Anti-Spyware for iPhone: A Complete Guide

Updated:

Although you may think of phone hacking as something that is unlikely to happen to you, the truth is that it is becoming increasingly common.
All a hacker needs is access to your phone for just a few minutes to install malicious software onto your device, giving them access to your emails, text messages, personal photos, phone calls, GPS location, and more.
Hackers can use this information to monitor your activity, blackmail you, and even commit identity theft.
Award winning anti-spyware
Detect and remove iPhone spyware now. Certo’s apps are trusted by millions worldwide.
But it’s not just criminals or cyber experts who might be hacking your phone. Most spyware apps for iPhones are low-cost, easy-to-install, and commercially available—such as FlexiSpy and mSpy—which anyone with access to your phone could install in just a couple of minutes.
Whether it’s a jealous partner or an ex, an interfering boss, or someone else, it’s possible that someone could be snooping around on your phone.
If you’re an iPhone or iPad user you’ll want to protect your phone from spyware, but it can be difficult to find an effective antivirus or anti-spyware app on the App Store due to Apple’s strict security features and privacy policies.
However, there is a solution. In this article, we explain how Apple users can protect their mobile devices from hackers by using an anti-spyware app like Certo AntiSpy, which is designed to be compatible with Apple devices.
Apple’s Approach to Antivirus Software
Before we go any further, it’s important to understand why Apple does not allow antivirus apps to be installed on iPhones or iPads. The reason is that Apple’s operating system simply does not allow apps to access any other apps or files on the device.
The company’s developer guidelines state that apps “may not read or write data outside their designated container area” and that any app found to be in violation will be removed from the App Store.
In some ways this is great for privacy and security; it means that an app like Instagram couldn’t gain access to financial information stored in your banking app, for example.
However, it also means that any antivirus apps downloaded onto your device wouldn’t be able to detect the presence of spyware apps or files.
It’s worth noting that there are still some great apps available on the App Store that can help with your device security by incorporating a VPN (Virtual Private Network) or giving you extra ways to backup your data. They just can’t do a full scan for spyware or other advanced threats.
The Solution: Secure Your iPhone with Certo AntiSpy
Luckily, there is a way to detect spyware on an iPhone or iPad that does comply with Apple’s guidelines.
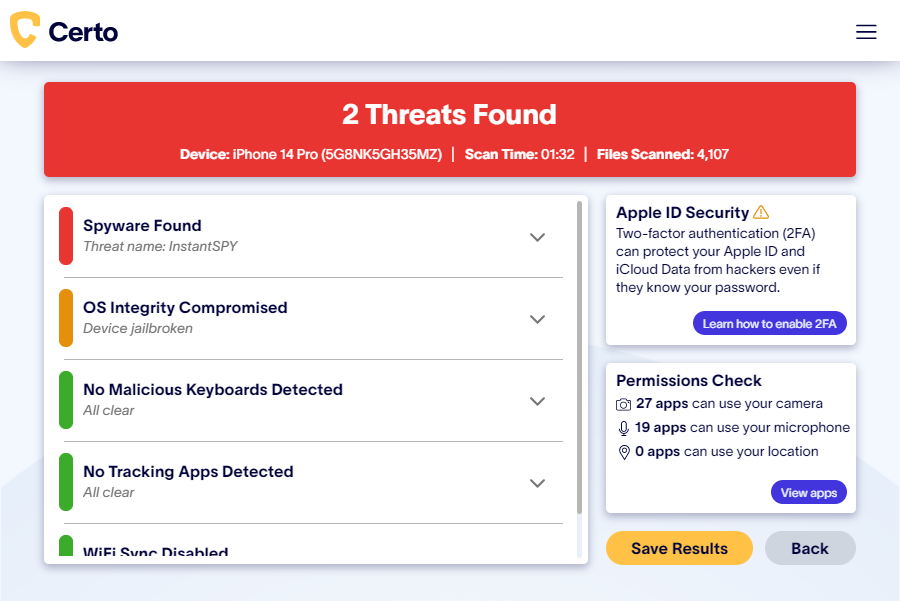
Certo AntiSpy is one of the best iPhone antivirus apps on the market, and it offers advanced protection for your iOS devices. Scan your iPhone or iPad for viruses and spy apps by connecting it to your computer via USB. Certo will complete a full scan of your mobile device and quickly detect any spyware or malicious apps.
You’ll then be provided with simple steps to remove the spyware, helping you regain control of your device and your privacy.
Since the anti-spyware software is installed on your computer rather than your iPhone, it is able to detect spyware without the need to install an antivirus app onto the iPhone itself.
Types of Spyware on iOS Devices

Image by Freepik
Now that you know how to remove viruses and spyware from your iPhone, it’s time to learn a little more about the different ways that it may have gotten onto your phone in the first place. With this knowledge, you’ll be able to better protect yourself against attacks.
1. Malicious apps
Spyware apps are the most common way for a hacker to monitor your activity. They can be purchased for as little as $30 and installed on your phone by anyone who has physical access to it for just a couple of minutes.
Once the software is installed, the hacker can remotely monitor all kinds of activity from your phone, including text messages, photos, GPS location, and more.
2. iCloud attack
Some hackers might try to access your information via your iCloud account. They target the data synced from your phone and held in your iCloud account, rather than targeting your physical device.
This type of attack doesn’t require access to the device itself, but does require the hacker to have the victim’s Apple ID login details. And because it is carried out via the Internet, it is harder to detect than spyware that is installed on a device.
To protect yourself against this kind of attack, enable two-factor authentication with your Apple ID. This type of authentication requires two pieces of information to access your account—for example, your Apple password and a six-digit code sent to one of your trusted devices—making it much harder for hackers to gain access.
3. Misusing legitimate apps
Apps that have access to your location, such as Find My and Apple Maps, can be misused to share the victim’s device locator with a hacker. For this to be possible, the hacker would need to have had physical access to the device at some point to set it up.
Hackers can also change the logged-in account for the device’s web browser to collect browsing data history and account login details.
As no malicious apps are installed, it’s possible for this type of attack to go unnoticed for months or even years.
4. Zero-day exploits
Zero-day exploits are quite uncommon, but can be devastating for victims.
They’re called zero-day exploits because the way they work is yet to be discovered by security researchers and as such, no fix has yet been released for the apps or devices that are affected.
Zero-day attacks are usually created by hackers when they discover a weakness in operating systems or apps.
Once this weakness has been exposed it’s immediately exploited, leaving developers trying to fix the problem as quickly as they can to minimize the risk to their users’ data.
Zero-day attacks can affect millions of users. In some cases, more advanced exploits can even infect a device with malicious software remotely, without the hacker needing to access the victim’s device.
Run a spyware scan
Get your privacy back. Detect and remove iPhone spyware with the award-winning Certo AntiSpy.
How to Detect and Remove iPhone Spy Software
If you’re suspicious that someone is monitoring your phone activity, there are a few things you can do.
Install Certo AntiSpy
Certo AntiSpy is the best way to keep your Apple devices safe. It’s simple to use and can help you find out once and for all whether you’re being spied on. If spyware is detected, you’ll be provided with clear steps on how to remove it and get your privacy back.
Here’s how:
- Download Certo AntiSpy to your computer.
- Connect your iPhone via USB.
- Click Scan.
- Once complete, click Remove next to any threats detected.
Manually identify malicious apps
Another way to find spyware on your device is to manually search through all the apps on your phone. To do this go to Settings > General > iPhone Storage and scroll through all installed apps. Even though this method can be successful in some cases, malicious software is often disguised or hidden in folders on your phone to make detection more difficult.

Update your operating system
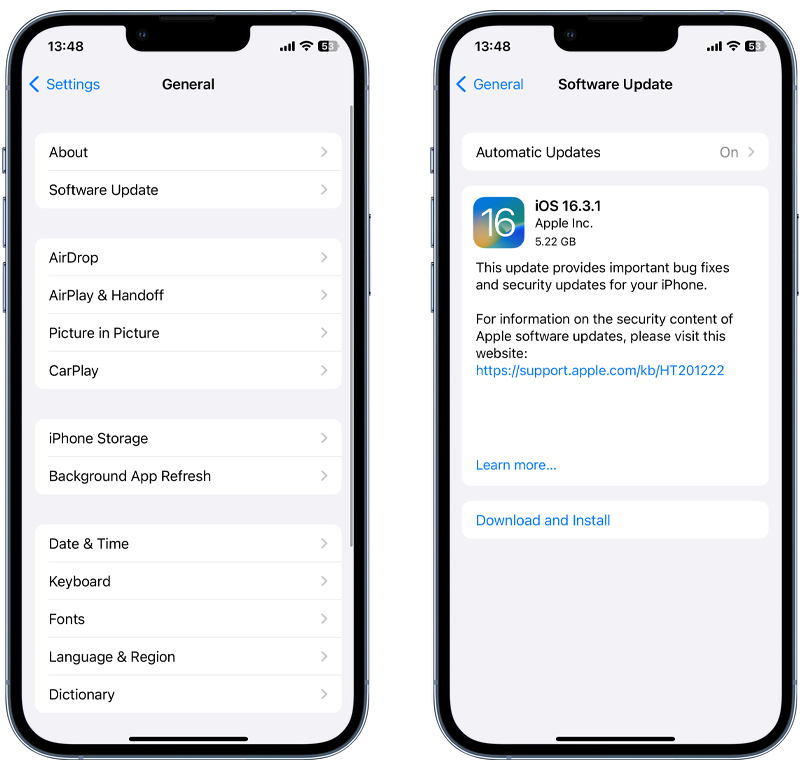
In some cases, spyware can be removed by simply updating your phone to the latest version of iOS. Hackers often try to take advantage of security vulnerabilities in older versions of operating systems, so by keeping your phone up to date you can improve your phone security.
You can check for and install any available iOS updates by going to Settings > General > Software Update.
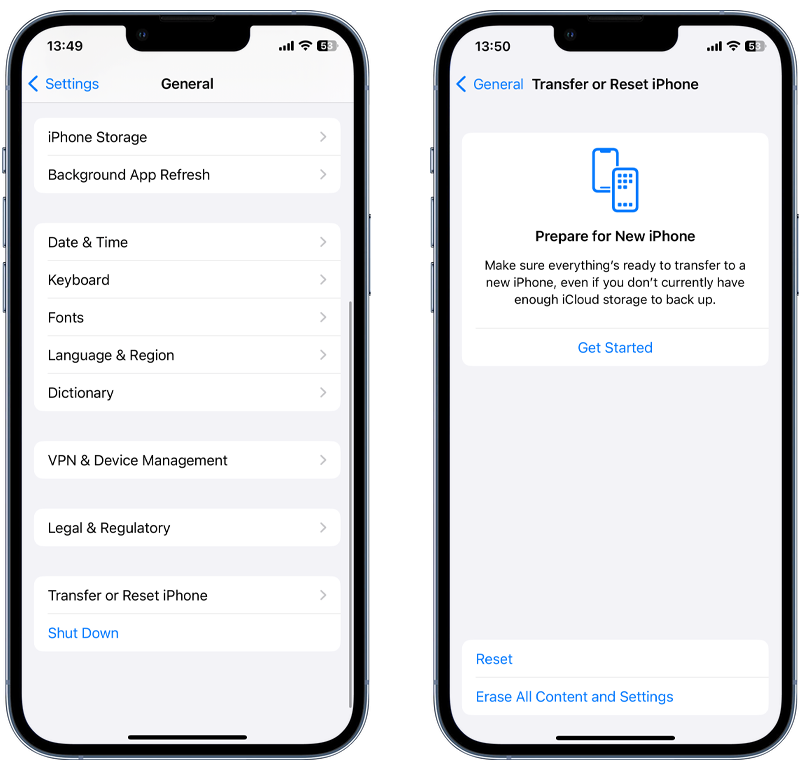
Perform a factory reset
A factory reset is a last resort that wipes all of the data on your phone and restores it to the factory settings when you bought it. Since it removes everything from your phone, the idea is that it will remove any spyware in the process, too.
However, it will also delete everything you have stored on your phone. It should only be carried out after you have done a contacts backup, as well as externally saving all your photos, messages, and anything else you don’t want to lose.
To reset, go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings.
Wrapping Up
Although Apple’s security and privacy policies restrict the types of antivirus or anti-spyware software that can be used on iPhone and iPads, there is a solution. Certo AntiSpy allows you to easily scan your phone for signs of monitoring via a USB connection to your computer.
Install the award-winning Certo AntiSpy today and get peace of mind that your private data is protected.