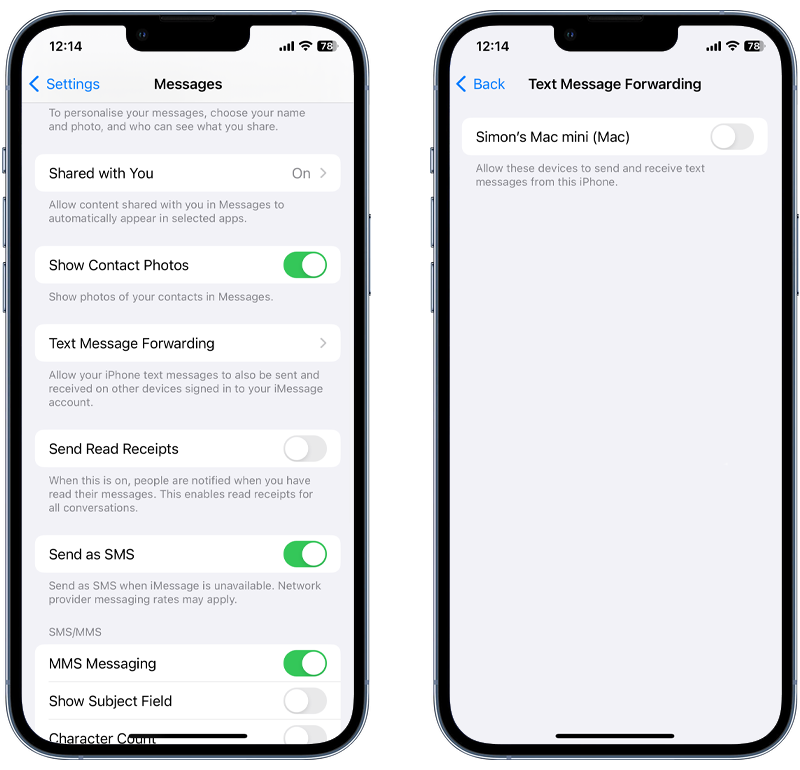
Fig 3. Disable Text Message Forwarding on iOS.
10. Disable calls on other devices
The ‘Calls on Other Devices’ feature on an iPhone allows you to make and receive calls on other devices that are signed in to the same Apple ID, such as your iPad, iPod touch, or Mac. This can be a convenient feature, but it can also be a security risk if it’s exploited by hackers.
Similar to message forwarding, hackers can exploit this feature to spy on you and steal valuable personal information.
If you suspect that your iPhone has been compromised and want to disable this feature, follow these steps:
- Tap on the Settings app on your iPhone.
- Scroll down and tap on Phone.
- Tap on Calls on Other Devices.
- Toggle off Allow Calls on Other Devices. This will prevent calls from being forwarded to any other devices signed in with the same Apple ID.
💡 Pro Tip: It’s also a good idea to check the devices associated with your Apple ID to ensure no unauthorized devices have been added.
11. Perform a factory reset
If all else fails, resorting to a factory reset can be your final defense. A factory data reset erases all the information, settings, applications, and data stored on your device, reverting it back to the exact state when you first took it out of the box. Doing this:
✅ Removes malware: It ensures that any installed malware, spyware, or unrecognized apps are removed from the device.
✅ Recovers the iOS: A factory data reset restores the device’s operating system (OS) and software to its original state, undoing any unauthorized system-level changes by hackers.
✅ Eliminates hidden threats: Even if some threats are dormant or hard to detect, a factory reset ensures they’re wiped out.
✅ Protects your data privacy: By erasing all data, you prevent continued unauthorized access to personal, financial, or business-related information stored on the device.
How to factory reset iOS devices:
- Open the Settings app.
- Tap on General.
- Scroll down and tap on Transfer or Reset iPhone.
- Tap on Erase All Content and Settings.
- If prompted, enter your iPhone passcode or Apple ID password.
- Confirm that you want to hard reset your device.
- Your iPhone will begin the reset process and then restart.
- Follow the on-screen instructions.
💡 Pro Tip: Backup Your Data
It's crucial to remember that a factory reset will delete everything on your device. This means photos, apps, messages, contacts—everything gets wiped.
Therefore, before you take this step, ensure you have a recent backup of all your essential data. Ideally, this backup should be scrutinized for signs of compromise so you don’t inadvertently restore malicious content onto the fresh system.
Key Takeaways
Phone hacking is a serious issue, but it is important to remember that you are not helpless.
This article outlined key things you can do to remove a hacker from your phone. These include:
- Making sure your iPhone is always updated.
- Changing your Apple ID password immediately if you suspect you’ve been hacked.
- Checking for and removing any spyware.
- Removing any profiles that look out of place.
- Ditching custom keyboards and disconnect unknown Bluetooth devices.
- Double-checking your saved Face IDs and removing any you don’t recognize.
- Disabling options like Message Forwarding and Calls On Other Devices.
- As a last resort, consider resetting to factory settings.
By following the steps outlined in this article, you can remove a hacker from your iPhone and keep your data safe. If you want to prevent your iPhone from being hacked in the future, check out this guide.