How to Tell if Your Android Phone Is Hacked

Updated:

One of the biggest reasons people hesitate when it comes to buying an Android phone is because they are concerned that Android devices are easier to hack than iPhones. And for the most part, this is true. While that doesn’t mean Android devices can’t be secured, it does mean that there are a few risks Android users need to keep an eye out for.
In this article, we’ll help you to find out whether or not your Android phone has been hacked by looking at nine different problems that you might be experiencing. We’ll also give you some advice on how to solve them.
Find out if your phone is hacked the easy way
Install Certo Mobile Security for free to identify and remove threats from your Android phone in minutes.
How to Tell If Your Android Phone Is Hacked
1. Battery draining too quickly or getting hot
Noticed that your battery is not lasting as long as it should? Has your battery life become significantly worse over the last few weeks or months? High battery usage might be a sign of phone hacking on your Android device.
Malicious software or spyware that may be installed on your device requires more processing power to run. This is because it is always working in the background, sending information from your phone to the hacker.
If your phone is hot to the touch this could also be a sign of phone hacking, as the phone heats up due to the spyware making it work harder.
It’s important to remember that there may be other reasons for fast battery drain or your phone heating up. For example, phone batteries inevitably deteriorate over time, so if your phone is a couple of years old this could be the reason.
2. Unexpected Ads or Pop-Ups
If you’re encountering unexpected ads or pop-ups on your Android device, it could be a sign of adware or malware. These ads may appear as notifications, on your home screen, or within apps, often claiming that your device is infected and urging you to download a security tool.
To check for this, observe if the ads appear while using specific apps or across various applications. If you’re unsure of the source, try restarting your device in Safe Mode. This mode will temporarily disable all third-party apps. If the popups stop appearing then you know that an app is the cause.
Here is how to activate safe mode:
- Press and hold the power button.
- Long-press the Power Off option until the Safe Mode prompt appears.
- On the following warning screen, tap the icon once more to proceed. Your phone will then reboot into Safe Mode.
How to exit safe mode:
- Simply restart your device.
- Alternatively, use the notification panel: select Safe Mode is on and then tap Turn off.
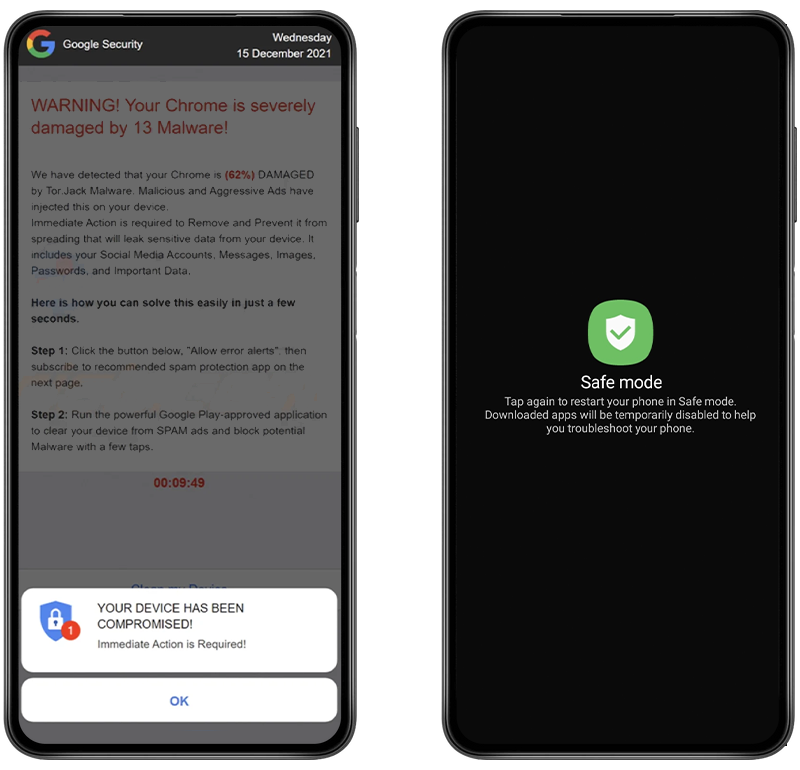
Fig 1. Example popup and enabling safe mode on Android.
3. Suspicious apps
Chances are you’ve got several apps installed on your phone — some of which you use daily, and others that you hardly open at all. If you think your phone is hacked, look out for suspicious apps that you don’t remember downloading.
Most spyware or malicious software requires an app to be installed onto the phone to collect your personal data. Hackers only need physical access to the phone for a couple of minutes to install spyware, and if you’re not vigilant about the apps on your phone you probably won’t even notice it.
It’s important to note that most Android phones come with some pre-installed apps and software. Although they won’t be apps you have installed, these apps aren’t malicious and don’t present a threat.

4. Unusually high data usage
If you’ve been experiencing exceptionally high data usage, it could be a sign that your device has something running in the background that is communicating via the Internet.
This could be as innocent as an app that is constantly updating or downloading something (i.e., a podcast app downloading new episodes). This is often the case and can be easily resolved.
However, if you’ve checked your apps and settings and you’re still experiencing high data usage, it could well be the case that your device is hacked and is communicating data back to a third party.
5. Google Play Protect has been disabled
Google Play Protect is a built-in virus and malware/spyware scanner for Android that will scan apps whenever they are installed onto a phone or tablet. A lot of the time a hacker will need to turn this off to gain access to the phone.
For security, we recommend that you always keep Google Play Protect on. You can check your Google Play Protect settings by doing the following:
- Open the Google Play Store app.
- Tap the profile icon at the top right of your screen.
- Tap Play Protect.
- If Play Protect is turned off, this could be a sign that someone has disabled it in order to install a malicious app.
Alternatively, the Certo Mobile Security app can also check this setting for you. Install the app here.

Fig 2. Enabling Play Protect on Android.
6. Unauthorized Charges
Keep an eye out for unauthorized charges on your phone bill or linked accounts. These could manifest as premium SMS charges or unknown purchases in the Google Play Store.
To investigate, regularly check your phone bill for unusual charges and review your purchase history in the Google Play Store under Account > Payments & subscriptions > Budget & history.
If you find transactions you didn’t authorize, immediately change your Google account password and consider enabling two-factor authentication for added security.
7. Your device is rooted
Rooting a device is a way of gaining access to deeper levels of authority over the device, and it is not usually allowed by the hardware or software developers.
Android rooting requires some basic technical knowledge. While it’s easy enough to do for someone with the right ability, it’s not something you can do to your own device by accident.
Hackers may seek to root your device to get easier access to certain functions on your cell phone and facilitate advanced spyware use.
If your device is rooted and it wasn’t you or someone you authorized that rooted it, your phone is likely hacked.
8. Developer options are enabled
Finding Developer options enabled on your device without your knowledge is a potential security concern. Developer options gives access to advanced settings and features used mainly for app development and debugging.
For example, with Developer options enabled, a hacker could install a malicious app onto your device by connecting it to their computer.
To check if it’s enabled, open the Settings app and search for “developer”. Alternatively, run a scan with our free app and we’ll tell you if it’s enabled as part of the System Adviser.

Fig 3. Checking if Developer Options is enabled on Android.
Is your Android phone hacked?
Find out now with Certo Mobile Security, the free app to help you stay in control of your privacy.
9. Antivirus finds a threat on your device
The quickest and easiest way to find out if your phone is hacked is to install a security or antivirus app like Certo Mobile Security. This free app will allow you to scan your device and find out for sure if there is malicious software installed on your Android system.
Fight back against cyber criminals with Certo for Android:
- Uncover hidden spyware and remove it quickly and easily.
- Run a security audit to find vulnerabilities on your device.
- Catch someone trying to access your phone when you leave it unattended.
- Find out if your accounts or passwords have been exposed in a data breach.
- See what apps on your phone can access your sensitive data.

Fig 4. Detecting a virus with Certo Mobile Security.
What Are the Risks of Phone Hacking?
If you think your phone has been hacked, you need to immediately take steps to remove the threat. Here are a few reasons why:
We depend on our phones
Most of us use our phones constantly, to do everything from messaging friends and family, accessing work emails, managing our finances, and more.
If your phone is hacked and the hacker changes your login credentials, you could be left suddenly unable to use your phone.
Hackers can remotely access your device from anywhere
If your Android phone has been compromised a hacker can track, monitor, and listen to calls on your device from anywhere in the world.
Everything on your device is at risk
If an Android phone is hacked, the attacker will have access to every piece of information on it. All of your personal data can be used for nefarious reasons, such as threatening to release private information to the financial gain of the hacker.
Software for phone hacking is inexpensive
Hackers use software that is incredibly cheap and accessible. For just $30, a hacker can get all the tools they need to exploit multiple devices and automatically retrieve whatever personal information they can find.
Phone hacking is relatively easy
If someone has the knowledge and is inclined to do so, hacking isn’t complicated. This means that almost anyone can be a hacker if they want to, such as partners, exes, family members, or even employers.
How to Protect Your Android Phone from Hackers
Although phone hacking represents a serious threat to your privacy, there are a few simple actions you can take to reduce the risk of it happening to you.
1. Install Certo Mobile Security
Certo keeps your Android device safe. This spyware detection app can find hidden spyware on any Android phone. Certo not only checks for malicious software, but also checks that the settings on your device are optimized for highest security. Find out more about the Certo Mobile Security App here.
Free security for all
Certo Mobile Security crushes spyware, stops intruders and keeps you safe online.
2. Use a virtual private network (VPN)
Virtual private networks encrypt all of the data that you share online so that no one is able to gain access. Whether it’s your social media logins, passwords, or browsing history, VPNs make it much harder for hackers to access your private information. Make sure you research different VPN providers carefully before signing up to one that is safe and secure.
3. Enable two-factor authentication
Two-factor authentication is an effective way of protecting your phone from hackers. It works by requesting two different types of authentication when you log in to an online account — for example, your Google account or social media accounts.
To log in, you might be required to enter your email address and password, as well as a verification code or a fingerprint ID.
The extra information required makes it much more difficult for hackers to gain access to your personal data.
Key Takeaways
It can be difficult to tell whether your Android phone has been hacked. Spyware and malicious apps can easily be hidden on your phone, leaving you vulnerable to attack.
Luckily, there are a few things you can do to reduce the risk and block hackers from your phone.
- Install Certo Mobile Security to scan your Android device for spyware and quickly remove threats.
- Use a strong passcode and biometrics on your device to stop unauthorized access.
- Ensure your operating system and apps are kept up-to-date so you always have the latest security patches.
- Use two-factor authentication for your online accounts to make it harder for hackers to gain access.
- Never share your passwords with anyone, and change them regularly to reduce the risk of your accounts becoming compromised.
Frequently Asked Questions (FAQs)
Is there a code to check if my Android phone is hacked?
For Android phones, there are useful USSD codes to check for signs of potential hacking: *#21# reveals any call or message redirections, *#06# displays the phone’s unique IMEI number to verify its legitimacy, and *#33# checks if any call barring has been activated without your knowledge.
While these codes help in identifying unusual settings, they don’t directly confirm if a phone is hacked. They should be part of a broader security approach including regular updates and vigilant app management.
What are the signs of a hacked Android phone?
The most telling signs of a hacked Android phone include, unexplained data usage, rapid battery drain, unusual apps and Google Play Protect being disabled.
These signs, along with antivirus alerts, suggest unauthorized access to your device, possibly due to malicious software. Regularly check and maintain security features to safeguard your phone.
What is the first thing you do when you get hacked?
If your phone has been hacked, immediately disconnect it from the internet by turning off Wi-Fi, mobile data, and Bluetooth. Change your critical passwords, especially for accounts linked to your phone. Use a trusted antivirus app to scan and remove any malware. Update your phone’s software to fix security gaps.
If problems persist, consider a factory reset, but back up your data first. Keep an eye on your accounts for any unusual activity and inform relevant services about the breach.