Can You Get a Virus from Opening an Email?

Published:

We’ve all been there—the urgent-looking email messages from your bank, a notification about a package you didn’t order, or a friend asking for help strangely.
That sense of curiosity, concern, or urgency can make you click before you think. But hold on!
While you can’t get a virus simply by opening an email these days, cyber threats still lurk within your inbox.
In this article, we’ll explore how emails can be used for hacking, the telltale signs of a malicious email, and how to protect yourself from digital attacks.
💡 Can You Get a Virus from Opening an Email?
You cannot get a virus by simply opening an email. Modern email clients are designed to protect against this. However, the danger lies in:
⚠️ Clicking malicious links within a spam email.
⚠️ Downloading and opening infected email attachments.
⚠️ If you reply or provide personal information requested in the email.
⚠️ If you have outdated software or operating systems with security vulnerabilities.
Understanding Email Viruses
An email virus is malicious code that is distributed through email messages. It can take the form of an email attachment or a link embedded within the text of an email message.
Opening an email is generally safe; but clicking a link or opening the attachment in malicious emails may activate a virus, which can steal your data, damage your system, or let hackers into your network.
Important Note: We often hear “virus,” “malware,” and “phishing” used together, but they’re different:
➡️ Viruses are malware designed to replicate themselves and spread to other devices, and they usually require some form of user interaction (like clicking links) to be triggered.
➡️ Malware is a broader term encompassing various forms of malicious software, including viruses, Trojans, and spyware designed to damage or exploit systems.
➡️ Phishing is where hackers send fake emails that trick you into giving up information like your password or other sensitive data.
💡 Related: Top 5 Phone Phishing Scams to Look Out for in 2024
With this in mind, we’ll explore how you can get hacked via email below.
How Viruses Spread through Emails
A seemingly harmless email may have hidden dangers beneath the surface. Let’s uncover how hackers can use emails against you:
📎 Attachments
Cybercriminals are experts at disguising viruses.
They can embed malicious code in seemingly harmless documents, including spreadsheets, Word documents, images, and PDF files.
When you open an unfamiliar attachment, especially from a suspicious sender, you could unknowingly unleash the virus onto your device.
🔗 Embedded links
Emails can contain links, mimicking a bank or other trusted company. However, clicking these links might redirect you to malicious fake websites designed to look just like the real ones.
These sites can automatically download malware onto your device or exploit vulnerabilities in outdated software to infect your system.
☠️ Exploiting vulnerabilities
Although rare today, if you’re still running outdated software then certain advanced viruses can infect your device just by being viewed in your email client’s preview pane.
This highlights the importance of keeping your email software and operating system up-to-date with the latest security patches.
💡 Pro-tip: It's critical to remember that email attacks rely on making you act without thinking. Practicing vigilance and caution before clicking links or opening attachments is essential to staying protected.
Warning Signs of a Malicious Email
Not all dangerous emails are easy to spot. Simon Lewis, co-founder of Certo, advises keeping an eye out for these telltale signs:
🔎 Unknown senders: If you receive an email from an unfamiliar address, treat it cautiously. Always carefully examine the email address for any subtle misspellings or odd domains that try to mimic legitimate companies.
🔎 Spelling and grammar errors: Many phishing emails contain glaring typos, strange phrasing, or awkward grammar. While not foolproof, these errors can signal a hastily crafted scam message.
🔎 Urgent or threatening tone: Attackers love to create a sense of urgency, making you fear that something terrible will happen if you don’t click a link or download a file immediately. “Your account will be closed!” or “Urgent invoice payment required!” are common manipulative phrases.
🔎 Unexpected email attachments: If a stranger or even someone you know sends you a file out of the blue, verify its legitimacy before opening it. If they haven’t mentioned the attachment in the email’s text, take a moment to contact them through another channel (phone or text) and ask if they intended to send it.
🔎 Inconsistencies in email domain: Double-check the sender’s email address in the mail client and verify that the domain matches the organization they claim to represent.
Here’s an example of a malicious email, purporting to be from Microsoft:
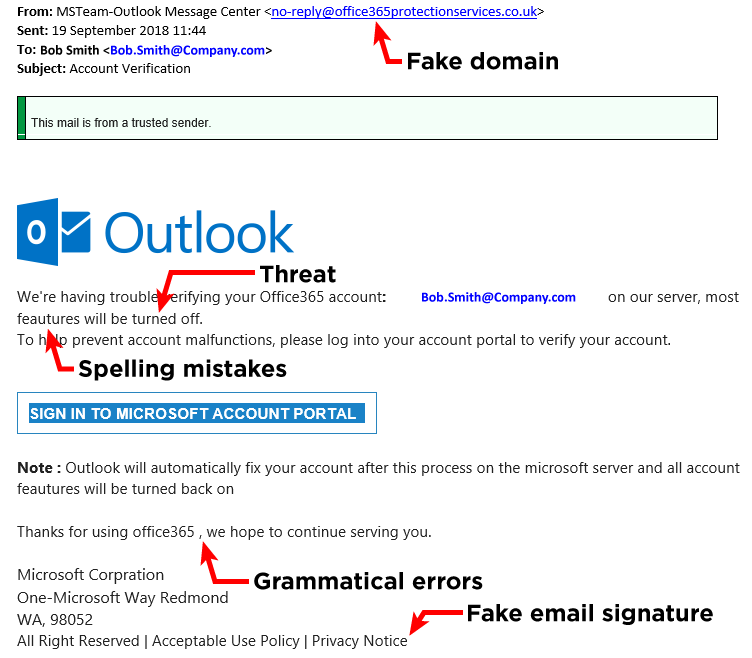
Image credit: QuoStar
Beware of emails that merely look official. Scammers often trick you with stolen logos or copy formats from legitimate companies.
Here are a few different types of email scams to watch out for:
| Scam Type | Description | |
|---|---|---|
| 1 | Emails claiming to be from reputable companies (tech support, banks, retailers, etc.). | Impersonate known companies to trick you into giving up your login details, personal information, or financial data. |
| 2 | Emails about account issues (suspicious activity, billing problems, etc.). | Claim problems with your accounts to scare you into clicking links or providing sensitive details. |
| 3 | Emails offering something too good to be true (refunds, prizes, etc.). | Lure you in with promises of unexpected rewards to get you to click links or provide information. |
| 4 | Emails with urgent or threatening language. | Create a sense of urgency to pressure you into acting without thinking, often claiming account closure, incorrect billing, or legal consequences. |
| 5 | Emails from unknown senders with attachments. | Use unfamiliar senders and attachments you weren't expecting to make you curious enough to open them. Attachments might contain malware or lead to phishing sites. |
| 6 | Emails mimicking shared files or collaboration requests (Google Drive, Dropbox). | Appear as legitimate file-sharing notifications but contain links that download malware or lead to fake login pages. |
| 7 | Emails impersonating executives within your company. | Target employees with emails pretending to be from high-level executives or HR personnel to request sensitive data or authorize fraudulent transactions. |
How to Protect Yourself from a Virus Infection
The best way to avoid email-based viruses is to be proactive with your digital safety. Here are a few critical practices:
✅ Healthy skepticism
Even emails from people you know may be compromised. Cultivate a healthy skepticism when it comes to opening emails.
Always first assess the legitimacy of a request before opening attachments or clicking on links. If something seems off, contact the sender through another channel to confirm.
✅ Email client settings
Email clients like Apple Mail, Yahoo Mail, and Gmail offer a “plain text” view option. This feature turns off images, fancy formatting, and potential hidden code, which can be helpful for extra security.
Additionally, most email clients allow you to set up spam filters. These filters can help automatically identify and sort potential scam emails into your junk/spam folders.
✅ Keep software updated
Software updates often contain critical security patches that fix vulnerabilities that cybercriminals exploit. Ensure that your mobile and computer operating system, web browsers, and email apps are always up to date.
✅ Download a reliable antivirus software
Invest in reputable and regularly updated antivirus software. Schedule regular scans to detect potential threats early. Your antivirus is like a digital immune system, constantly working to protect your devices.
Need Reliable Mobile Protection?
Certo Mobile Security has your back. Get advanced antivirus for your iPhone or Android smartphone.
What to Do If You Think Your Device Has Been Infected
If you suspect you’ve clicked on a malicious link or opened an infected attachment, act quickly to avoid viruses:
➡️ Disconnect: Immediately disconnect your device from the internet. This helps prevent the malware from spreading or communicating with external servers controlled by attackers.
➡️ Complete a malware/virus scan: Run a thorough scan with your antivirus software. This software will try to identify and quarantine malicious files.
➡️ Change passwords: Change your email password immediately. If you reuse the same password across different accounts (which you should avoid!), change the passwords for those services, especially those linked to finances or sensitive data.
➡️ Report: If possible, report the malicious email to your provider. They can take action to block the sender or warn other users.
Final Thoughts
Email remains a powerful tool and a potential entry point for cyber threats. Always remember the dangers of opening attachments or clicking links from unknown senders.
Such actions often allow viruses and other malware to infiltrate your system.
The best defense against email-based attacks combines constant vigilance and reliable security software. Train yourself to scrutinize emails critically, always questioning the legitimacy of a message before interacting with it.
By pairing awareness with a robust mobile antivirus solution like Certo, you’ll significantly reduce your risk of falling victim to these attacks.