News

Apple Alerts iPhone Users Globally to Mercenary Spyware Attacks
Apple has issued warnings to iPhone users across 92 countries regarding a sophisticated "mercenary spyware attack" aimed at remotely...
News

Apple has issued warnings to iPhone users across 92 countries regarding a sophisticated "mercenary spyware attack" aimed at remotely...
Guides

Smartphones have become central to our lives, storing everything from personal photos and conversations to sensitive financial data. This...
Guides

In today’s connected world, our smartphones are central to our daily lives, functioning not just as communication tools but also as...
News

The term "Juice Jacking" might sound intriguing, but it represents a real cybersecurity threat according to the Federal Communications...
Expertise

In an age of digital espionage and data breaches, it's no surprise that more and more people are concerned about the privacy of their...
Expertise

Imagine finding out that someone has been spying on you at home, in your car, or on vacation—it’s sure to send shivers down your spine.
News

In the ever-evolving landscape of cyber threats, a new menace has emerged in the form of a sophisticated phishing-as-a-service (PhaaS) named...
News
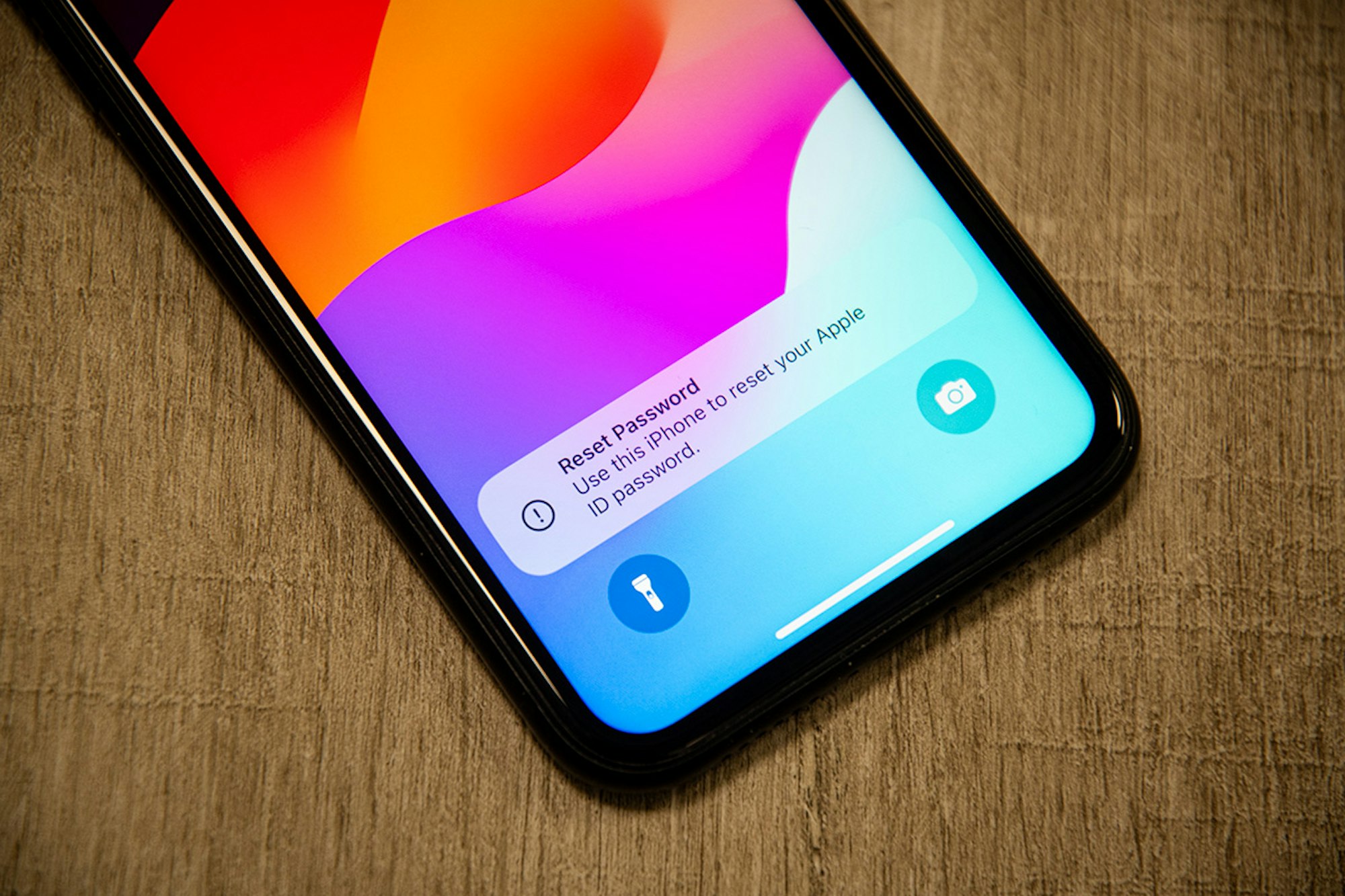
In the intricate world of cybersecurity, where vigilance is paramount, a new phishing campaign targeting Apple users has emerged, leveraging...
Guides

If someone you know gains physical access to your phone, they can spy on your text messages, videos, photos, and other sensitive...