Can iPhones Get Viruses?

Updated:

In today’s world where so much private information is kept on our phones, they are increasingly becoming more valuable targets for hackers. iPhone users often believe that iOS devices are “unhackable,” but is this actually true?
Apple is keen to maintain this image, and the company regularly talks about how secure its devices are. But while it’s true that iPhones are one of the more secure phone brands on the market, are they really immune to hacking and viruses? In this article, we examine the facts
Think your iPhone has a virus?
Quickly and easily check your iPhone for threats today with the award-winning Certo AntiSpy.
Can My iPhone Get a Virus?
We all have an idea in our minds of what a so-called ‘computer virus’ is. This term mostly comes from the earlier days of computing, when computers could easily become infected with a virus.
Hackers used malicious websites or fake emails to trick people into opening them and allowing the virus access to their computers. The virus would then take control of the computer and generally cause havoc.
Viruses were often costly to rectify and could result in the loss of important data. Not to mention the risk of passing the virus onto another person’s computer if you weren’t careful.
If this is the type of virus you are worried could infect your iPhone, then the simple answer is no, your iPhone cannot be infected in the same way as a computer.
However, this does not mean that your phone is automatically protected against other cyber threats. In this article, we’re going to explore the most common threat for iPhones, spyware, and explain how you can protect your device from it.
What Is Spyware?
As its name suggests, spyware is usually created with the purpose of spying on a user, collecting passwords, account usernames, and a whole host of other sensitive data that should remain private.
Spyware can be installed in a number of ways, but the most common one involves a third party getting physical access to your device and installing software (often in the form of malicious apps) that allows hackers to monitor and collect all device activity.
This installation process can be done in mere minutes and can remain completely undetectable to the user–who might never realize that they’ve been hacked. This is especially true for users who are less tech-savvy, and therefore less likely to keep their phone up to date with the latest security patches.
In some cases, more advanced spyware can even be installed without having physical access to the device. For example, the victim might get hacked by clicking on a malicious link or email attachment, or by unwittingly downloading a rogue app.
How Common Is Spyware on iPhones?
Compared to the Android operating system, iOS (the operating system used for iPhones and iPads) is generally more difficult to hack. However, this doesn’t mean that it doesn’t occur, and it certainly doesn’t mean it can’t happen to you.
This is especially true when you consider the fact that some spyware is extremely cheap to purchase. Commercially available spyware can be purchased for as little as $30, and it does not require the person using it to be a computer genius.

Are There Other Threats iPhone Users Should Know About?
Another common method of hacking iPhones is by gaining access to a user’s iCloud account. Certain tools allow a hacker to regularly and automatically download data from iCloud that has been synced from your phone. This gives them access to your text messages, photos, private notes, and GPS location history.
The solution is to activate two-factor authentication on your device, as this will add an extra layer of security to your iCloud account and will prevent most cases of this type of hack from happening, even if the attacker knows your password. Click here to read more about iCloud hacking, as well as how to protect your device from this type of hack.
Signs That Your iPhone Might Be Hacked
Although it can be difficult to detect iPhone viruses and spyware on your own, there are a few warning signs to look out for.
Unexplained high data usage
Spyware typically uses lots of data to send information about your phone activity to the hacker. If your data usage has increased dramatically and you’re not sure why, it could be a sign of a malware infection.
Unfamiliar apps
If you think someone might be spying on your phone, look out for any apps that you don’t remember downloading. Delete any apps that you don’t recognize and that look suspicious, since they could be spyware apps.
Phone overheating
If you notice your phone getting unusually hot, this could be a sign of malware. Since the phone has to work harder to send your private data to the hacker, the extra processing can make it hotter than usual.
What to Do If Your iPhone Has Been Hacked
If your iPhone has been hacked, there are a few things you can do to regain control.
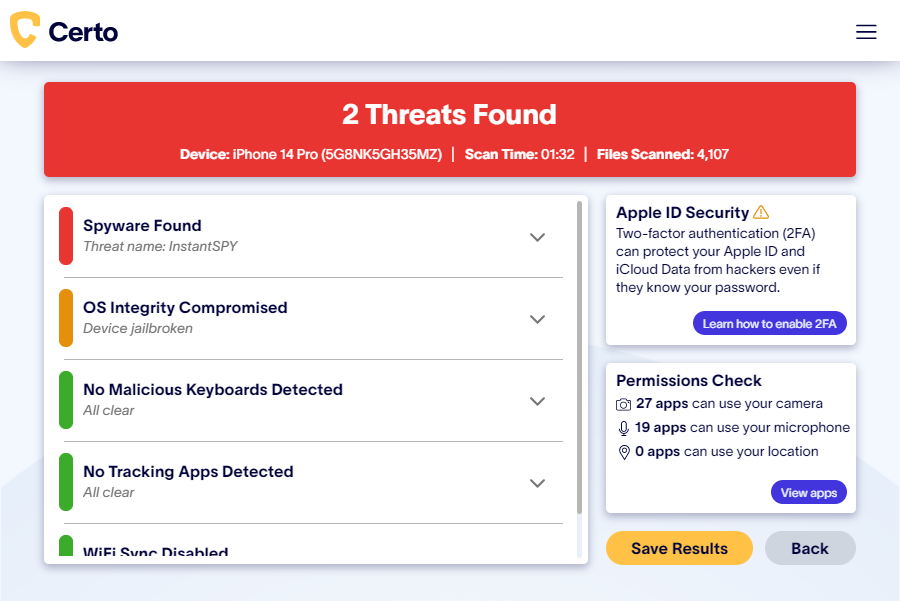
Use Certo AntiSpy
Certo AntiSpy is the award-winning tool designed to detect spyware on iPhones and iPads, and guide you through removing it for good. If you think your phone is hacked, it should be your first port of call for a simple and effective solution.
Restore to factory settings
Some people choose to do a factory reset to try to remove viruses from their iPhone. Although this method often works, it should be seen as a last resort because it wipes all the data from your phone.
If you do choose this option, make sure you backup all of your important data on an external device, or on your iCloud account.
To reset, go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings.
Restart your phone
In some cases, simply restarting your phone can remove the spyware. However, the effectiveness of this method will depend on what type of spyware your phone is infected with.
How Can iPhone Users Protect Their Device from Spyware?
This can be more difficult on iPhones than with other manufacturers. This is because Apple imposes restrictions on what apps are allowed to do on its devices. One of these restrictions is that security apps cannot access areas of the file system where spyware usually hides. This means that antivirus apps do not exist on the App Store.
However, there are still several ways iPhone users can protect themselves against spyware:
Keep your iOS updated
It’s important to update your phone as regularly as possible. Apple is constantly working on bug fixes and ironing out weaknesses in their system that hackers might try to exploit.
Every new update leaves your phone better protected. To enable automatic updates, open the Settings app, tap General > Software Update > Automatic Updates, then turn on Install Automatic Updates.
Never jailbreak your iOS device
It may be tempting to jailbreak your phone in order to bypass some of Apple’s software restrictions. However, jailbroken devices are easier for hackers to gain access to and you could be putting yourself at risk.
Never download third-party apps from outside the official App Store
Apps that are not downloaded from the App Store are more likely to be fraudulent. Never download suspicious apps from other sources, since doing so only puts your device’s security at risk of infection from iPhone viruses.
Use a strong passcode to unlock your device
Ensure your passcode is at least 6 characters and do not share it with anyone. For added security, activate biometrics such as fingerprint or face unlock.
Keep your apps updated
Just like Apple, app developers are constantly improving the security of their apps. By running the latest version of all your apps, you make it harder for hackers to exploit security weaknesses.
Be vigilant online
Fake emails and malicious websites can trap you into entering personal information on what is essentially a hacker’s database. Be vigilant and only trust websites you know are reputable.
Regularly scan your iPhone for security threats
Although Apple doesn’t allow antivirus apps in their App Store, you can use software such as Certo AntiSpy to perform a full scan of your device by connecting it to a computer via USB.
Award-winning spyware detection
Combat spyware and other cyber threats with Certo AntiSpy, the world's leading anti-spyware tool for iPhones.
Cover Image by stockking on Freepik