How to Block Hackers from Your Phone

Updated:

Hackers are out there, looking for the smallest chink in your armour that will enable them to sneak in the backdoor and steal your personal information or spy on your activities. For the capeless superheroes fighting cybercrime, it can seem like an impossible task to keep up with the new ways that criminals are attempting to hack into their victims’ devices.
As a result, while the authorities are playing catch up with the cybercriminals, it is up to ordinary citizens to remain vigilant and block hackers as best they can. The question is, what can you do to stop them?
Here are our 10 tips to keep the hackers out:
Table of Contents
- 1. Update Your Phone and Apps
- 2. Enable 2-Factor Authentication
- 3. Download a Good Security App
- 4. Use a Complex Passcode
- 5. Don’t Connect to Unsecured Wi-Fi Hotspots
- 6. Only Download Apps from Official App Stores
- 7. Factory Reset
- 8. Use Intruder Detection
- 9. Restart Your Phone Periodically
- 10. Check for apps using sensitive permissions
- Final Thoughts
- Frequently Asked Questions (FAQs)
1. Update Your Phone and Apps
Despite the multitude of new tricks that criminals are using to hack into your phone, there are some tried and tested methods that are fairly reliable, such as taking advantage of outdated or unpatched operating systems. Manufacturers and app developers regularly release new updates to help protect against new security threats and vulnerabilities.
By regularly updating your phone software and apps, you can protect your device against incoming attacks. In some cases an update may block a hacker that already has access to your device, if their malware relies on out-of-date software or a jailbreak.
2. Enable 2-Factor Authentication for All Your Online Accounts (Especially iCloud or Google)
A lot of people configure their phones to make things quicker and more convenient. For example, many people choose to back their files up on the cloud because it saves on physical storage.
While this might be a great feature to have in case your phone is broken or lost, it also means there is a duplicate copy of your device out there that could be hacked.
Using two-factor authentication, which is often built into cloud services, helps to protect your device from being hacked or data being stolen. As a rule, you should always use two-factor authentication to access your online accounts.
This means that even if a hacker manages to crack your password, your account will still be safe and your backed up data secure.
3. Download a Good Security App
A good security app can help you block hackers from your phone as well as detect any threats or vulnerabilities that may already be on there. Certo Mobile Security for iPhone and Android are trusted by millions worldwide to help protect their device’s from cyber attacks.

Award-winning mobile security
Block hackers for good with Certo's industry-leading security apps for iPhone and Android.
4. Use a Complex Passcode
This may seem obvious, but a strong passcode is the first line of defense against unauthorized access to your phone. Contrary to popular belief, most of the time a hacker will actually need physical access to your phone in order to install a malicious app.
By making sure that your passcode is at least 6 characters and you don’t use something that is easily identifiable for you, you can add an extra layer of protection to your device.
Once you have set your passcode, don’t share it with anyone else and where possible use biometrics such as fingerprint or face recognition.
5. Don’t Connect to Unsecured Wi-Fi Hotspots
Hacking doesn’t always mean that some malicious app or code has been loaded onto your phone. Sometimes a hacker may create a malicious WiFi hotspot designed to eavesdrop on your internet traffic.
That is why you should never connect your phone to an unsecured WiFi network, or one you do not trust. If you have no option other than to connect then make sure to use a good VPN like NordVPN so your traffic is encrypted.

6. Only Download Apps from Official App Stores
Third party app stores can be tempting as they often contain free versions of paid apps or tweaked versions of existing apps which offer more features than the original.
However, these apps are subjected to a much less rigorous approval process than any official app stores. Therefore, as a result, they are a common method used by hackers to distribute malware.
7. Factory Reset
As a last resort, performing a factory reset will stop or block any hackers who currently have access to your phone. Doing so will remove any spyware that has been installed on the phone but it also removes every trace of your account from the device. Make sure you create a secure backup of any important data before doing so.
To learn how to factory reset your Android device, click here.
To learn how to factory reset your Apple iOS device, click here.
8. Use Intruder Detection
Some apps for iPhone and Android offer an intruder detection feature to catch snoopers who have physical access to your phone in the act. For example, they can detect when an incorrect PIN is entered and either take a photo of the intruder or sound an alarm to alert you.
This feature is available in Certo Mobile Security for Android, and will be coming soon to Certo Mobile Security for iOS.
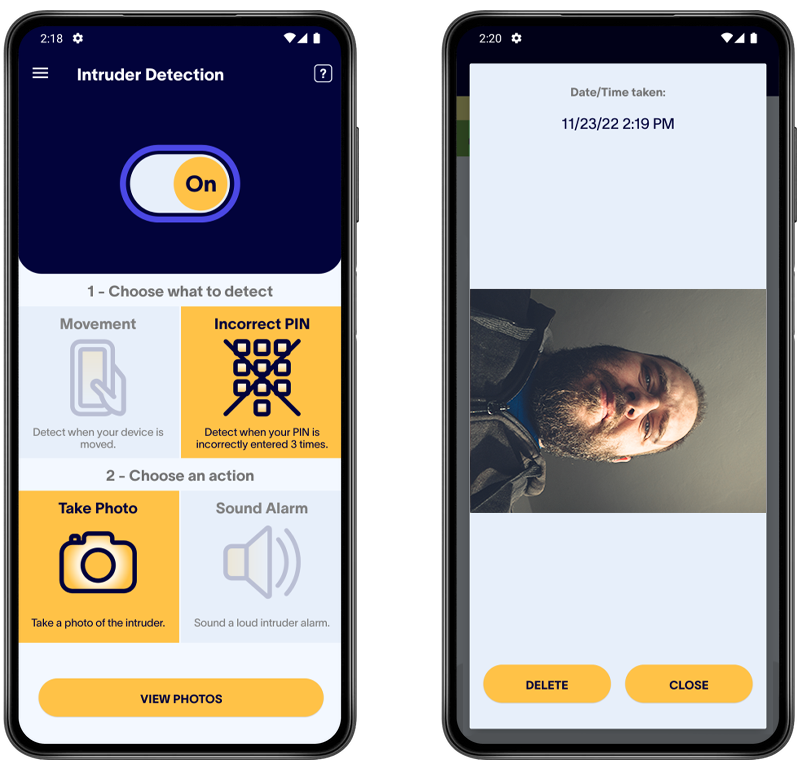
Fig 1: Catching an intruder with Certo Mobile Security for Android.
9. Restart Your Phone Periodically
Many hackers rely on your phone being left switched on for long periods of time, something which most of us do, in order to function. If you perform a restart, then it can stop a malicious app from working, which is especially true on iPhones. Therefore, restarting your phone periodically can be a good way to block any hackers that may be monitoring your movements.
10. Check Your Device for Apps That Are Using Your Location, Microphone or Camera
A lot of phone hacking takes the form of a hidden spy app. These spy apps will typically need access to things like your microphone, camera or location in order to perform their function.
Doing a quick review of the apps that have access to these features on your device can be an easy way to reveal a spy app.
Android users can use Certo Mobile Security to see exactly which apps are using these features and to quickly and easily make changes.
iPhone users can check their device by following these steps:
- Open the Settings app.
- Tap Privacy & Security.
- Tap either Location Services, Microphone or Camera.
- Review the list of apps that have access and make any changes if required.
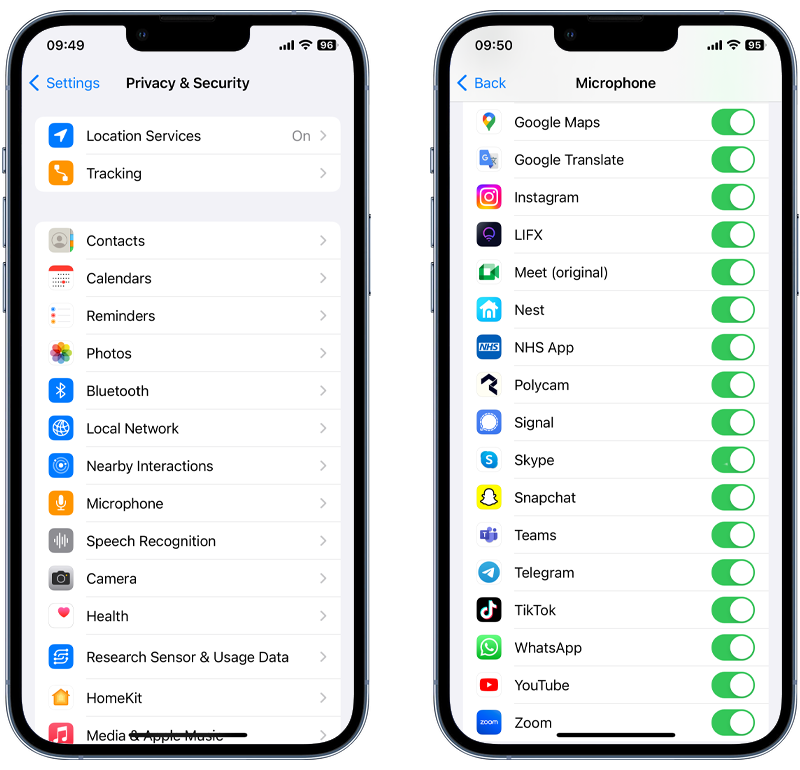
Fig 2: Reviewing apps with access to your Microphone on iOS.
Final Thoughts
All of these methods are good ways to mitigate the risks of hackers accessing your phone. However, if you want a more robust way to protect your devices, specialized security apps such as Certo AntiSpy (iOS) and Certo Mobile Security (Android) are a more secure way to spot and block hackers. In tandem with these methods, you are able to present a well-armored defense in the face of cybercriminals.
Frequently Asked Questions (FAQs)
What protects my phone from hackers?
Hackers will usually rely on out-of-date software with vulnerabilities or a phone that has poor access control. Therefore, the two best things you can do to protect your phone from hackers are
- Install any system or app updates as soon as they are available.
- Use a complex passcode to unlock your device, which is at least 6 characters in length.
Can you check to see if your phone is hacked?
With the right tools, it’s quite easy to tell if your phone is hacked. Certo’s free apps can help with this, download Certo Mobile Security for iPhone or Android now and run a scan for threats and vulnerabilities.
What should you do if your phone is hacked?
If you’re unfortunate enough to become a victim of phone hacking, there are a few things you should do as soon as possible:
- Run a scan with a security app and remove any identified threats.
- Change the unlock passcode on your device.
- Change the password for your Apple ID and/or Google account and ensure two-factor authentication is enabled for these accounts.
- Check for and install any updates for your operating system and apps.
- If your device is still compromised after the above steps then you may want to restore your phone to factory settings, which will remove any threats from your device. Ensure you have a full backup of your device and are familiar with the restore process before erasing any data.
Stop hackers for good
Quickly and easily run a spyware check on your cell phone today with one of our award-winning apps.
Cover Image by Freepik