How a Little-Known iPhone Feature Is Opening the Door for Cyberstalkers

Updated:

Most iPhone users cite Apple’s supposedly impenetrable security as one of the reasons for their loyalty to the brand. However, cyber stalkers and spyware providers alike pour their time and resources into getting around Apple’s defences.
While the tech giant has been fairly quick to crack down on actual holes and flaws in their security, when it comes to this technical loophole they have been dragging their feet.
At Certo we are constantly monitoring for new methods that spyware makers and cybercriminals develop to access data from mobile devices. Our researchers have recently discovered a new method that spyware developers are using to facilitate cyber stalking on iPhones.
This new method is particularly interesting because of just how easy it is to set up, and how difficult it is to detect. This means that the stalker can access most of the data on the phone without the need for much technical knowledge, and with little fear of being found out.
We have started to see this new method, known as WiFi Sync spyware, being adopted by leading spyware providers as the more traditional Jailbreak and iCloud methods are getting increasingly difficult to deploy. Solutions built using this new method are reliable and easy to use for cyberstalkers, meaning it is becoming the preferred way to illicitly access someone else’s iPhone and we predict that this will be the direction that iPhone spyware is going to take in the near future.
How does it work?
There is a little-known feature on all iOS devices called ‘WiFi Sync’, which essentially allows for a backup of the device to regularly be downloaded onto a nearby computer over a WiFi connection.
For most, this is a legitimately useful feature if you are worried about losing or damaging your device. Providing a solid external backup that isn’t just in the cloud without the need to physically plug your phone into the computer every day to create it. You just set it up once and it will continue to backup the entirety of your data every 24 hours until the feature is disabled.
Sounds great right? Unfortunately, this ease of set up and lack of maintenance makes it the perfect target for spyware providers and cyberstalkers. The solution offered by spyware providers requires the stalker to have access to their target device to set the connection up, but after that the target device will provide a full backup to a computer using the same WiFi network. An application on the computer then reads the backup and packages up all the information into a clear report for the stalker.
Nothing needs to be installed onto the phone itself, which makes it very difficult to detect. As far as the phone is concerned, it is just performing a routine backup.
‘There are so many other more innocent apps that we already have on our phones that can be manipulated to essentially be used to track someone or to spy on them’
Jenny Darmody, For Tech’s Sake Podcast
The main provider of this type of spyware advertises the application as a parental monitoring tool. The program promises an easy 5 minute installation, with no lockouts and no jailbreak required. They then promise a full view of a huge amount of activity on the phone, all parcelled up in a clear user interface. This includes:
- All SMS and text messages sent and received, including deleted messages.
- Photos
- Website history
- Call logs
- Messages and usage of apps including Tinder, WhatsApp, Viber and Kik
- GPS Location data
Data captured from the victim’s iPhone can be viewed via web portal, or as an app on the stalker’s phone. Here they will receive notifications of new messages and activity on the target device, alerting them at regular intervals to what their victim is doing.
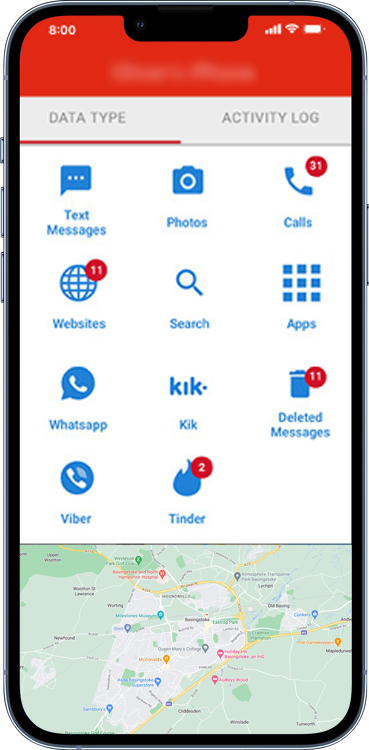
Fig 1. App on the stalker’s phone showing recorded activity from the victim’s device
The company offers tailored software for monitoring iPhones, iPads, Android phones, PC, Mac or Chromebook computers.
While the company markets its product as a parental monitoring tool, we have discussed previously how companies such as these brand themselves as parental monitoring tools, while marketing themselves on Google and elsewhere as tools to spy on the phones of a spouse or partner. You can read more about this here.
Why does this matter?
Spyware isn’t a new problem, we have written extensively in the past about different types of spyware and how to combat them. The significance of this particular discovery lies in the common misconception that spyware is not really a problem for iOS devices. It is true that newer iPhones cannot be jailbroken right now and iCloud hacking has largely been stamped out. But the WiFi Sync method can be used to spy on any iPhone with relative ease and can go undetected for months or even years.
How exactly would this sort of attack work and what are the signs to look out for?
Step 1 – The perpetrator installs an application on a computer that is joined to the same WiFi network as their target’s iPhone. Any computer can be used here, it does not have to be one that belongs to the target.
Step 2 – They get hold of the target’s phone for a few minutes, plug it into the computer and turn on WiFi Syncing. When enabled, the computer application can request a full backup from the iPhone over WiFi any time it wishes.
Step 3 – A backup of the iPhone is acquired over WiFi and saved to the computer. This backup includes all text messages, photos, call history, app data and much more.
Step 4 – The computer application waits for the backup to complete and then sends all of the information to the spyware provider’s server for processing.
Step 5 – The perpetrator logs into a web portal or app where they can browse all information from the iPhone backup in an easy-to-read report. This report will update with new information from the target’s iPhone each time a backup is run, which is typically every night.
Once the set-up has been completed there is little-to-no indication to the user of the device that this is happening. The only visible sign will be a small spinning icon at the top of their Control Center when the backup is in progress.
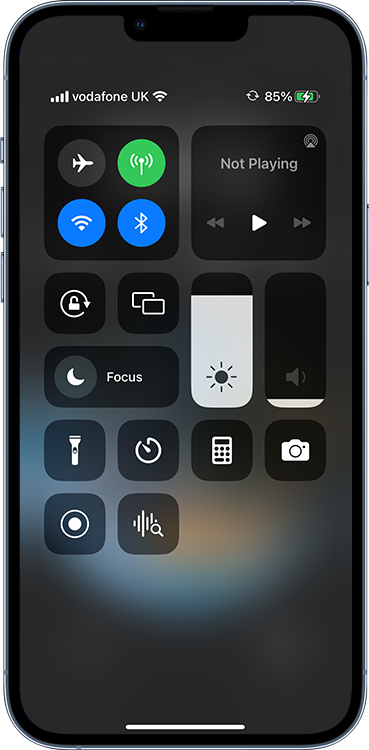
Fig 2. Control Center on the victim’s phone showing a backup in progress
When might this be used?
This is not the type of spyware that is typically used by faceless hackers to commit fraud. Instead, this is a really frightening example of how easily perpetrators of tech abuse and domestic violence can gain access and exert control over every aspect of their victim’s lives. This is not, however, the only form of tech abuse available that is difficult to detect.
As Louise O’Hagan, Co-Founder of Cyber Awareness Ireland said on the For Tech’s Sake podcast, tech facilitated abuse is the misuse of any device that can be connected to the internet to exert control over another person. This could include the use of IoT devices like Amazon Alexa, Google Maps apps, or even electric cars.
Apple has drawn negative attention for their attitude to security before, with AirTags, tiny coin sized devices used for keeping track of your belongings, being frequently misused for stalking. Previously, iPhone users were alerted to the presence of an AirTag with a cryptic message; “accessory detected” which leaves users unsure whether they needed to take the message seriously or not.
‘Airtags have been seen as the greatest gift to stalkers that there ever was’
Jenny Darmody, For Tech’s Sake Podcast
Following a reasonable response from users that this was unacceptable, and mounting evidence of AirTags being used in coercive, controlling or stalking situations, Apple have responded by refining this message to state ‘AirTag detected’ and have even updated the technology so that an Android device will also detect the AirTag and alert the potential victim.
However, when it comes to the WiFi Sync issue, they have been much less helpful, and have actually made changes to iOS that make it more difficult to tell if this feature is enabled.
Historically you could perform a simple check in the Settings app on the phone to see if WiFi Sync was enabled (and therefore if you may be a victim of this type of spyware). It would even display the name of the computer that your iOS device was set up to sync with. However, in iOS 13 and all subsequent updates, Apple has removed this information from the Settings app, making it extremely difficult to tell if it is enabled.
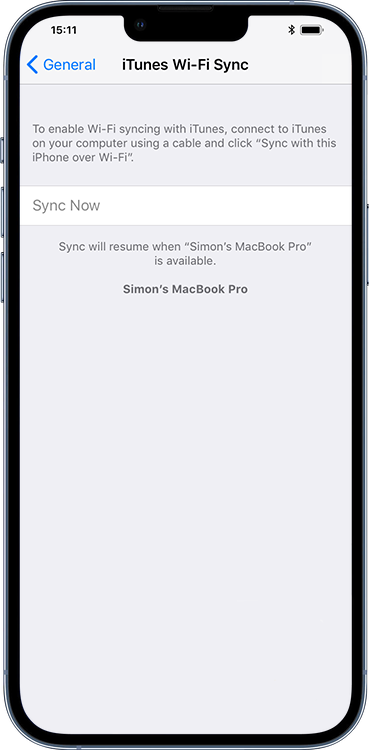
Fig 3. A pre iOS 13 device showing WiFi Sync status
What can you do if you are worried? What should Apple be doing now?
The first thing that Apple should do is to reinstate the section in the Settings app that shows whether WiFi Sync is enabled for the device. This would immediately allay the fears of potential victims as they can see if the feature is enabled. Even better, Apple could actually give iPhone users the option to disable WiFi Sync directly from their device.
Unfortunately, as long as Apple is excluding this information from the phone’s settings there isn’t an easy way to see if your iPhone is set to back up over WiFi or not. The only indicator would be the spinning icon at the top of the Control Center when the backup is happening. As these are often set up to happen overnight, this means you’ll need to be watching your phone screen 24 hours a day to try and catch it. Which obviously is not a practical solution.
While we are waiting for Apple to respond to this growing problem we know that people are being left at risk and in the dark about what is happening on their devices. For this reason we have developed the WiFi Sync Checker, a completely free tool that will quickly and easily check the WiFi sync status of your device and allow you to disable it if required. If you are concerned that you might be a victim of this type of spyware you can learn more about the tool and download it for free here.
Update June 2023
We’re pleased to report that in a recent iOS update, Apple has partially addressed this issue. There is still no option on the iPhone to see if WiFi Sync is enabled, however, the user does now receive a prompt on their iPhone to enter their passcode each time a wireless backup is about to begin.
This makes this attack much harder to hide and therefore much less likely to be used against someone without their knowledge.
If you’re concerned about this type of attack, be sure to update your device to the latest iOS version now.