Beware of What You Type: The Rise of Keyboard-Based iPhone Hacking

Published:

A troubling new hacking method has emerged—cybercriminals have found a way to bypass Apple’s normal security checks and use third-party custom keyboards to spy on people’s iPhone activity.
Once one of these malicious keyboards has been installed on an iPhone, hackers can use it to gain unauthorized access to every keystroke on a victim’s device. This allows them to record private messages, browsing history, and even passwords.
iPhones are usually considered one of the most secure devices. This is thanks to their closed operating system and regular security updates. However, security patches alone may not be enough to combat this new threat.
These keyboards pose a significant threat, especially in domestic tech abuse situations where an abuser uses technology to harass, stalk, or intimidate a partner.
After receiving multiple reports of cyberstalking incidents, where stalkers appeared to know everything that their target had typed into their iPhone, Certo’s threat lab launched an investigation. This revealed the presence of these nefarious custom keyboards on the affected devices.
We’ve created guidance explaining how this exploitation works, how iPhone users can shield themselves, and what steps Apple should take to address this issue.
What Is This New Threat?
Surveillance on an iPhone presents notable challenges. Typically, a hacker would need to either jailbreak a target’s iPhone or gain access to their iCloud account.
However, this new technique is significant as it does not rely on any of these usual prerequisites. It is compatible with all iPhone models, leverages an existing feature within the iOS system, and doesn’t require any specialized technical skills.
It takes the form of a custom keyboard, which are commonly used on iOS to improve grammar, perform translations or add new emojis. However, when set up in a specific manner, these custom keyboards can function covertly as keyloggers. This allows them to discreetly capture and transmit all keystrokes made by the user, providing hackers or snoopers with detailed access to the typed information.
Some off-the-shelf spyware developers have exploited this, offering keylogger services through these keyboards for as low as $30.
This is particularly concerning for those at risk of domestic tech abuse, as it only requires a few unsupervised minutes with the device to set up and it’s difficult to spot unless you know what to look for. We’re starting to see reports from our users in these situations, highlighting the need for awareness and vigilance.
How Does It Work?
We don’t want to provide a how-to guide for stalkers, so we won’t go into the exact setup steps or name any spyware products. But it’s important to note that the process is worryingly straightforward, here’s how it works…
The process begins with installing a small app containing an embedded custom keyboard on the target’s device. The spyware developers we investigated often distribute these apps through TestFlight—a platform for testing new iOS apps before they are released on the App Store.
By deploying via TestFlight, spyware developers are likely attempting to avoid detection by Apple. This is because TestFlight apps are not subjected to the same strict review process as apps from the main App Store.
However, in theory, a malicious custom keyboard could be distributed via any app. This means a seemingly harmless app may serve as a carrier to introduce a keylogger.
Once the app is on the iPhone, the stalker then installs the custom keyboard via the Settings app and configures it to have ‘Full Access’ to the device. Next, the perpetrator switches the iPhone’s default keyboard with this custom version. Visually, these keyboards are almost identical.
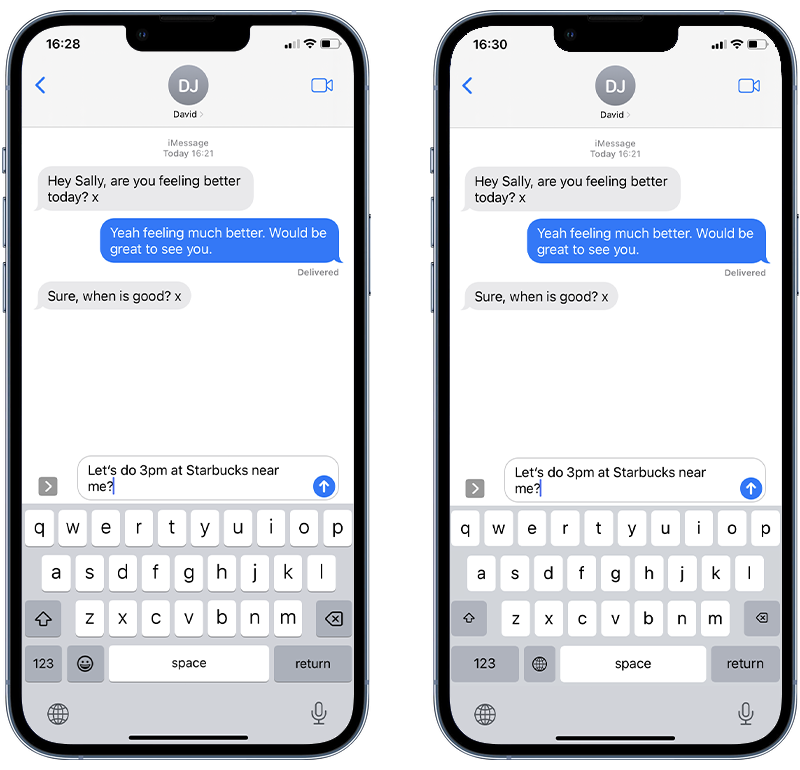
Fig 1. Default iOS keyboard (left) vs. custom keyboard with keylogging capability (right).
The malicious keyboard then records everything that the victim types on their iPhone and sends it to an online portal which can be accessed by the stalker from anywhere in the world.
Captured information can include things like: private messages, passwords, two-factor authentication codes, notes and essentially anything typed into any app on an iPhone.
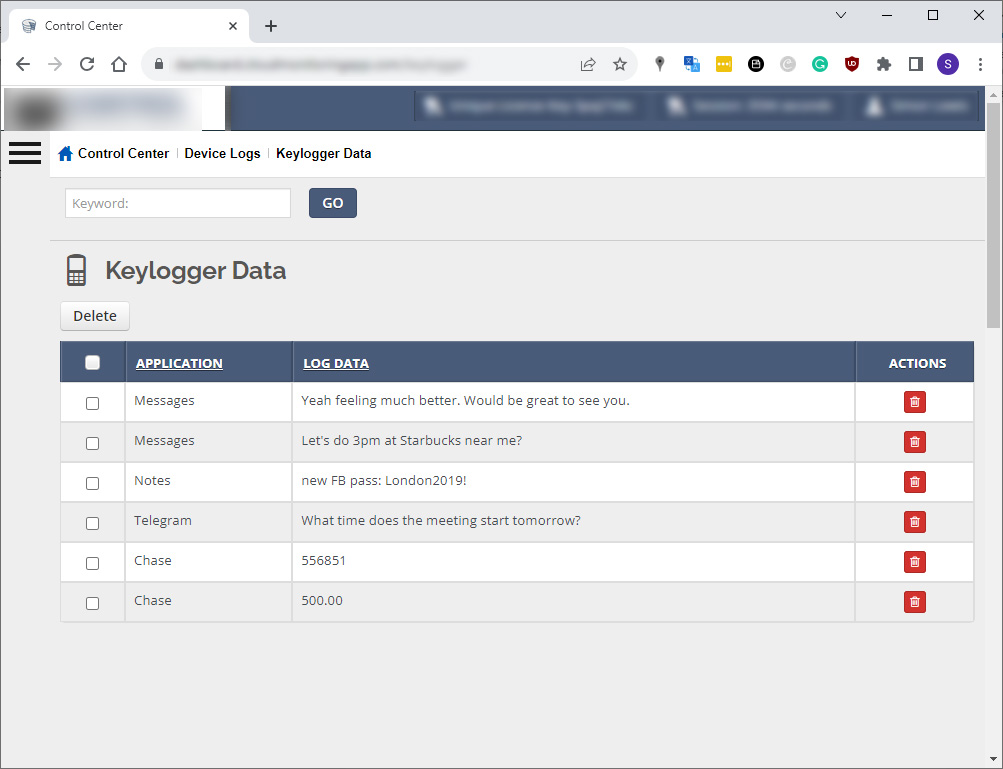
Fig 2. Web portal for viewing captured keystrokes.
How to Tell if You’re Affected
Spotting a covert keylogger on your iPhone isn’t straightforward, as these custom keyboards often mimic the appearance of standard ones. You can see this in the screenshots above.
The best way to check if you’re affected is to review your installed keyboards in your device’s Settings app. To do this, go to Settings > General > Keyboard > Keyboards.
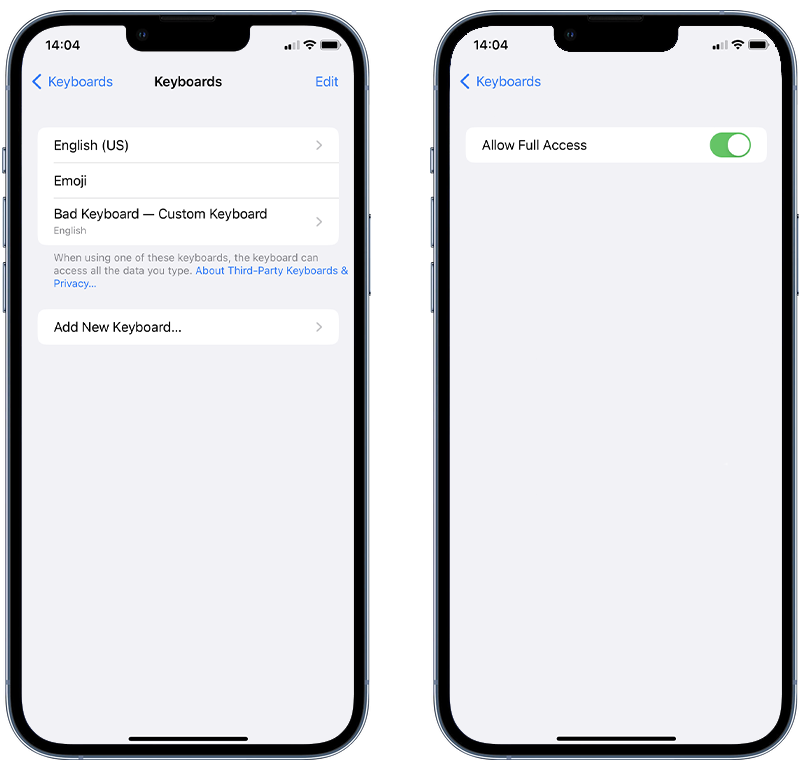
Fig 3. Checking for custom keyboards on iOS.
You’ll usually see two standard keyboards: one in your language—for example, ‘English (US)’—and another, named ‘Emoji’. Any other keyboard could be suspicious, especially if it has ‘Allow Full Access’ turned on.
If you find a keyboard you don’t recognize, remove it immediately.
To delete unrecognized custom keyboards on your iPhone, follow these steps:
- Tap Edit
- Tap the red minus button next to any keyboard you don’t recognize
- Tap Delete
In response to this prevailing threat, we have also added keylogger detection to our free iPhone app, Certo Mobile Security.
What Should Apple Be Doing?
We think that Apple could enhance its security measures to handle these keyboard threats better.
A simple but effective change could be to notify users when a new keyboard with ‘Allow Full Access’ is installed. Obviously, the notification should not appear immediately as the stalker would likely just clear it, but it could appear randomly within 24 hours of installation. This would be similar to WhatsApp’s method of alerting users about new device connections using the Linked Devices feature.
Additionally, the review process for TestFlight apps is not as strict as the main App Store. Apple therefore might consider introducing more stringent checks for these apps, especially those that have an embedded custom keyboard. This would make it significantly harder for TestFlight apps to be misused by hackers and spyware makers.
Wrapping up
This new method of using malicious custom keyboards to compromise iPhone security is a concern, especially for those vulnerable to domestic or tech abuse, where obtaining physical device access to set up the keyboard is much easier.
Our findings highlight the importance of being cautious and regularly checking your iPhone’s keyboard settings for anything unusual.
Apple also has a role to play in enhancing device security. Simple steps, like alerting users to keyboards with full access and scrutinizing TestFlight app submissions more closely, could make a significant difference. Staying informed and aware is key in this ever-evolving digital landscape.