I Am Having My Phone Tracked. How Can I Stop It?

Updated:

In today’s world, our mobile devices serve as the digital epicenter of our lives, rendering them vulnerable to potential tracking and hacking. This ever-present concern extends beyond merely tracking our physical whereabouts; it includes monitoring our conversations, browsing habits, login credentials, and even our cherished photos and videos.
As we increasingly rely on a single device, the importance of robust mobile security cannot be overstated.
In this article, we’ll delve into the intricacies of mobile hacking, exploring the methods used by cybercriminals to track your location and activities. We’ll guide you in identifying any signs of intrusion, and most importantly, provide you with actionable steps to prevent and mitigate phone tracking should you uncover evidence of hacking on your device.
Stop phone tracking now
Certo's award-winning spyware detection tools for iPhone and Android are trusted by millions worldwide.
How Can a Phone Be Tracked?
There are many different ways a phone could be tracked, and some people believe it’s as simple as knowing someone else’s phone number. However, we’ve shown this to be false. The most significant threat to your mobile security comes from something known as spyware.
Spyware: The Invisible Threat
Spyware is malicious software that hackers use to collect private personal information from your phone and send it back to them so they can view it remotely. It acts like a sponge, soaking up as much information about you as it possibly can.
This software is typically physically installed onto your device and can be purchased commercially for as little as $30. It is incredibly cheap and simple to use, meaning this type of hacking isn’t restricted to computer experts; anyone can do it.
Both Android (Samsung, LG, Huawei, etc.) and iOS (Apple) have their own protections in place to guard against spyware. However, it’s not impossible for hackers to completely bypass these protections by modifying the device’s software (called “rooting” on Android or “jailbreaking” on iOS).
This process gives them deeper control over the device, allowing them to install spyware that collects your information while hiding it completely from view.
Misusing Parental Tracking Apps
Another method involves using parental or family tracking apps (available from the Play Store or App Store) initially designed for parents to help monitor their children. These apps are often misused and installed onto the devices of unsuspecting victims to track their location.
This tactic is commonly used (but not restricted to) in marital relationships or even domestic abuse cases.
Cloud Attacks
A third way someone can become a victim of hacking is via the Cloud account linked to their phone. If a hacker acquires login details for their iCloud or Google account, it could be entirely possible for them to access any backed-up data from the phone, including contacts, messages, images/videos, or even a complete copy of the phone in some cases.
Exploiting Legitimate Apps for Tracking
A final tactic often seen is the use of legitimate apps (such as Google Maps) to track someone’s location. This can often be achieved using the app’s built-in location-sharing feature. You can read more information about this type of hack here.
How to Tell if Your Phone Is Tracked
Here is a list of symptoms you should keep an eye out for if you are worried that your phone is being tracked:
- Is your phone Jailbroken or rooted?
- Are there any apps on your phone that you don’t recognize?
- Does your phone get hot after a short time?
- Are you experiencing unusually high data usage?
- Does your battery run out faster?
- Are you receiving unusual messages or emails (or have you in the past?)
- Does someone close to you know private things about you that you’ve not mentioned anywhere other than on your phone?
The quickest and most thorough way to determine if your phone is being tracked is to run a spyware scan with a trusted application for Android or iPhone.
Android
Certo Mobile Security is an app that can scan your entire device and check for any malware or security vulnerabilities. It will also check for apps that are tracking your location and allow you to manage the permissions for those apps, along with apps that are able to access your microphone, cameras and files. Finally, it will check that your device is not rooted, which is often required for the most invasive spyware.
Certo Mobile Security is completely ad-free and provides full anti-spyware functionality at zero cost. A premium upgrade is available which enables automatic scanning so you can ‘set it and forget it’ safe in the knowledge that your device will always be protected. Find out more about Certo Mobile Security for Android here.

iPhone
Due to the way the iOS operating system works, spyware detection for iPhones is a little trickier than on Android, and a different approach is therefore required.
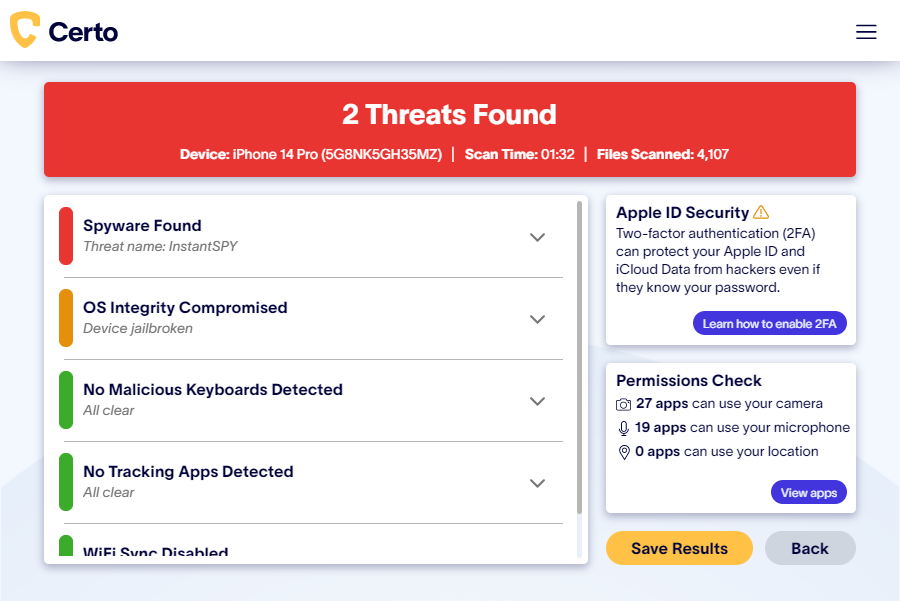
Certo AntiSpy is a tool designed to scan your iOS device via a connected computer. The software can quickly check your iPhone or iPad for data-stealing spyware installed on the device. It can also check for any location tracking apps, including those legitimately available on the App Store. Finally, it will check for any signs of jailbreaking – a method that hackers often use to bypass Apple’s in-built security measures which allows them to see all of your personal data, track your location and listen in on phone calls.
Get your privacy back
Download one of Certo's award-winning apps today and uncover spyware and other cyber threats on your phone.
How to Stop Your Phone Being Tracked
Once you’ve checked your device for spyware or tracking software, the next thing to do is remove it. We’ve split this section into Android and iOS because the hacking methods and steps to reverse them are different for each platform.
Android
- If you’ve downloaded and installed the free Certo Mobile Security app, then you will be able to perform a scan that will reveal any spyware installed on the device. Once the scan has been completed and if spyware has been detected you will then be prompted to remove it with a single tap of a button.
- If you’re using any cloud services to backup your Android device (such as Google Drive) then you must make sure that you have enabled two-factor authentication. Two-factor authentication is a way of ensuring that even if a hacker has somehow discovered your login details for your account, they can’t access that account without a confirmation code sent to your phone via SMS text message. This prevents hackers from viewing all of the backed-up information or downloading a clone of your device.
- For so-called ‘legitimate’ tracking apps that are readily available on the Google Play Store, you should start by simply checking all of the apps on your phone. Investigate any that you don’t recognize and simply remove them if you don’t want them. Make sure to check app folders as well, as this is a way that some people try to hide this type of app. Alternatively, you can use Certo Mobile Security to quickly view all of the installed apps on your device that are tracking your location.
iPhone
- If Certo AntiSpy finds spyware or a tracking app on your device, all you need to do is click the Remove button. The software will either remove the threat for you or provide you with easy-to-follow removal steps, specific to the threat identified on your device.
- If you’re worried about your iCloud account being hacked, then the best thing to do here is to enable two-factor authentication. This will prevent anyone from accessing your account even if they have your password.
- For any ‘family/parental’ tracking apps (legitimately found on the App Store) then the first option is to just search your device and manually remove any apps with the location permission that you don’t trust, not forgetting to check app folders as hackers will sometimes hide these apps from plain sight using this method. Alternatively, Certo AntiSpy can not only tell you about fully-fledged tracking software, but also about the types of legitimate apps that are commonly misused and pose a security threat.
We hope this article has helped you learn more about the different types of phone tracking available to hackers. You’ll now be better equipped to tell if you’ve been a victim and armed with the knowledge you’ll need best to protect yourself.
With the ever growing amount of sensitive and private data on our phones, it’s more important than ever to ensure they’re protected.
Cover Image by rawpixel.com on Freepik