Apple ID Hacked – What Can I Do?

Updated:

Illegal hacking and spyware use are constantly rising around the world. As organizations like the Coalition Against Stalkerware work to fight this global problem, one of the main weapons we have in our arsenal is education.
If you have ever wondered if your Apple ID has been hacked, then read on to discover the telltale signs and what to do if you suspect that someone else is accessing your information without your permission.
It’s important to remember that Apple ID hacking isn’t the only way that someone could be snooping on your phone. There are many spyware providers that offer apps that can hack and monitor an iPhone, often stealing much more data than available through an Apple ID.
If you suspect that your iPhone has been hacked in any way, you can use a dedicated spyware detection tool, like Certo AntiSpy, to find out for sure and fix your device.
Hacked? We’re here to help.
Certo’s free app helps you protect your Apple ID and iPhone from cyber attacks.
Has Your Apple ID Been Hacked?
How to tell if your Apple ID has been hacked
Apple ID hacking is sneaky because:
- It’s hard to notice.
- They can track many of your activities and access account information without your knowledge.
- They don’t need to install anything on your phone to do it.
Because of this, you won’t notice any of the usual danger signs of iPhone spyware like your data running out fast or your battery dying quickly.
Here are some quick checks you can do to help identify if your Apple ID has been hacked:
⚠️ Unexpected activity: Do you see apps or purchases you didn’t make? This unexpected activity could be a sign that your Apple ID has been compromised.
⚠️ Password problems: Someone might’ve changed your password if it doesn’t work or if you get suspicious messages like a password reset email or verification code you didn’t ask for.
⚠️ Account changes: Getting notifications about changes you didn’t make, such as a new email or phone number? That’s suspicious.
⚠️ Security alerts: If Apple tells you about sign-ins from new places or devices you don’t know, be careful.
⚠️ Strange devices: If you see devices linked to your Apple ID that you don’t recognize, that’s a red flag.
Immediate steps to fix an Apple ID hack
If you believe your Apple ID has been compromised, you should take immediate steps to regain control and protect your information.
To protect your Apple ID and other accounts, take these critical steps:
1. Try to log in to your Apple ID account
The first thing a hacker will do is change passwords to lock out account owners. If you notice suspicious activity, immediately try to regain access. Here’s what you should do first:
- Try logging in to your Apple ID at either appleid.apple.com or icloud.com.
- If you can successfully login to your account. Proceed to Step 2 to change your password.
- If you are unable to login to your account, visit iforgot.apple.com to try and reset your password and recover your account.
2. Change your Apple ID password and ensure it is strong
If you can access your account, immediately change your Apple ID password on your Apple device or browser. Here’s what you need to do:
Using a web browser:
- Go to the Apple ID account page and log into your account.
- In the Sign-In and Security section, click Password.
- Follow the on-screen instructions to reset your password. Depending on your account settings, you might be given different options, like answering security questions, getting an email to reset the password, or using two-factor authentication.
Using an Apple device:
- Go to the Settings app.
- Tap on your name at the top, which opens the Apple ID screen.
- Tap on Sign-In & Security.
- Tap Change Password. If you’re signed in to iCloud and have a passcode set up for your device, you’ll be prompted to enter it.
- Enter your new password and confirm it.
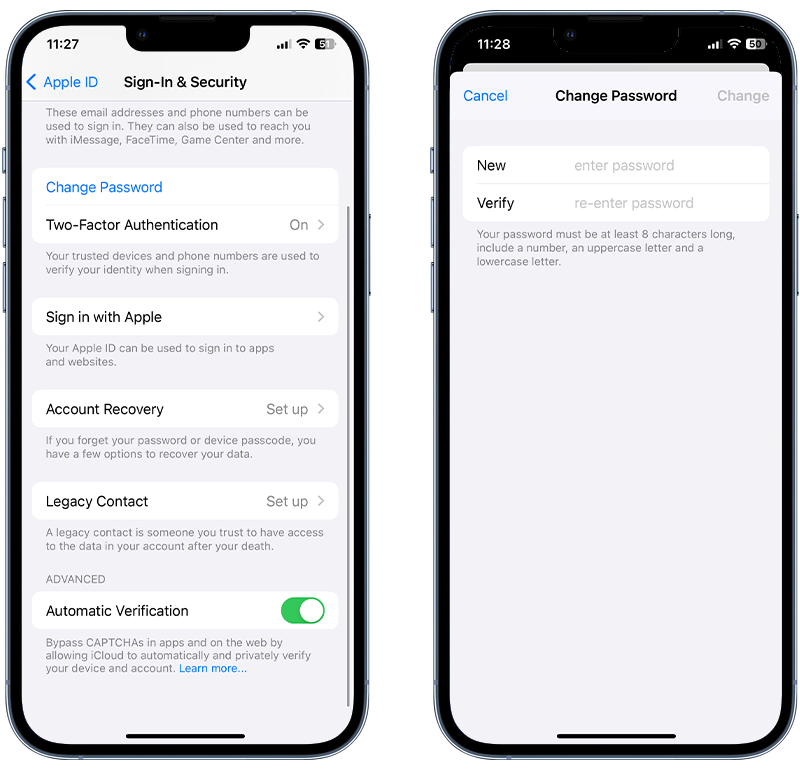
Fig 1. Changing Apple ID password on an iPhone.
It’s important to note that your Apple ID password should differ from all other online accounts. This is standard good practice to maximize your Apple ID security.
Using unique passwords for each website will ensure that your other accounts remain protected in the event that one of them is a victim of a data breach.
💡 Pro-tip: Here’s how to create strong passwords
When you create a password, aim for one that's both complex and memorable. Here's a method that works well:
Use a phrase: Start with a memorable sentence or phrase. For example: "My cat Whiskers loves climbing trees!"
Take initials: Use the first letter of each word. From our example, this gives: "McWlct"
Mix cases: Use both uppercase and lowercase letters.
Integrate numbers and symbols: Replace some letters with numbers or symbols. For instance, "a" can become "@," "l" can be "1", "s" can be "$," etc. So, "McWlct" might turn into "McW1c$t".
Extend length: Longer passwords are generally stronger. Aim for at least 12 characters.
Avoid personal information: Steer clear of easily accessible details like birthdates, anniversaries, or names.
Change it up: Don’t use the same password across multiple sites. If one website is compromised, all your accounts could be at risk. A password manager can help with this. We recommend NordPass.
3. Enable two-factor authentication with your Apple ID
Now is a good time if you haven’t set up two-factor authentication yet. It adds an extra layer of security because it not only requires your password, but access to one of your trusted devices or phone numbers, too.
Enabling two-factor authentication means that even if someone discovers your password, they cannot access your account. Any attempts to log in with your password will trigger a unique code sent to your trusted device. This protects you and alerts you if any attempts to log in are made.
Here is how to enable 2FA:
- Go to Settings and tap on your name at the top to access Apple ID settings.
- Tap on Sign in & Security.
- Tap on Turn on Two-Factor Authentication.
- Tap Continue.
- Next, you’ll be asked to provide a phone number to receive a verification code via SMS or a phone call. This number will be used whenever you need to verify your identity through 2FA.
- Choose to receive the code by text or call, then tap Next.
- Enter the verification code you received to verify your phone number and continue with the setup.
4. Check your Apple ID device list and remove unrecognized devices
Another critical step to regain control after a potential breach of your Apple ID is to review the devices linked to your account.
Hackers often add their devices to your account to access your data and make unauthorized changes.
To review your Apple ID device list and see which devices are associated with your Apple ID, follow these steps:
- Open the Settings app.
- Tap on your name at the top to access Apple ID settings.
- Scroll down to the list of Apple ID devices associated with your Apple ID.
- Tap on any device name to see more details, like the device model, OS version, and serial number. If needed, you can also remove a device from this list.
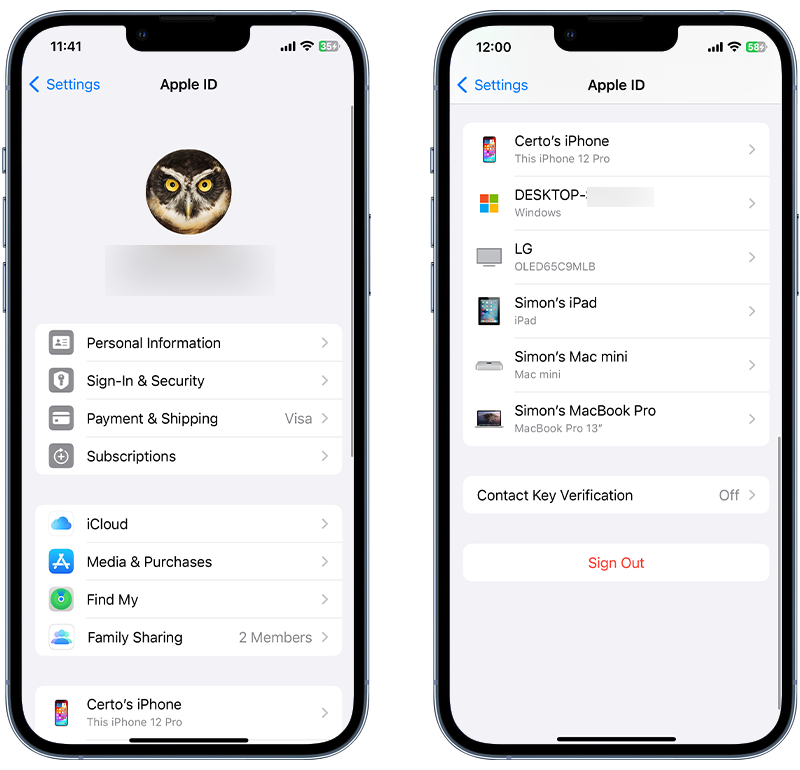
Fig 2. Checking devices logged into your Apple ID.
5. Contact Apple support
If you’re still worried that your Apple account or device has been hacked, it’s a good idea to talk to Apple Support. They have experts ready to help with account recovery.
They can check your account’s safety, guide you on fixing any issues, and give tips to keep things secure in the future. It’s always better to play it safe and get professional advice when in doubt.
Steps to protect your Apple ID in the future
1. Turn on Advanced Data Protection
In iOS 16, Apple added the option to enable Advanced Data Protection for your data stored in iCloud. This feature encrypts your data and this means it can only ever be accessed by one of your trusted devices.
Here is how to set up Advanced Data Protection on Apple devices:
- Open the Settings app.
- Tap your name, then tap iCloud.
- Scroll down, tap Advanced Data Protection, then tap Turn on Advanced Data Protection.
- Follow the on-screen instructions to review your recovery methods and enable advanced data protection.
You can learn more about this feature here.
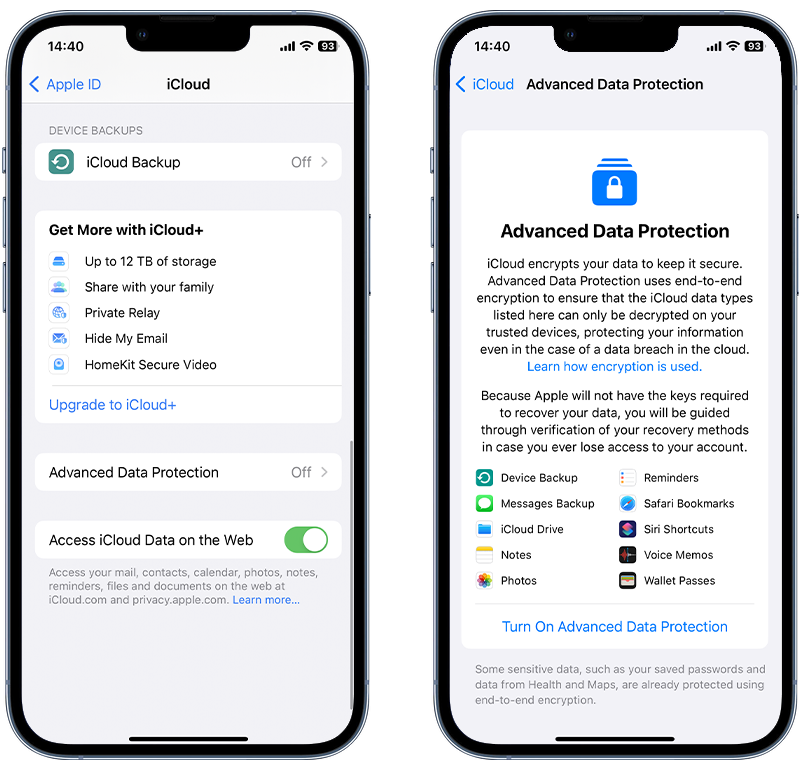
Fig 3. Enabling Advanced Data Protection for iCloud.
2. Only sync what’s necessary
Syncing data to iCloud can be handy, as it allows you to access your information across multiple devices. However, this also means that a copy of your personal data and account details is stored in a location beyond your direct control.
For this reason, be selective about what you sync and only choose essential information.
3. Consider local backups
Similar to the above, if you backup your device to iCloud, then a complete copy of all your data is stored online and it could potentially be accessed by anyone who gains access to your account.
It’s worth considering backing up to your computer instead, which gives you more control about where your data is stored. These backups can be encrypted for extra security.
Understanding Apple ID Vulnerabilities

Image by Freepik
We’ve covered what to do right after you think your Apple ID has been hacked. But there’s more to know.
You can better protect yourself by understanding how hacking works and the signs to watch out for.
So, let’s dive into what happens when someone tries to hack your Apple ID and how you can stay ahead of them and keep your account secure.
How can someone gain access to your Apple ID?
Simply put, the hacker would have to know your Apple ID username and password and there are a variety of ways that they could find this information:
❌ Phishing attack
A phishing attack happens when you receive a text or email that persuades you to click on a malicious link and prompts you to enter your credentials.
There are several ways that these attacks give themselves away, and you can read our guide to spotting them here.
❌ Hacking another device
Suppose a hacker has gained access to another device of yours, for example, a computer, tablet, or other phone. In that case, they can use that to log keystrokes and steal your login data for your Apple ID and any additional login information you may use on that device.
❌ You are the victim of a data breach
Data breaches are another alarming factor that contributes to the rise in malware attacks, particularly ransomware that targets large organizations.
If you use the same login information across multiple accounts, there is a much higher chance that your data will be leaked online.
In 2023, companies and organizations that suffered the most significant data breaches include Sony, Microsoft, and T-Mobile. You can read the complete list here.
❌ You know your hacker
A particularly alarming concern arises if you have ever shared your credentials with someone or let them have unsupervised access to your phone. In such cases, there’s a risk that this person could misuse your information to hack into your Apple ID.
What happens when someone hacks your Apple ID?
What can a hacker do once they’ve obtained your Apple ID login credentials?
Many spyware providers offer a service that steals data from iCloud by using the victim’s Apple ID and password.
Most iOS spyware relies on your phone being jailbroken to work, which requires access to the device and a little technical knowledge.
Having an alternative cloud-based solution (often called a ‘no-jailbreak’ solution) gives hackers a greater breadth of options when they are trying to stalk you or steal your personal information.
So how does it work? The hacker would give your Apple ID and password to the spyware provider, who would then use it to access your account and download a copy of all the data you’ve synced with iCloud from your iPhone.
This data is then formatted for the hacker into an easy-to-read report, which will be updated every time your phone syncs to iCloud. The data they could steal from a hacked iCloud account could include:
- iMessages
- Contacts
- Calendar entries
- Photos and videos
- Notes
- Your GPS location in real-time
- Emails, if you have an iCloud address
What else could a hacker do with your Apple account?
Another option for hackers would be to restore the most recent backup of your iPhone to a device they control.
This would allow them to see a full copy of your phone at the time of backup, including messages, photos, contacts, and any other data in the device backup stored in iCloud.
What are the limitations of hacking an Apple ID? It gives someone access to a lot of information about you and your phone; however, it doesn’t allow them to listen in to your calls or turn on your camera or microphone to spy on you in real time.
This requires a more advanced spy app to be installed directly on the device. If this is something that you are worried about, check out Certo AntiSpy to find and remove spyware on your iPhone.
Award-winning spyware detection
Combat spyware and other cyber threats with Certo AntiSpy, the world's leading anti-spyware tool for iPhones.
Wrapping Up
Safeguarding your Apple ID is crucial in an era where digital security threats are ever-evolving. The steps and strategies outlined in this guide are not just reactive measures for when you suspect a hack, but they are also proactive approaches to fortify your Apple ID against potential threats. Remember, your digital safety hinges on the strength of your security practices.
Regularly updating your security settings, using unique and strong passwords, enabling two-factor authentication, and being vigilant about the devices connected to your Apple ID are fundamental practices.
Furthermore, consider using dedicated tools like Certo AntiSpy for an added layer of protection against hacking and cyber attacks. These tools are designed to detect and neutralize threats that conventional methods might miss, ensuring your peace of mind.
Frequently Asked Questions (FAQs)
How can I tell if someone has signed in to my Apple ID?
If someone attempts to sign in to your Apple ID, Apple will alert you by displaying a message on any of your devices that’s signed in to that Apple ID. You may also get an email with details of any unrecognized login attempts.
To check devices that are signed in to your account, follow the instructions here.
Can someone read my WhatsApp messages if they have my Apple ID?
While WhatsApp chats can be backed up to iCloud, someone can’t view this information without access to your Apple ID. The messages can only be downloaded by a device with your phone number.
For an extra layer of security, turn on end-to-end encryption for your WhatsApp backups in the app’s Settings.
What can someone do if they have my Apple ID?
If someone gains unauthorized access to your Apple ID there are several ways your data could be compromised:
- If you sync data from your iPhone to iCloud, a hacker can view this data.
- If you have an @icloud.com email address, they may be able to send and receive emails via your account.
- If FindMy is enabled, they could track your location.
- If you backup your iPhone to iCloud, they could restore the entire backup to their device.