How to Check for Malware on iPhone

Updated:

Our smartphones have become our constant companions, with the average person checking their phone about 144 times a day. Given this heavy usage, it’s no surprise they store a vast amount of sensitive information.
This wealth of information makes our phones a prime target for hackers. They aim to sneak harmful software, known as malware, onto our devices to access and misuse our data.
In this article, we’ll guide you on how to identify, remove, and protect your iPhone against malware, which will ensure that your personal information remains secure and under your control.
How to Detect Malware on an iPhone
Checking an iPhone for malware can be a tricky task due to the closed nature of iOS.
However, there are several steps you can take and signs you can look out for to identify a possible malware infection:
Check for unusual activity
Your iPhone may exhibit unusual behavior, such as sudden crashes, battery drain, unexplained data usage, or unfamiliar apps that appear on your device.
Let’s dive deeper into the various types of unexpected behavior displayed by Apple devices infected with malware.
🔺 Finding suspicious apps you didn’t install: Discovering unfamiliar apps on your device that you don’t recall installing could be a sign of malware. This is because malware is capable of installing additional malicious apps to compromise your device.
Some examples of known malicious apps to look out for are “Cydia”, “Sileo”, “Checkra1n”, “SystemCore”, “SystemUpdate” and “Phone Monitor”.
💡 Pro-tip: Check your iPhone settings menu for third-party apps
You can inspect your apps through the Settings menu. From your home screen, simply open Settings and scroll down to identify any apps appearing in the menu that you didn't install.
To view a list of apps you've purchased, open the App Store and tap on your profile icon. Select 'Purchased' to see a list of all your acquired apps.
🔺 Your iPhone is overheating: While occasional overheating can occur during intensive use, consistent overheating may signify malware operating in the background and consuming significant system resources.
🔺 Your data or call usage is higher than usual: An unexplained spike in data or call usage may indicate malware transmitting data to or communicating with remote servers.
💡 Pro-tip: How to check your data usage on an iPhone
Check overall data usage:
- Go to the Settings app.
- Scroll down and tap on Cellular or Mobile Data (the terminology might vary depending on your region).
- Under the Cellular Data section, you can see your current data usage. This shows the total data you've used in a cellular data cycle.
Check data usage per app:
- In the same Cellular or Mobile Data menu, scroll down to view the data usage per app.
- Each app listed shows the amount of cellular data it has used.
- You can toggle off cellular data for specific apps to reduce data usage.
🔺 Your iPhone’s battery life doesn’t last as long as it used to: Drastic reductions in battery life may be due to malware processes running in the background and consuming power at a higher rate.
🔺 Your apps crash: If your apps start crashing frequently, it may be due to malware interfering with the apps’ normal operations.
🔺 Pop-up ads: Random pop-up ads, especially those prompting you to install additional apps or claiming you’ve won a prize, could be a sign of adware or malicious software.
🔺 Your phone storage is filling up: Unexpectedly running out of storage might be caused by malware storing large amounts of data on your device or installing additional malicious apps.
💡 Pro-tip: Check the amount of storage space on your Apple device
Accessing storage settings:
- Go to the Settings app on your iPhone.
- Scroll down and tap on General.
- Now tap on iPhone Storage.
- In the iPhone Storage section, you'll see a bar at the top that displays your used and available storage.
- Below the bar, you'll find a list of apps along with the amount of storage each app is using.
Each of these signs could indicate a potential malware infection, but other nonmalicious issues can also cause them. It’s advisable to investigate any unexpected behavior on your iPhone and consult with Apple support if necessary.
💡 Expert Insight: Is your phone jailbroken?
Any complete discussion about the telltale signs of malware on Apple devices needs to touch on jailbreaking.
Jailbreaking refers to the process of removing the restrictions imposed by Apple on an iPhone, which allows the user to install unofficial apps, tweaks, and themes that are not available on the official Apple App Store.
The process of jailbreaking itself relies on exploiting vulnerabilities in iOS. The vulnerabilities that arise due to jailbreaking make your phone an easy target for malicious software. We highly recommend not jailbreaking your device.
It’s possible that someone else might have jailbroken your iPhone. If that’s something you are worried about, find out how to tell whether your iPhone is jailbroken.
Run a malware scan
Once you have checked your phone for unusual activity, we recommend that you install an antivirus app to check for any malware attacks on your device.
Here at Certo, we’ve developed a tool that allows iPhone users to quickly and easily perform thorough scans of their devices and uncover data-stealing malware.
Certo AntiSpy can detect the following:
✅ Malware installed on your device.
✅ Jailbreaking (a method hackers use to bypass Apple’s security and install spy apps).
✅ GPS location tracking apps (including legitimate apps you didn’t know were tracking you).
Here’s how to use Certo AntiSpy to keep your iPhone safe and secure:
- Download Certo AntiSpy: Download and install Certo AntiSpy antivirus software on your computer.
- Plug your iPhone into your computer: Connect your iPhone to the computer where Certo AntiSpy is installed with a USB cable.
- Run a scan: Once you’ve connected your iPhone, open Certo AntiSpy and start the scan. The software will then analyze your iPhone and check for signs of malware, spy apps, and system vulnerabilities.
- Remove any threats: Once you’ve run the scan, Certo AntiSpy will show you the results. Here, you will be able to remove any suspicious files with a click of a button.
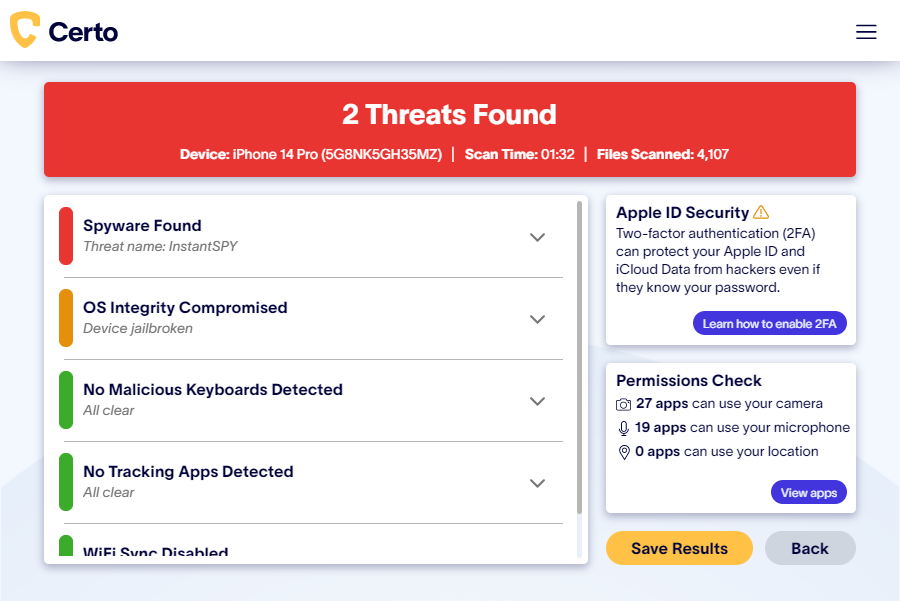
Fig 1. Finding hidden malware on an iPhone with Certo AntiSpy.
Other steps you can take to check for iPhone malware
➡️ Check for unrecognized profiles
On iOS, Configuration Profiles can be a way for hackers to install malicious apps or change settings on your device. To check, go to Settings > General > VPN & Device Management. If you see any unfamiliar profiles, it could be a sign of malware.
➡️ Check if Developer Mode is enabled
This allows developers to connect their iOS devices to a computer in order to install an app for testing. However, it can also be abused by hackers as a way to install malware. If Developer Mode is enabled on your device but you’ve never used it for development then it could be a sign that someone has installed a malicious app.
To check, go to Settings > Privacy & Security and look for an option that says Developer Mode. If you do not see the option then Developer Mode has never been active on your device.
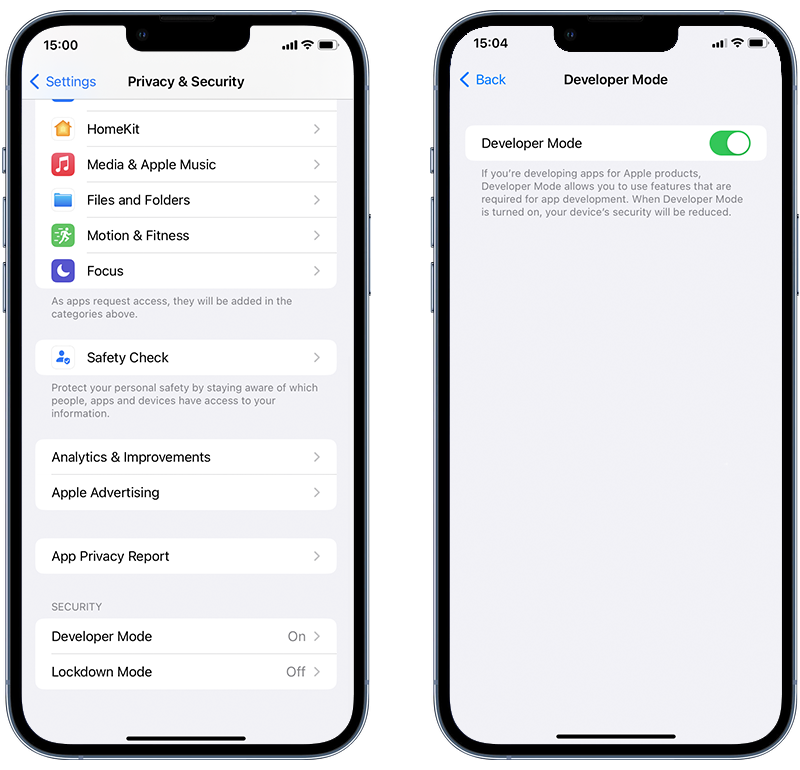
Fig 2. Checking Developer Mode on iPhone.
➡️ Check app permissions
Look through the permissions of your installed apps in Settings and ensure they align with what you expect.
Here is how to check app permissions on an iPhone:
- Open the Settings app on your iPhone.
- Scroll down through the settings menu to find the list of installed apps.
- Tap on an app to view its permissions.
- You’ll now see a list of permissions the app has requested, such as access to the camera, microphone, photos, and more.
- The permissions that the app currently has, will be toggled on. You can change the permissions by toggling the switches on or off.
- If you toggle a permission off, the app will no longer have access to that particular feature on your iPhone.
How to check privacy settings:
- Alternatively, you can check permissions by category. Go back to the main Settings menu and tap on Privacy & Security.
- Here, you’ll see categories like Camera, Microphone, Photos, etc.
- Tap on a category to see which apps have requested access and to change the permissions.
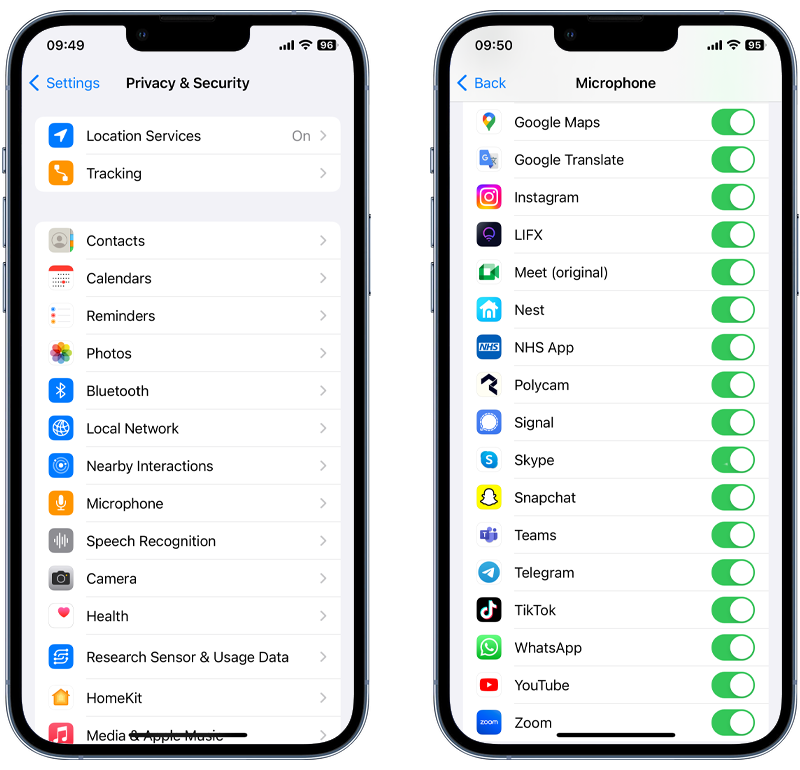
Fig 3. Reviewing which apps have access to your microphone on iOS.
➡️ Contact Apple Support
If you’re still concerned, you should contact Apple Support or visit an Apple Store to have your device professionally looked over.
How to Remove Malware from Your iPhone
If you have recognized any telltale signs of malware installed on your phone, don’t worry! Below, we’ll show you how to remove this malicious software from your phone.
At a glance: How to remove malware from your phone
✅ Update your iOS
✅ Restart your device
✅ Clear your browser history and data
✅ Remove any suspicious apps
✅ Restore your iPhone
✅ Factory reset your iPhone as a last resort
We’ll explore these in more detail below.
➡️ Update your iOS to the latest version
Apple frequently releases iOS operating system updates that include security patches to fix bugs and vulnerabilities that malware could exploit.
To update your iOS, go to Settings > General > Software Update. If an update is available, follow the on-screen instructions to download and install it.
➡️ Restart your device
Restarting your iPhone can help stop malicious processes running in the background and can even remove some exploits, such as a jailbreak.
To restart, hold down the side button and either of the volume buttons until the power off slider appears.
Once the device is off, hold the side button again until you see the Apple logo appear, which means that it is turning back on.
➡️ Clear your iPhone browsing history and data
Clearing your browsing data can help if malware has gained access via malicious websites or web-based scripts.
Go to Settings > Safari > Clear History and Website Data.
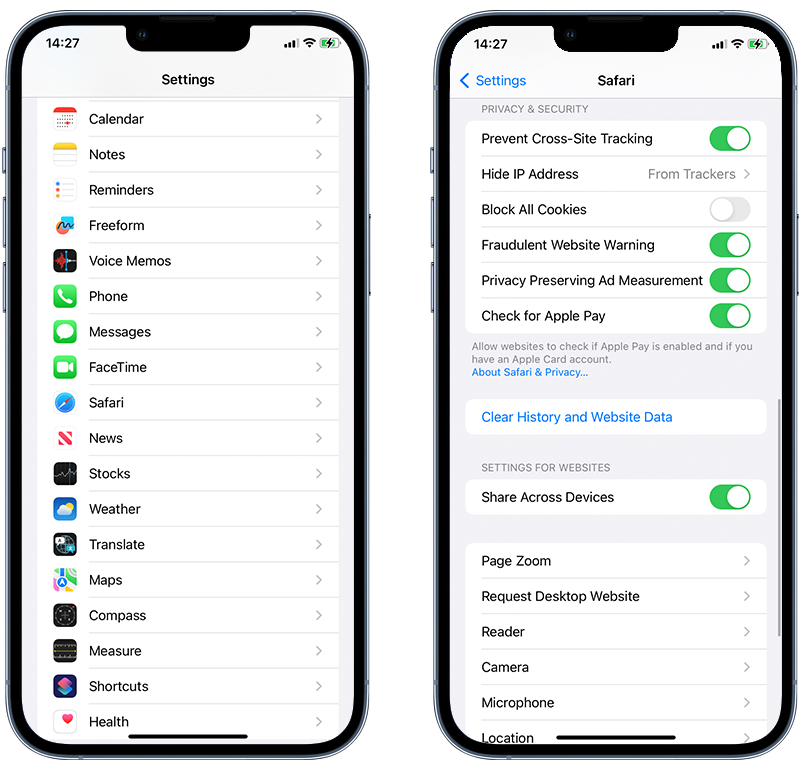
Fig 4. Clearing history and website data for Safari.
➡️ Remove any suspicious apps
If you’ve installed apps from outside the App Store that behave suspiciously, it’s advisable to delete them.
Press and hold the app icon until a menu appears, then select Remove App or Delete App.
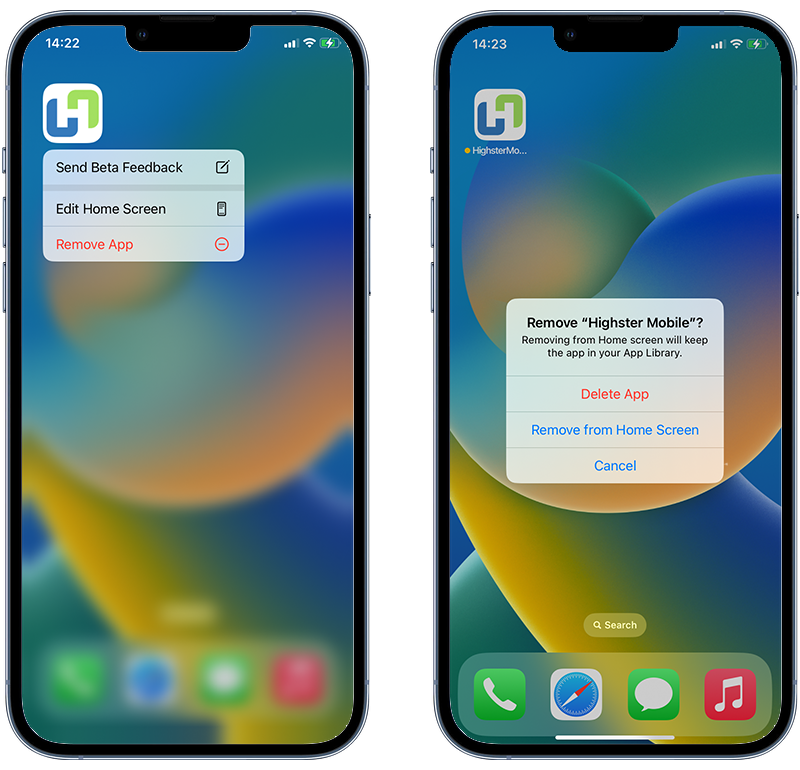
Fig 5. Removing a suspicious app from an iPhone.
Alternatively, go to Settings > General > iPhone Storage, find the suspicious app, tap on it, and select Delete App.
➡️ Restore your iPhone
If you’ve recently backed up your iPhone, and you suspect malware infected your phone after that, you can restore your iPhone to your previous iCloud backup.
To do this, follow Apple’s official guidance on their website here.
➡️ If necessary, factory reset the iPhone
As a last resort, a factory reset will erase all data and settings from your phone, including any malware. Before you proceed, ensure you have a backup of your data.
Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings. Follow the on-screen instructions to complete the process.
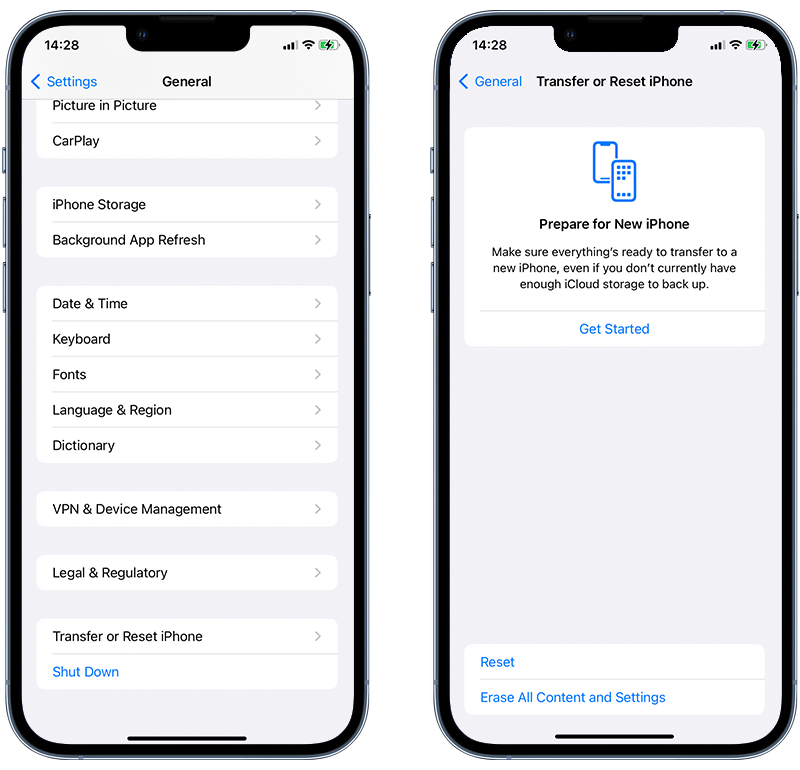
Fig 6. Performing a factory reset on an iPhone
💡 Expert insight: Related guides
If you suspect you have been hacked and need more help—check out our guide on what to do if your iPhone has been hacked. If you clicked on a phishing link, here is our expert guide on securing your phone after a phishing attack.
How to Keep Your iPhone Safe from Malware in the Future

Now that you know how to spot and remove malware from your device, it’s essential to learn more about what malware is and the kinds of malware that can get access to Apple mobile devices.
Understanding malware will help you keep your iPhone safe. In the next section, we’ll help you do just that. Lastly, we’ll share some tips on how to protect your iPhone from future potential threats.
Find and remove iPhone malware fast!
Scan your iPhone with Certo AntiSpy and uncover any hidden malware lurking on your device.
What is iPhone malware?
Similar to their Android counterparts, there are many different types of malware that target iPhones.
Some require the hacker to install it onto your device, while others exploit vulnerabilities in existing (and entirely legitimate) apps you already use regularly. Let’s take a look at these different types now:
⚠️ Spy apps
Spy apps are commercially available tools that allow someone to monitor an iPhone remotely–sometimes costing as little as $30.
These are easily accessible and simple to use, requiring very little technical knowledge to set up. When someone gains physical access to the device, they can be installed onto most phones in just 2 minutes.
This means that anyone can potentially be a hacker should they want to. Spouses commonly use these apps to spy on their partner to read their messages, track their GPS location, and listen in on phone calls.
Once this malware has been installed onto the device, it is almost impossible to detect as it can be invisible and remain completely hidden from the victim.
⚠️ Rogue Enterprise apps
If a hacker is unable to install a spy app on their victim’s iPhone, then they may use a rogue Enterprise app.
The Enterprise app program is meant for businesses who want to develop bespoke in-house apps for internal use. This appeals to hackers because Enterprise apps do not need to pass Apple’s strict App Store review process and can, therefore, be used to distribute malware.
This method is much easier to deploy onto a victim’s iPhone compared to a spy app, but the hacker would need to trick the victim into installing the app onto their device.
This is usually done by using some form of social engineering, with the hacker posing as someone else with a legitimate reason for the victim to install their app. You can learn more about this type of hack here.
⚠️ Exploiting existing apps
Some more organized and high-level hackers are now developing exploits for specific existing apps that are installed on most people’s iPhones and used regularly.
An example is the WhatsApp hack which exposed a weakness in the app’s file-sharing features. Another example is a vulnerability discovered in the Apple Mail app, which was used to hack iPhones.
Both of these cases allowed hackers to spy on their victims’ iPhones remotely. It’s easy to see just how dangerous malware like this can be, given how widely used these two apps are.
⚠️ Zero Day malware
The most elite hackers constantly seek ways to exploit devices and apps for personal gain. Zero Day malware is the most advanced type of hacking and requires intricate knowledge of the iPhone’s operating system and firmware.
This threat is based on discovering new weaknesses and exploiting them on a mass scale before the developer even realizes what is happening and long before they can fix the problem—which is why they are given the name ‘Zero-day’ exploits.
Once these threats have become public knowledge, developers and cybersecurity companies can usually reverse-engineer the malware so that it can be detected and prevented.
Final Thoughts: How to Keep Your iPhone Safe from Malware
The best way to keep your iPhone safe is to avoid malware in the first place. Here are some simple steps to protect your device:
✅ Turn on automatic updates for iOS to get the latest security fixes.
✅ Regularly check your device for malware with a trusted antivirus app.
✅ Don’t jailbreak your iPhone; it removes crucial security protections.
✅ Only download apps from the App Store so you know they are safe.
✅ Don’t click on strange links—they might take you to harmful websites.
✅ Back up your data regularly so you don’t lose anything important.
✅ Ignore strange text messages on iMessage to avoid scams.