How to Stop Someone from Spying on My Cell Phone

Updated:

Did you know around 60% of all cyberattacks in the world happen on cell phones? In fact, around 80% of these hacks happen via apps on mobile devices.
With this in mind, you may want to know how to stop someone from spying on your cell phone.
You’re not the only person concerned about this. Many people are worried about spy software being installed on their phones, as it is becoming increasingly easier for almost anyone to hack your phone if they have the right tools.
That’s where we come in. We’ve put together an easy, step-by-step guide to help you protect yourself and your private data and prevent someone from spying on your phone. Let’s get started.
Stop phone spying the easy way
Quickly and easily run a spyware scan on your cell phone today with one of Certo's award-winning apps.
Signs Someone Is Spying On Your Phone
Before we tell you more about how you can get complete protection from phone spying, let’s take a quick look at some telltale signs that your phone may have spy software installed.
- Your battery life runs down faster than usual. Tracking your GPS location and recording phone calls uses a lot of battery life.
- Your phone is heating up. All the extra processes that are running on your cell phone can cause it to get hotter than usual.
- Your cellular data usage is unusually high. Sending your private information back to the hacker can lead to high data usage.
- You notice distorted noises on phone calls. This may be a sign your phone calls are being recorded.
- Your phone takes a long time to shut down. If your device is sending large amounts of data to a hacker, these tasks will need to finish before your device will switch off.
- You’re receiving odd text messages that include unrecognized links. This can mean a hacker is trying to access your sensitive information.
How to Stop Someone from Spying On Your Mobile Device
Now that you know what may happen to your phone if a spy app has been installed, let’s examine some of the things you can do to stop someone from spying on your cell phone.
1. Change your passcode
It may surprise you, but phone spying is far more likely to be carried out by the people closest to you rather than some anonymous hacker.
In many cases, these are the people that would know your passcode, which is how they would gain access to your Android or iOS device.
Telling someone your PIN number, security pattern, or password leaves you vulnerable to cell phone spying.
Changing your passcode regularly will prevent anyone from looking through your phone. This also makes it harder for someone to install spyware that secretly accesses your sensitive information like your passwords, chat history, email, images, and videos.
Ensure you choose a strong passcode of at least six characters, and don’t choose anything that would be easy for someone to guess, like your birthday.
Additionally, make use of biometric features like Face ID or Touch ID on an iOS device, which can add an extra layer of protection as no one other than you can unlock your phone.
2. Restart your phone
Many spy apps rely on phones being left switched on for long periods of time. In many cases, simply by restarting your device you can stop someone from spying on your cell phone.
If you think about it, our cell phones are on most of the time, and we don’t turn them off regularly. However, restarting your phone from time to time can force any spyware on your phone to stop working.
3. Update your device and apps
Another simple measure you can take is to do a software update as often as possible to ensure you have the latest software on your phone.
Cell phone manufacturers regularly release updates to help protect against newly developed spy software and other hacking methods.
Some mobile device hacking methods rely on an older version of the manufacturer’s software being installed to bypass the built-in security features.
The same goes for any default or pre-installed apps—ensure you keep them up to date.
For iOS devices, an added benefit of keeping the device up-to-date is that the act of installing new software updates will ‘break’ most spy apps and stop them from collecting any further sensitive data from your device.
4. Scan your device for spyware apps
By far the best thing you can do if you are worried about someone spying on your phone is to scan your device. A scan will highlight any spying software that has been installed onto your cell phone, along with any areas of weakness in your phone’s security.
You can use our award-winning anti-spyware tools, which are available for iOS and Android.
Award-winning spyware detection
Certo's industry-leading spyware detection tools for iPhone and Android are trusted by millions worldwide.
5. Check If Google Maps or Apple Find My is sharing your phone’s location
Most people don’t realize that a snooper doesn’t necessarily need to install spyware to track your location. Pre-installed apps, such as Google Maps and Apple’s Find My, have the ability to share your GPS location with another phone with just the tap of a button.
You can check if location sharing is turned on in either of these apps as follows:
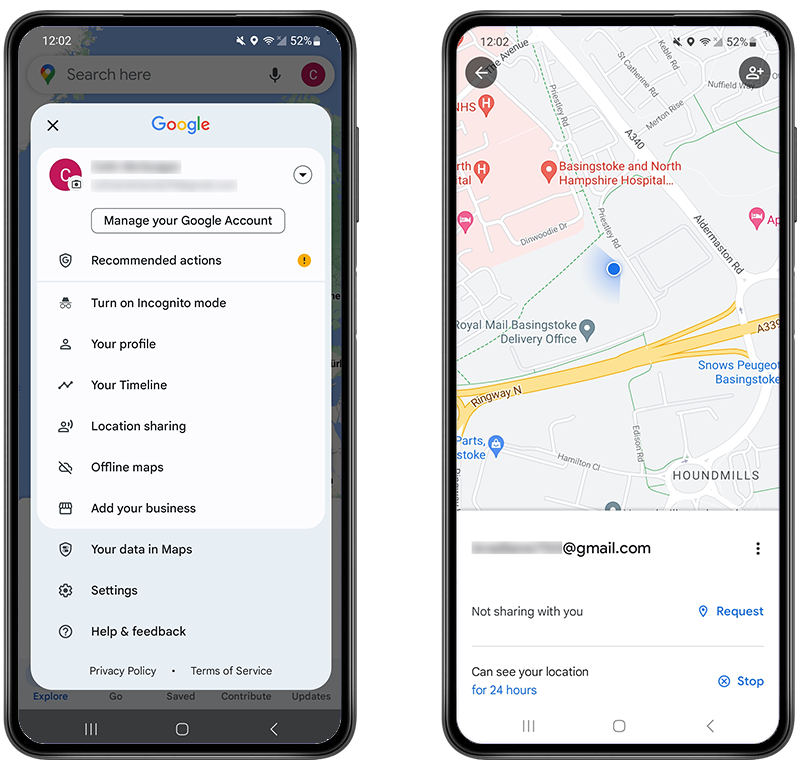
How to stop sharing your location in Google Maps:
- On your device, open the Google Maps app.
- Tap the Account Circle in the top right.
- Tap Location Sharing.
- Remove any accounts you are sharing your location with.
How to stop sharing your phone’s location in Find My (iPhone/iPad):
- On your device, open the Find My app.
- Tap Me.
- Turn off Share My Location.

These are just two examples of default apps that allow location sharing. However, you should be vigilant and check your device for any app that could allow location sharing to a third party without your knowledge.
6. Check the logged-in account in the Google Chrome browser app
Yet another trick that some snoopers use is changing the account used for the Google Chrome browser app. If they change it to an account they control, this will allow them to track all your internet browsing history, along with any usernames and passwords that you save in the app.
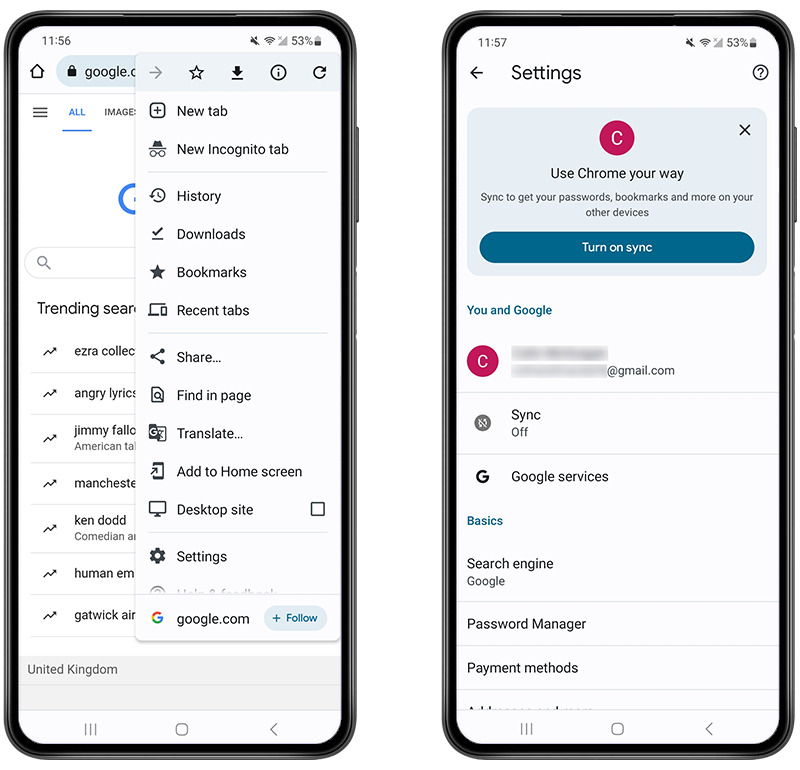
To check your logged-in account:
- Open the Google Chrome browser app.
- Tap the three dots in the top right corner.
- Tap Settings.
- Under ‘You and Google’, you should be able to see the email address that’s logged in.
- If it’s incorrect, tap on the email address, then tap Sign out.
- After you’ve done this, you should change the passwords for your important accounts.
7. Check your device for apps that are using your location, microphone, or camera
Many spy apps will collect sensitive data from your device and give the hacker access to your GPS location, microphone, and even your camera.
Certo AntiSpy (iOS) and Certo Mobile Security (Android) will tell you exactly which apps are using these three features and will allow you to easily spot any suspicious-looking apps that could be spying on you.
If you want to do this manually, you can review the privacy and permission options in the Settings app on most phones.
8. Use a VPN
A virtual private network (VPN) will encrypt all the traffic between your phone and any online resource it’s accessing, whether it be your email account, social media apps, or a website you’re visiting.
Use a reputable VPN like NordVPN with your device to ensure that no one can spy on your online activity.
Although a VPN doesn’t automatically give you complete protection, it should be part of an overall security plan.
9. Use two-factor authentication
Instead of hacking your physical Apple or Android device, hackers will sometimes target the accounts associated with it.
For example, unauthorized access to an Apple iCloud account might give a hacker the ability to download data synced from your iPhone. E.g. photos, contacts, messages etc.
This would give them access to all kinds of private phone data. The same goes for Google accounts.
To prevent this from happening, tech companies offer a feature called two-factor authentication (2FA). Put simply, this means that to log into your account, a hacker would need a special code that is sent to you via text message in addition to your password.
Even if they know your username and password and were trying to log in from another device, they wouldn’t be able to do so because they wouldn’t have your unique code.
To learn how to enable two-factor authentication on Apple iOS click here, or for Android devices using Google click here.
10. Factory reset your phone
It’s worth noting that this is the last resort and should really only be used if nothing else works.
A factory reset will erase all data from your phone and return it to the state it was in when you first opened the box.
This will wipe all your personal data, so make sure you back up any contacts, photos, videos, and data that you want to keep.
- Check out this article to reset your Android device.
- Read this article to reset your Apple iOS device.
Wrapping Up: How to Stop Someone Spying On Your Cell Phone
We hope this guide gives you some insight into how to stop someone from spying on your cell phone and how to secure your device.
If you are concerned that your phone may have been hacked because of the signs listed above, then run a quick scan with one of Certo’s award-winning anti-spyware tools for iPhone or Android.
If you suspect that the person who is spying on your cell phone is someone you know, think carefully before confronting them, and never do anything that could put you in danger. The Coalition Against Stalkerware has some great resources to help victims of cyberstalking that you may find useful.
By keeping an eye out for the common signs of spyware and following our additional security tips, you should be able to keep your cell phone safe and secure.
Frequently Asked Questions (FAQs)
Is there a way to tell if your phone is being spied on?
Yes, there are indicators that your phone might be monitored. Unexpected battery drain, strange noises during calls, and unexplained data usage spikes can be signs, but they can also result from other issues. Installing a reputable security app can help detect spyware.
Can I block my phone from being spied on?
To stop someone from spying on your mobile device, change your passcode and utilize biometric features like Face ID or Touch ID. Restart your phone, update your device and apps to the latest versions, and perform a scan for spyware using a reliable tool. Additionally, check for location sharing settings in apps like Google Maps and Apple’s Find My, and as a last resort, consider a factory reset after backing up essential data.
How do I protect my phone from being tracked?
To prevent tracking, regularly review and limit app permissions, especially those requesting location access. Use encrypted communication apps, disable unnecessary location services, and consider using a VPN. Remember, though, some tracking, like by mobile carriers, can’t be completely stopped.
How can I make sure my online activities are secure?
Use a reputable VPN to encrypt online traffic, enable two-factor authentication on your accounts, and be cautious about the accounts you’re logged into, especially on browsers and apps.