How to Fix a Hacked Android Phone

Updated:

In recent research, it was found that 98% of all smartphone malware attacks targeted Android devices.
If you have recently discovered that your Android phone has been hacked, we can only imagine how creeped out and worried you must be.
Knowing that someone has had access to your text messages, phone calls, and even your banking details is a scary thought that’s enough to send shivers down your spine.
If you are dealing with a hacked Android phone, there are some steps you can follow to fix it. These steps are quite simple to follow, so you should regain control of your phone in no time.
First, we’ll outline six steps you can follow right away if your Android phone is hacked. After addressing the immediate concerns, we’ll explain the nature of hacking, the indicators that your phone might be compromised, and the methods scammers use to hack Android devices.

Fix hacked Android for free
Download Certo Mobile Security now and fix your hacked phone in a matter of minutes.
6 Ways to Fix a Hacked Android Phone
If you’re convinced that someone has hacked your Android phone, there are some simple ways to fix it and ensure that no one has access to your personal or sensitive information.
1. Delete suspicious apps
Run through all your installed apps, including those in folders, and search for anything that doesn’t look right.
Uninstall any unknown apps that you didn’t install yourself or that look suspicious.
However, it’s important to keep in mind that there are several system apps on an Android phone that come pre-installed on the device. These apps might have names you don’t recognize, but aren’t necessarily malicious.
Before deleting an app you’re unsure about, check the web to see if it’s actually a legitimate app.
You can get to a list of all your apps by following these steps:
- Go to the Settings app on your phone.
- Tap Apps.
- Run through the list for any suspicious apps.
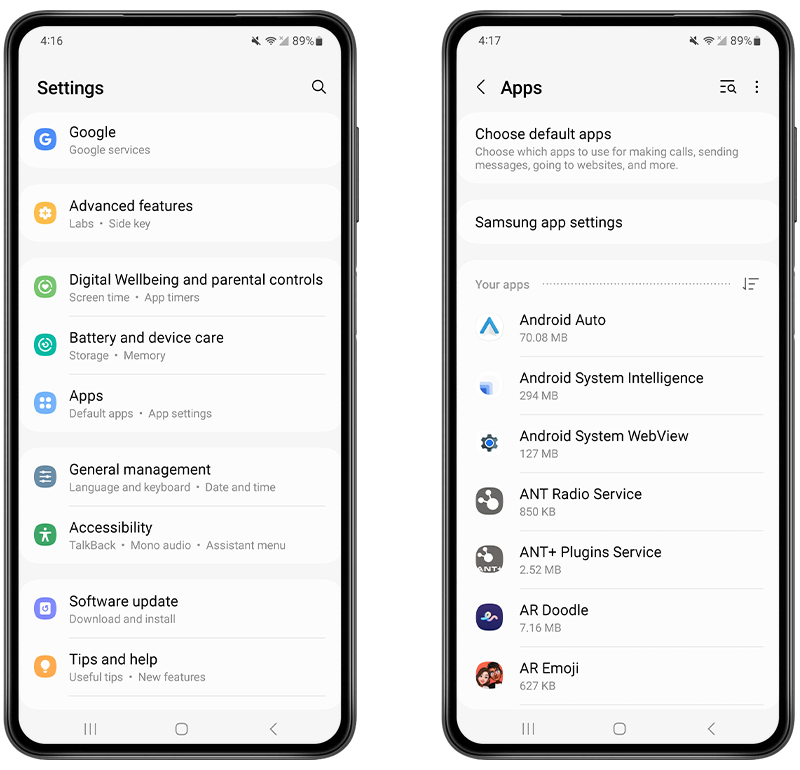
Fig 1. View installed apps on an Android device.
2. Change your Google account password
These days, many of our apps are linked to our Google account. In fact, your Android phone will typically need you to sign in to a Google account when you first set up the phone.
If you suspect someone has hacked your phone, you need to change your Google account password immediately, as this is a common way that hackers could access data from your phone.
You can change your password by following these steps:
- Open the Settings app.
- Tap on Google.
- Navigate to Manage Your Google Account.
- Visit Security.
- Go to Signing in to Google.
- Find Password and then change it to something new.
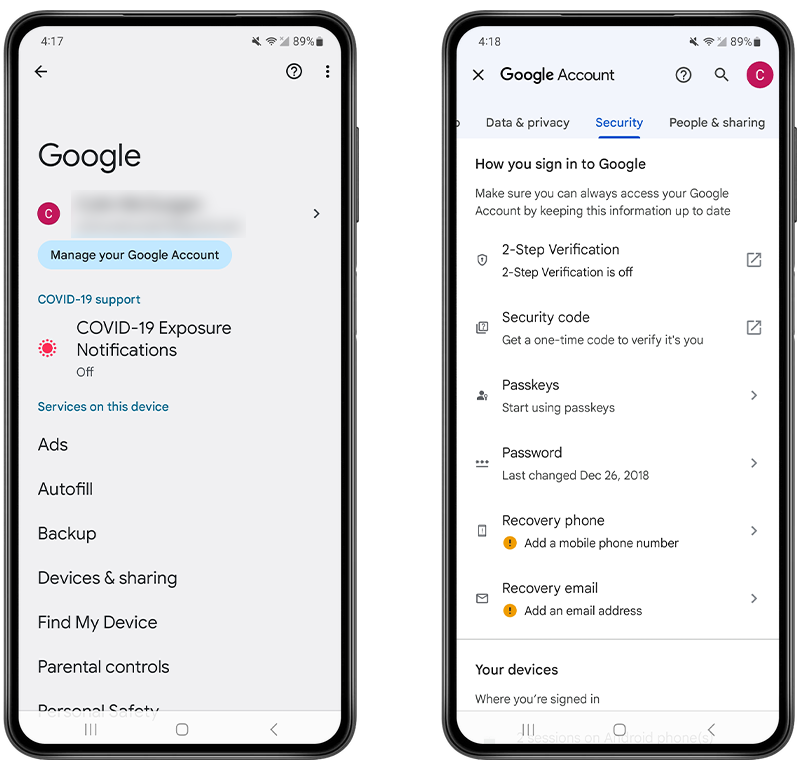
Fig 2. Changing your Google password.
When setting any password for online accounts, be sure to use something that would be difficult for a hacker to guess. Don’t use names of family members, pets, or memorable dates as your password.
If the hacker is someone close to you, which is often the case, they may be able to guess your password based on what they know about you. Ensure that your password is strong enough to prevent people close to you from getting into your phone.
2-Step Verification is a must for any Google account, protecting your account from unauthorized access even if someone guesses your password. Check your Google account settings and make sure it’s enabled.
3. Remove administrator access
Often, a hacker will install apps with administrator access to gain control over even more data on your phone and make it more difficult to remove the malware.
By deactivating administrator access, you can disable any unknown apps that might be used to spy on your phone.
You can do this by following these steps:
- Open Settings.
- Use the search tool to find Device Admin Apps or Device Administrators.
- If you see any unknown apps that you don’t recognize, toggle administrative access off or select the app and choose the Deactivate function.
- You can then uninstall the app like any other app.
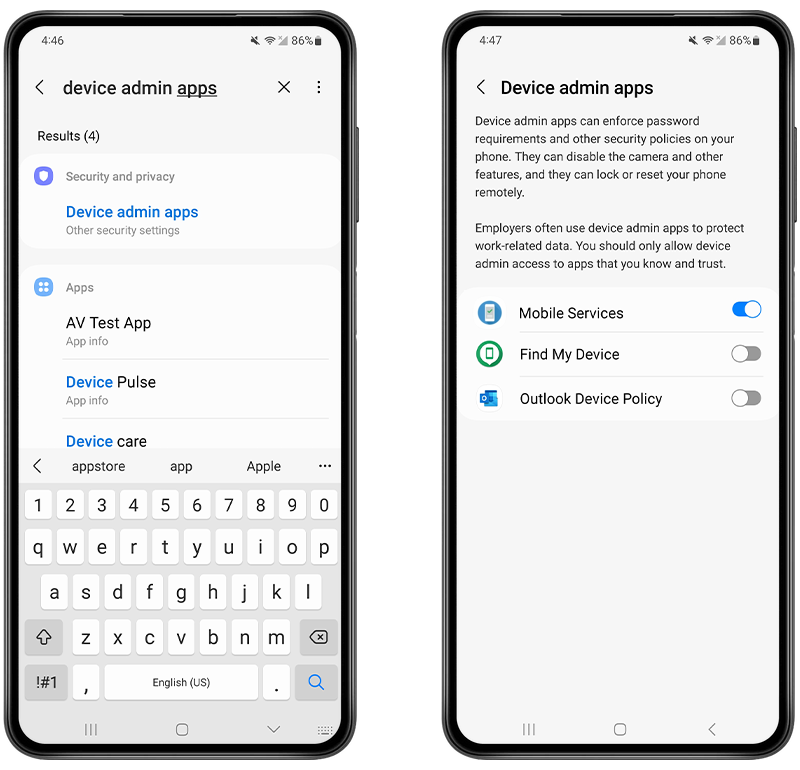
Fig 3. Disabling Device Admin Apps.
4. Download antivirus software
Scanning your phone for suspicious apps and files is simple with the Certo Mobile Security app, which can help you uncover and remove malware and cyberthreats for good. All you need to do is download the free app from the Google Play Store and tap the Scan button.
The app will scan all your apps and files to look for malicious software that could be used to hack and spy on your phone.
Once the scan is complete, the app will let you know if any suspicious apps or files have been found, and you can remove them with one simple tap.
You can also set the app to run regular scans of your phone, giving you peace of mind that you can identify any hacking in the future before it becomes a problem.
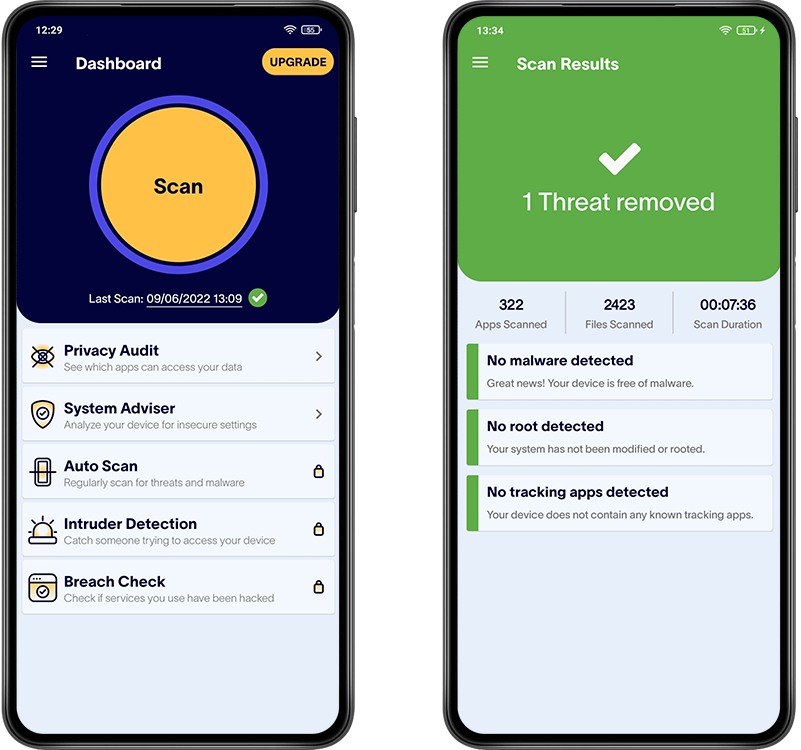
Fig 4. Certo Mobile Security for Android.
5. Clear your Android phone cache
Even after deleting suspicious apps, malicious code can still hang around in your cache. So, it’s a good idea to clear it.
Clearing your phone’s cache can be beneficial if you suspect hacking because it removes potentially malicious data that hackers may use or have left behind.
Cached data can be exploited to gather personal information, execute repetitive malicious actions, or cause app misbehaviors.
How to clear cache for an individual app
- Open the Settings app on your Android device.
- Navigate to Apps or Applications (this may vary depending on your device).
- Scroll through the list and find the app whose cache you want to clear.
- Tap on the app’s name.
- Tap on Storage.
- Tap on Clear Cache.
Note: If you tap Clear Data, you’ll remove all data related to the app, which might include saved games, settings, etc.
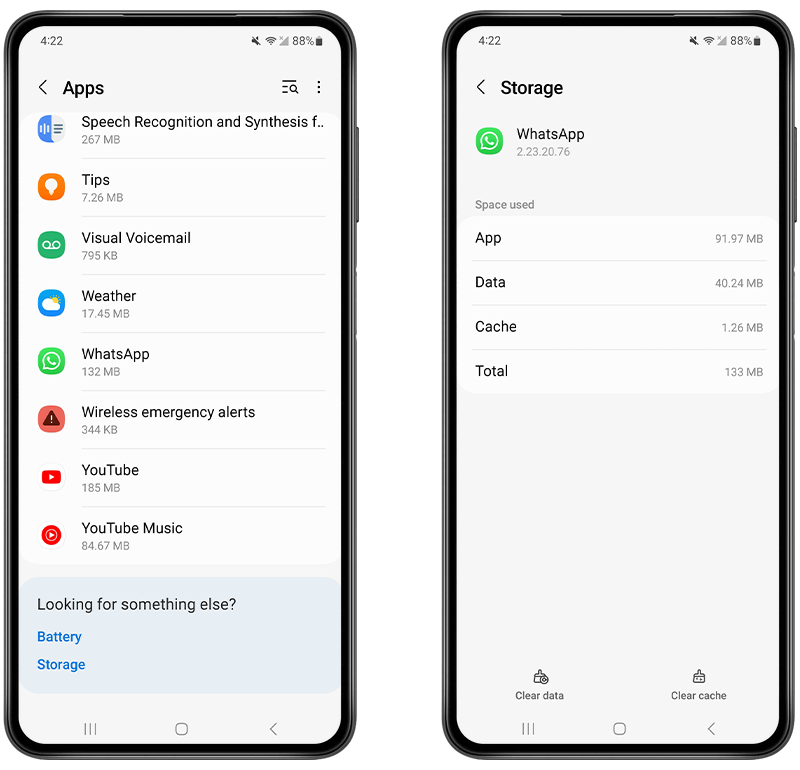
Fig 5. Clearing the cache for an individual app.
How to clear system cache (cache partition)
The process to clear the system cache may vary depending on the device manufacturer, model, and Android version. Here’s a general guide for devices with a built-in recovery mode:
- Turn off your Android device.
- Boot into Recovery Mode. This usually involves holding down a combination of buttons (like Volume Up + Power) as the device starts. Theexact combination varies by device, so you may need to look it up for your specific model.
- Once in Recovery Mode, use the volume buttons to navigate and the power button to select.
- Highlight and select Wipe cache partition or Wipe device cache or something similar.
- Once the process is complete, select Reboot system now.
💡 Note: Clearing the system cache won't delete any personal data or settings, but always ensure you have important data backed up before performing any system-level operations.
If you're unsure about any step or if you have a specific device model in mind, always refer to the device's official user manual or support website for precise instructions.
6. Do a factory reset
A factory reset restores your Android phone to the state it was in when you first bought the phone.
What’s useful about a factory reset is that it completely removes any malicious apps like spyware.
You may be worried about losing your data in a factory reset, but if you back up your device to Google before the reset, you can restore all your data and settings when the factory reset is complete.
Android users can follow these steps to safely perform a factory reset:
- Back up your data and familiarize yourself with the restore process.
- Turn off your phone and hold the Power and Volume Up buttons (or Power and Volume Down on some devices) until you see the Android logo.
- Recovery mode will load, and you can then use the Volume Down button to navigate to Wipe data/factory data reset.
- Wait for the factory reset to finish, and your phone will reboot.
Signs Your Android Phone Has Been Hacked
If you’re not entirely sure whether your Android phone is hacked, here are some signs to look out for:
🔋 Your battery drains faster than usual: When there are suspicious apps like spyware on your phone, the device has to run more tasks than ever before. Running all these tasks could cause your battery to drain very quickly.
🔥 Your phone is getting hot: All the extra processes an Android phone must run if it’s been hacked will put your phone under pressure. This can cause it to heat up more than normal.
📈 Your data usage increases: If someone has hacked your phone, much of your private data will be transferred from your Android phone to the hacker. This transfer can affect your data usage. If you notice that your data usage has suddenly increased, you may have been hacked.
📲 You start noticing performance issues: If your smartphone takes a long time to shut down or is unusually slow, this could be a sign that you’ve been hacked. All the extra processes running in the background of a hacked phone can slow it down and prolong the shutdown process.
☢️ Your phone is rooted, but you didn’t do it: Rooting an Android phone means removing the phone manufacturer restrictions. If you discover that your phone has been rooted and you didn’t do it yourself, it’s likely someone has hacked your device.
It’s worth noting that these aren’t all necessarily signs that your phone is hacked. They could be due to other reasons, such as a technical fault or the age of your device.
Use USSD Codes To Check If Phone Is Hacked
Unstructured Supplementary Service Data (USSD) refers to a protocol in the Global System for Mobile Communications (GSM). It allows users to communicate with their mobile network providers through text-based messages.
Essentially, USSD codes are sets of characters that, when entered, prompt the network to provide certain information or execute specific functions.
While USSD codes can offer insights into your phone’s operations, they don’t directly indicate if your phone has been infected with malware. However, they can be useful tools in understanding and diagnosing your device’s behavior, which can be a great way to find evidence of a hacker.
Here are some USSD codes that can help you determine if your phone is being hacked:
🔺Dial *#06# to get your IMEI number
Every mobile device has a unique code called the International Mobile Equipment Identity (IMEI). While the IMEI itself doesn’t indicate whether your phone has been hacked, it’s essential to keep a record of it.
If your device ever gets compromised, having the IMEI on hand is crucial for official reports, such as filing a police complaint. Before exploring any other codes related to phone security, you can quickly find out your device’s IMEI by dialing *#06#.
🔺 Dial *#62# to see if your calls are being forwarded
When you dial *#62# it reveals any forwarding settings for your messages and calls—like where they’re sent if your phone is off or out of range.
If a number appears in response, it might just be your voicemail! But if you don’t recognize it, it’s a sign that you’ve been hacked. Once you’ve established who your calls are being forwarded to, you can turn off all call forwarding. To do this, simply dial ##002#.
🔺Using the Netmonitor Utility Code: ##197328640##
What is a Net Monitor?
A Net Monitor is a tool that analyzes network data packets. It keeps track of all data your phone sends and receives, including location, calls, and other communications.
Why use this code?
On some devices, by using this code, you can potentially find evidence that someone has gained unauthorized access to your phone.
How to use the code
- Dial ##197328640## on your phone.
- You’ll be presented with a menu. Navigate to UMTS Cell Environment, then select UMTS RR information.
- An ID specific to your cell will appear. Note it down.
- Press your phone’s back button twice to return to the main menu, then navigate to MM Information and select Serving PLMN.
- Note down the displayed local area code.
- Visit a Netmonitor tracking website, such as https://opencellid.org.
- Enter the cell ID and local area code you’ve recorded.
- The website will display location details of any devices potentially linked to yours.
⚠️ Always be cautious and ensure you’re using such tools ethically and within the bounds of the law.
How an Android Phone Can Be Hacked
Let’s look at the most common ways Android phone hacking takes place:
Installing spyware and other malicious software
If a hacker gains physical access to your device or sends you a malicious file, they could install a hidden spyware app and use it to continuously track your activity.
Through spyware, a hacker can:
➡️ Monitor and record your calls.
➡️ Read your text messages.
➡️ View your photos and videos.
➡️ Access your location.
➡️ View your browsing history.
Sometimes, spyware is so sophisticated that you cannot detect it simply by visually checking for suspicious apps.
Instead, you may want to use a spyware detection app, like Certo Mobile Security, that uses award-winning technology to detect and remove spyware on Android phones. Certo is available for free from the Play Store here.
Social engineering and phishing
How would a hacker install spyware on your phone without accessing it physically? Through social engineering or phishing scams.
These types of scams typically involve a hacker sending you a text message or email that encourages you to follow a link.
Once you visit this link, you may be prompted to enter your personal information into a website or to download an attachment.
By following a link and entering your login information, you could be giving a hacker all they need to get into your phone.
And by downloading an unknown attachment, you could install malware onto your phone that hackers can use to gain access without physically touching it.
If you are aware of what phishing emails and texts may look like, you might be amused at what is being sent your way.
Check out this questionable phishing email trying to convince the recipient that Mark Zuckerberg wants to give them money:
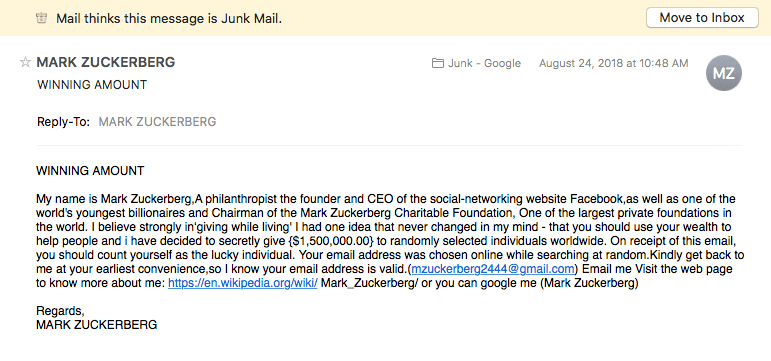
Fig 6. Example of a phishing email.
Accessing your Android device via an unsecured public Wi-Fi network
If your phone is connected to an unsecured Wi-Fi network like the type you would find in a public space, hackers could access data on your phone this way.
Hackers can intercept the communication between your phone and the public Wi-Fi network to access and steal your usernames and passwords, which they can use to get into your device or accounts.
In just 16 minutes, a man was able to hack a public Wi-Fi hotspot and could’ve stolen data from those who were connected to it.
However, while this wasn’t a malicious attempt—he was trying to raise awareness—it shows just how easy it would be for a hacker to access data from your phone via an unsecured public Wi-Fi network.
How to Improve Your Android Phone’s Security
If your phone is hacked then your first course of action should be to fix it straight away. However, it’s still important to be aware of some security best-practices that you can apply to protect your device going forward.
Here are some essential security tips you should follow to ensure your phone doesn’t get hacked in the first place:
✅ Don’t leave your phone unattended in a public space. If someone has physical access to your phone, it’s a lot easier for them to install apps that can be used to monitor your activity.
✅ Use a virtual private network (VPN) when connecting to unsecured public Wi-Fi networks. This will prevent anyone from being able to intercept your communications.
✅ Use a biometric authentication method on your lock screen, which means only your face or fingerprint can unlock your phone. This is much stronger than any password could be.
✅ Use a password manager to store all your passwords in one place while keeping them protected from prying eyes. We recommend NordPass.
✅ Only download apps from the official Google Play Store, as it is more likely that these apps are legitimate. Avoid downloading apps from other sources.
✅ Never open links or download attachments if you don’t know exactly what they are or who sent them.
✅ Keep your operating system updated. If there are any software updates available, always be sure to install them. Operating system updates can prevent hacking and will often disable any active malware already on your phone.
Final Thoughts
The digital age has brought along immense benefits, but it’s also accompanied by challenges, particularly in the form of cyber threats. Android phones, given their popularity and open-source nature, are especially vulnerable targets.
However, with knowledge and the right tools, you can defend yourself against most hacks and enjoy the convenience of your smartphone without compromising on security.
While there are various measures you can implement to safeguard your device, utilizing reliable security tools like Certo Mobile Security can make the process more manageable and effective. Remember, a combination of awareness and the right resources will help ensure your phone stays hack-free. Stay informed, stay safe.

Free anti-spyware for Android
Certo Mobile Security crushes spyware, stops intruders and keeps you safe online.
Frequently Asked Questions (FAQs)
Can you fix a hacked Android phone?
There are certain steps you can take to protect your Android phone from being hacked, and you can also fix it quite easily..
Using an app like Certo Mobile Security can help you detect and remove any apps or files that are being used to hack your phone.
You can also fix a hacked Android device manually by reviewing app permissions, removing suspicious apps, and/or performing a factory reset.
What are the signs of a hacked Android phone?
Some of the signs of a hacked phone include:
- Your phone getting very hot.
- The battery drains faster than usual.
- You have high data usage.
- A phone performance issue, such as the phone being slow or taking a long time to shut down.
- Someone knows something that you have only communicated via your phone.
What happens if your Android phone is hacked?
If your Android device has been hacked, the culprit could obtain access to all your personal and sensitive information, such as login details, your photos and videos, and your Internet and social media activity.
If you notice any telltale hacking signs, it is best to act swiftly to remove any spyware and lock the hacker out of your device.