Guides

How to Tell if a Motorola Phone Is Hacked and How to Fix
Smartphones have become central to our lives, storing everything from personal photos and conversations to sensitive financial data. This...
Guides

Smartphones have become central to our lives, storing everything from personal photos and conversations to sensitive financial data. This...
Guides

In today’s connected world, our smartphones are central to our daily lives, functioning not just as communication tools but also as...
Guides

If someone you know gains physical access to your phone, they can spy on your text messages, videos, photos, and other sensitive...
Guides

You may be under the impression that iPhones are the safest mobile devices on the market and with their tough stance on user privacy, Apple...
Guides

In this article, we’ll explain how you can find a keylogger on your iPhone and what you can do to prevent hackers from installing this...
Guides

Safeguarding data on your iPhone, including personal photos, videos, passwords, and banking information, is likely a top priority for you.
Guides

Learn to secure your iPhone and iPad from viruses with our guide. Find tips on virus removal, prevention, and iOS security features.
Guides

If you're an iPhone user, you might have encountered a frustrating problem recently: the iPhone calendar virus. So how do you get rid of it?
Guides
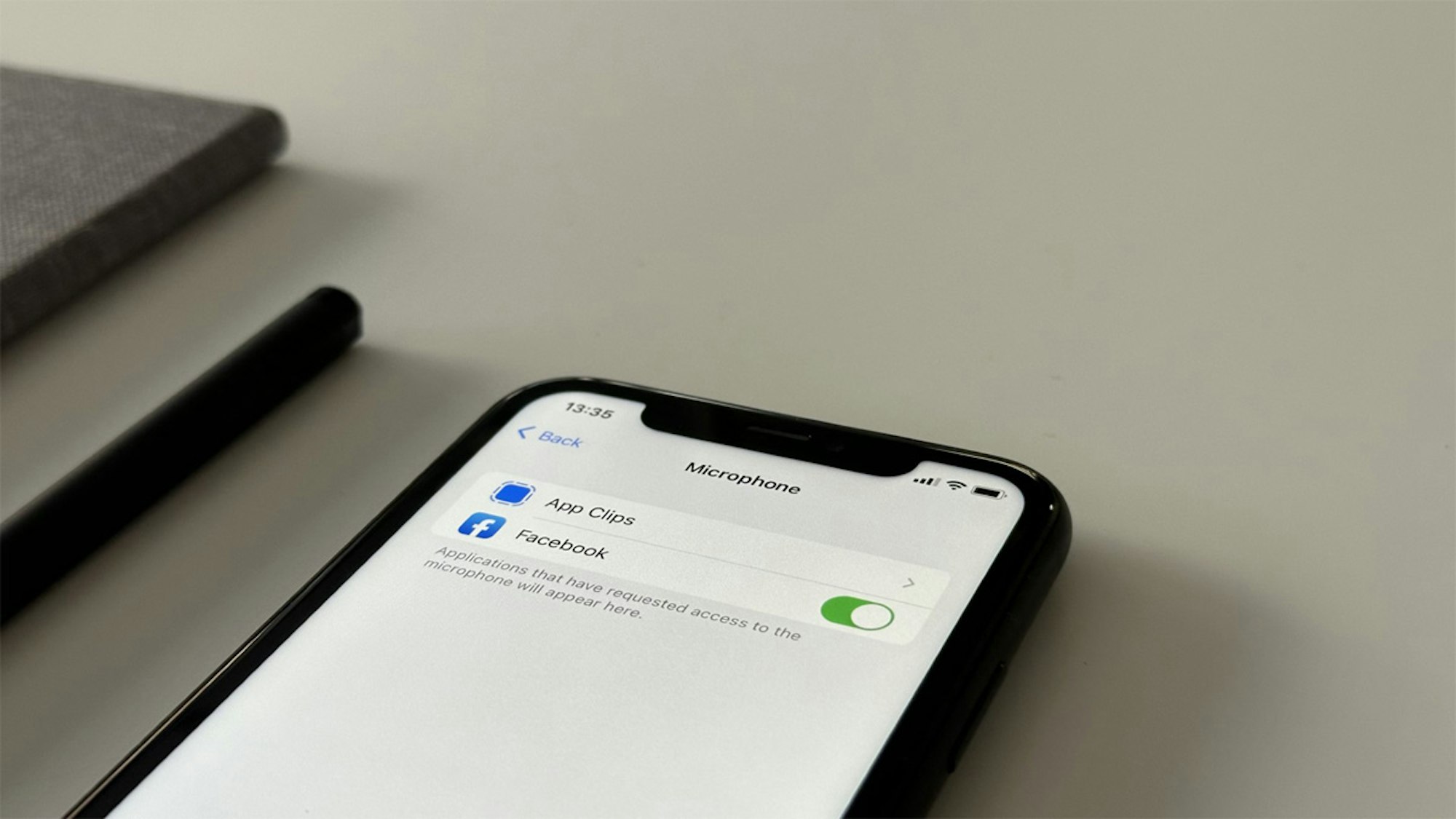
With the rise of virtual assistant apps like Siri and countless other applications requesting microphone access, protecting your privacy is...