Can Someone Hack Your iPhone Remotely?

By Simon Lewis
Updated:

It’s a question we’re asked a lot by iPhone users; whether they should be worried about someone potentially hacking their iPhone remotely. In this article, we examine the facts about what is actually possible, as well as give out some handy advice that will help protect you in the future.
So, if you’re one of the people asking yourself, “can someone hack my iPhone remotely?”, then you should read on…
Stop remote hackers
Quickly and easily check your iPhone for hackers today with the award-winning Certo AntiSpy.
Is it possible to hack an iPhone remotely?
It might surprise you, but yes, it is technically possible to remotely hack an iOS device. Spyware such as Pegasus continues to gain attention due to its ability to be installed without physical access to the victim’s iPhone, sometimes just by way of a missed FaceTime call or other zero-click exploits.
On the bright side; however, it will almost certainly never happen to you. Here’s why:
1. Remote-hacking software is exceptionally expensive.
There have been cases of hackers gaining access to an iOS device remotely (for example Pegasus and the WhatsApp hack in 2019), but the exploits required to hack a device remotely are incredibly specialized and expensive, often in excess of $100,000.
That means in order to make it worth a hacker spending that much money – you would have to be a very high-value target. The good news is that, well, most of us aren’t.
The reality is, most of us really don’t need to worry about these sophisticated cyber attacks. Not only is it rare for most hackers to be able to afford this type of software, but the developers that make it also only sell it to governments and a select list of clients.
Most hackers are far more likely to go after more accessible and less expensive methods of spying on someone’s device.
2. Apple patch any vulnerabilities almost as soon as they find them.
Apple takes the security of their devices very seriously (they wouldn’t even let the FBI use their ‘backdoor’), so they are always assessing the potential risks to their software. As soon as they discover a vulnerability or a bug in their system – they fix it. They release an update, and every iPhone, iPad or iPod is suddenly protected from those security threats.
This is one of the benefits of using an iOS device compared to, for example, an Android device. Android’s operating system runs in various different builds across a range of different devices. This makes it hard for Google to roll out a big update that will patch security threats for every device, whereas, for Apple, it’s much more simple.

3. Some companies claim to offer remote-hacking of an iPhone, but it won’t work for most users.
The basic idea behind these services is that they allow an attacker to gain access to your iCloud account and extract data synced from your iPhone. If they do gain access, they have the ability to see things such as your messages, photos, call logs, internet history and anything else synced to your iCloud account.
However, as most people are using two-factor authentication with their Apple IDs, this means that the hacker would still need physical access to the device to disable two-factor, meaning that in most cases this attack is not truly remote.
This is one of the reasons why we tell our readers and customers that it’s important to enable two-factor authentication on all of their devices and online accounts wherever possible.
You can read more about this type of hack in this article.
What can you do to protect yourself?
Although the risk of being hacked remotely is quite low, as we’ve pointed out, it’s not impossible. So, here are a few extra steps you can take if this is something you are particularly worried about. These are also good general tips to follow if you’re concerned about your iPhone security in general:
1. Install Certo AntiSpy
Our revolutionary software is designed to help you stay ahead of painful security threats. We protect your device from the various methods that hackers use on a daily basis to attack and gain access to your personal data.
We ensure that your device remains protected and will help you manage any potential areas of risk. We can also detect if your device is, or has ever been, compromised in any way, recommending further steps of action in order to stay secure.
The main thing we offer, though, is peace of mind. We want you to feel safe that your device is secure, and your data is protected.
Award-winning spyware detection
Millions trust Certo to protect their mobile devices from hackers. Find out how Certo AntiSpy could help secure your iPhone.
2. Enable two-factor authentication
This one is pretty simple, and it’s something that everyone with an Apple ID should do. Two-factor authentication adds an extra layer of security and ensures that someone can’t access your iCloud account and device backups, even if they’ve worked out your password.
Click here to learn how to enable two-factor authentication for your Apple ID, or just follow along with the steps outlined below:
- Go to your Settings app.
- Tap your name, then Password & Security
- Tap Turn on two-factor authentication then tap Continue.
It’s worth noting that you may be asked to answer some security questions to access your Apple ID.

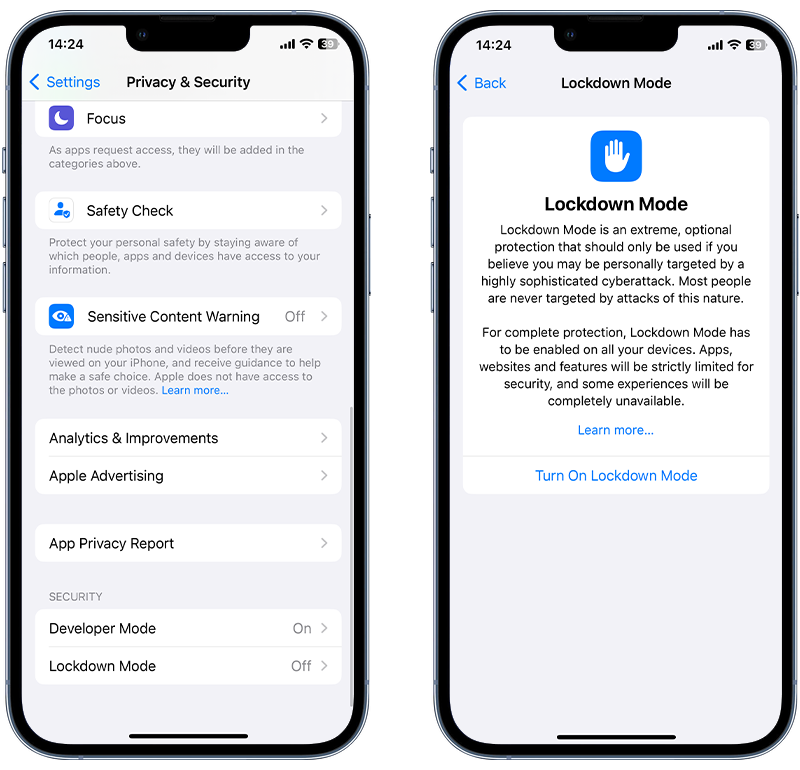
3. Enable Lockdown mode
Apple introduced Lockdown mode in iOS 16. This is an optional, extreme protection measure that can be turned on to help combat some targeted and sophisticated cyberattacks, such as Pegasus. As mentioned above, attacks of this nature are very rare and typically only used against high-profile targets.
When enabled, your device will function differently. Some apps, websites and features will be strictly limited for security and some experiences will be completely unavailable.
While this isn’t going to protect against all methods of hacking, it can be a way to further secure your device if you think you may be at risk.
Lockdown mode can be enabled as follows:
- Open the Settings app.
- Tap Privacy & Security.
- Under Security, tap Lockdown Mode and tap Turn On Lockdown Mode.
- Tap Turn On Lockdown Mode.
- Tap Turn On & Restart, then enter your device passcode.
Final thoughts
In conclusion, it is technically possible for someone to remotely hack an iPhone, but it is highly unlikely to happen to most users. The expensive software and specialized techniques required for remote hacking make it a viable option only for high-value targets.
Additionally, Apple’s swift response to patch vulnerabilities and the use of two-factor authentication make it even harder for hackers to access personal information. While the risk may be low, it is still important to take measures to protect oneself, such as using anti-spy software, keeping the device updated, and being cautious of suspicious apps and links.
Overall, iPhone users can rest assured that their device is secure and take steps to ensure their privacy and safety.